Articles
To read the articles in this section, simply click on the article title or read button on the far right (if visible).
Use the below filters to customise the number of articles displayed or search for specific title topics/keywords.
| Articles | |
|---|---|
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
|
Articles:
Renaming Windows 2000 Domain Name
| Read |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
MS Server Articles:
Windows Servers
Installation and Configuration of Fine-Grained ...
Microsoft introduced Fine-Grained Password Policy for the first time in Windows Server 2008 and the policy has been part of every Windows Server si...
Windows Servers
Configuring Windows Server Roaming Profiles
Windows roaming profiles allow the mobile users of a company to always work with their personal settings from any network computer in a domain. Roa...
Windows Servers
Windows 2003 DHCP Server Installation & Configu...
DHCP (Dynamic Host Configuration Protocol) is a protocol that allows clients on a network to request network configuration settings from a server r...
Windows Servers
Windows Server Group Policy Link Enforcement, I...
Our previous article explained what Group Policy Objects (GPO) are and showed how group policies can be configured to help control computers and us...
Featured Subcategories:
Virtualization & VM Backup Articles:
How to Enable SNMP on VMware ESXi Host & Config...
In this article we will show you how to enable SNMP on your VMware ESXi host, configure SNMP Community string and configure your ESXi firewall to a...
Understanding Deduplication. Complete Guide to ...
When considering your VM backup solution, key features such as deduplication are incredibly important. This is not simply from a cost perspective b...
SysAdmin Day 2020 - Get your Free Amazon Vouche...
SysAdmin Day has arrived, and with it, gratitude for all the unsung heroes that 2020 has needed. Your hard work has made it possible for all of us ...

Ultimate Guide: Install Windows 11 on VMware ES...
In this article, we’ll show you how to setup or install Microsoft Windows 11 on VMware’s ESXi servers and bypass the Trusted Platform Module versio...
Your IP address:
18.189.188.15
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!
Linux - Unix
Linux CentOS - Redhat EL Installation on HP Smart Ar...
This article was written thanks to our recent encounter of a HP DL120 G7 rack mount server equipped with a HP Smart Array B110i SATA Raid controller, ne...
Linux - Unix
Critical 15 Year-old Linux Security Hole (Ghost) Rev...
Security researchers at qualys.com yesterday released information on a critical 15 year-old Linux security hole which affects millions of Linux systems ...
Linux - Unix
Understanding The Linux Init Process & Different Run...
Different Linux systems can be used in many ways. This is the main idea behind operating different services at different operating levels. For example, ...
Linux - Unix
Installation and Configuration of Linux DHCP Server
For a cable modem or a DSL connection, the service provider dynamically assigns the IP address to your PC. When you install a DSL or a home cable router...
Popular Topics
Cisco Data Center (Nexus/UCS)
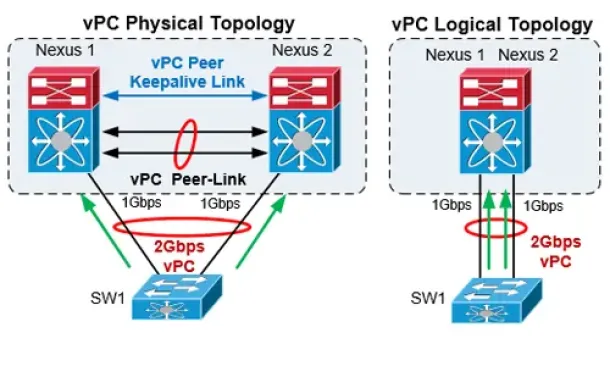
The Complete Cisco Nexus vPC Guide. Features & Advan...
Cisco virtual Port Channel (vPC) is a virtualization technology, launched in 2009, which allows links that are physically connected to two different Cis...
Windows Workstations (XP, 7, 8, 10, 11)
How to Start Windows 8 and 8.1 in Safe Mode – Enabli...
This article will show you how to start Windows 8 and Windows 8.1 in Safe Mode and how to enable F8 Safe Mode. Previous Windows O/S users would recall t...
Cisco Switches
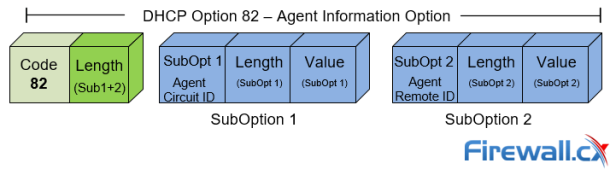
DHCP Option 82 Message Format, Analysis. DHCP Snoopi...
This article provides in-depth analysis of DHCP Option 82 (DHCP Relay Agent) which is one of the +180 DHCP Options available to the DHCP protocol and us...
Cisco Routers
Configuring PPTP (VPDN) Server On A Cisco Router
The Point to Point Tunneling Protocol (PPTP) is a network protocol used to create VPN tunnels between public networks. These VPN tunnels are encrypted f...

















