Articles
To read the articles in this section, simply click on the article title or read button on the far right (if visible).
Use the below filters to customise the number of articles displayed or search for specific title topics/keywords.
| Articles | |
|---|---|
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
|
Articles:
ICMP Protocol - Part 1: Introduction
| Read |
Suggested Articles:
TCP - UDP Protocol Analysis
TCP Header Anaylsis - Section 1: TCP Source & Des…
This section contains one of the most well-known fields in the TCP header, the Source and Destination port numbers. These fields are used to specify…
Network Fundamentals
Firewall Topologies
In this section we are going to talk about the different ways a firewall can be set up. Depending on your needs, you can have a very simple firewall…
Ethernet Protocol, CSMA/CD, Collisions
The Novell Proprietary Frame Format
Novell's Proprietary Frame Format was developed based on a preliminary release of the 802.3 specification. After Novell released its proprietary form…

Network Fundamentals
Power over Ethernet - Understanding PoE Technolog…
Power over Ethernet (PoE) was invented by PowerDsine back in 1997 and the first power injector (Midspan) was installed in 1998! Many manufacturespart…
Featured Subcategories:
Netflow Articles:
NetFlow Analyzer: Free Download, Step-by-Step Ins…
In our previous article we explained how a Netflow Analyzer can help you gain visibility into your user traffic, application traffic and data flows w…
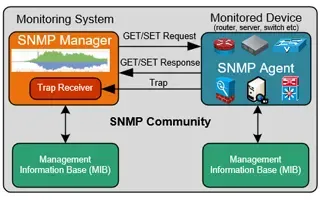
Netflow vs SNMP. Two Different Approaches to Netw…
SNMP (Simple Network Management Protocol) and Netflow are both popular protocols with admins, prized for their ability to give visibility over the ne…

Netflow: Monitor Bandwidth & Network Utilization…
Monitoring network traffic & bandwidth usage via Netflow is mandatory for any type and size network. Gaining visibility into user traffic, applic…
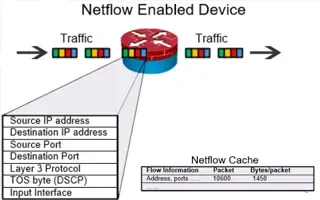
Complete Guide to Netflow: How Netflow & its Comp…
This article will cover the basics of Netflow, including its use cases, Netflow supported devices, Netflow history, and variants. We’ll also dive int…
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!

VLAN Networks
VLAN Security - Making the Most of VLANs
It's easy to see why virtual LANs have become extremely popular on networks of all sizes. In practical terms, multiple VLANs are pretty much the same as h…

VLAN Networks
Comparing Traditional Flat & VLAN Networks
Designing and building a network is not a simple job. VLANs are no exception to this rule, in fact they require a more sophisticated approach because of t…

VLAN Networks
VLANs - IEEE 802.1q Trunk Link Protocol Analysis
While the VLAN Tagging article briefly covered the IEEE 802.1q protocol this article will continue building upon it by further analyzing the IEEE 802.1q T…

VLAN Networks
VTP Protocol - In-Depth Analysis
The previous article introduced the VTP protocol, we examined how it can be used within a network, to help manage VLANs and ease the administrative overhe…
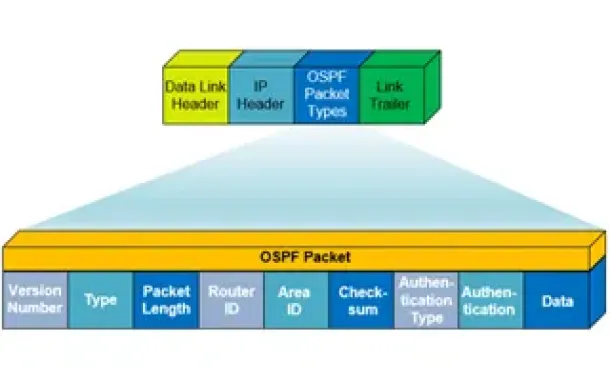
Routing
OSPF - Part 1: Introduction, OSPF Packet Structure, OS…
Open Shortest Path First (OSPF) is a popular routing protocol developed for Internet Protocol (IP) networks by the Interior Gateway Protocol (IGP) working…
Routing
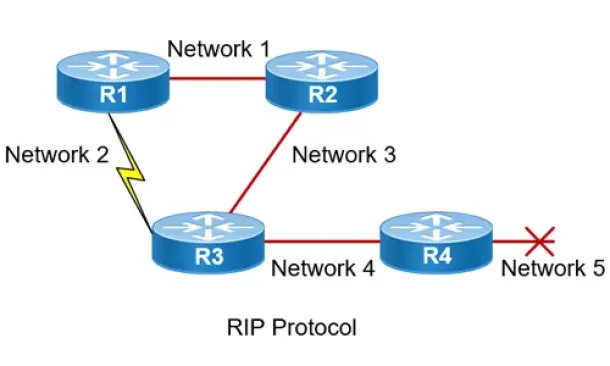
Routing Information Protocol - RIP
Routing Information Protocol (RIP) is a distance-vector routing protocol that is commonly used in small to medium-sized networks. It is one of the o…
Routing
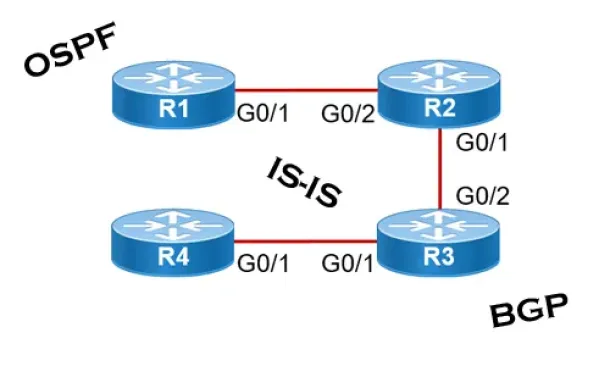
Link State Routing Protocols
Link State routing protocols do not view networks in terms of adjacent routers and hop counts, but they build a comprehensive view of the overall network…
Routing
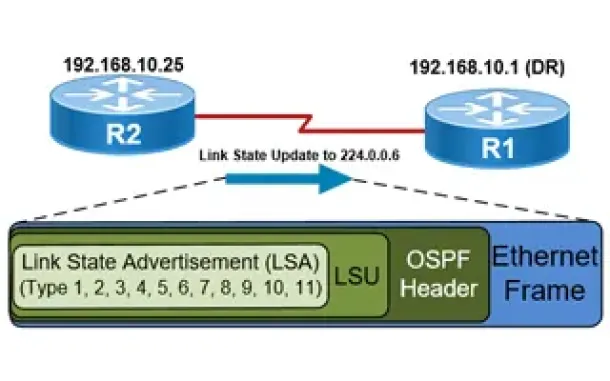
OSPF - Part 5: Analysis of OSPF Link State Update (LSU…
This article explains how OSPF uses Link State Advertisement (LSA) to exchange information about the network topology between routers. When a router recei…
Cisco Switches
Password Recovery / Password Reset Procedure for Catal…
This article shows how to reset a password on a Cisco Catalyst 3750-X (stacked or single unit) and Cisco Catalyst 3560-x switch without losing its startup…
Cisco Switches
Complete Guide to DHCP Snooping, How it Works, Concept…
This article covers popular Layer 2 & Layer 3 network attacks with a focus on DHCP Starvation Attacks, Man-in-the-Middle attacks, unintentional rogue…
Cisco Switches
Forcing A Cisco Catalyst Switch To Use 3rd Party SFP M…
Many companies are seeking for Cisco SFP alternatives to help cut down the costs on these expensive modules.
A frequent customer problem with Cisco's new…
Cisco Switches
Installation of a Cisco Catalyst 4507R-E Layer 3 Switch
Driven by our thirst for technical material and experience, we thought it would be a great idea to start presenting various installations of Cisco equipme…



















