Articles
To read the articles in this section, simply click on the article title or read button on the far right (if visible).
Use the below filters to customise the number of articles displayed or search for specific title topics/keywords.
Suggested Articles:
OpManager - Network Monitoring & Management
Boost Network Security and Efficiency with Inte...
Network alerts are vital for maintaining your network's health, efficiency, and security, ensuring seamless daily operations. They act as an early ...

EventLog Analyzer
Unlock Deep Visibility & Insight into Windows S...
This article explores the exciting new features of Windows Server 2022 and emphasizes the critical role of analyzing Windows Server logs. You'll al...

ManageEngine Firewall Analyzer
7 Essential Firewall Management Strategies for ...
A firewall appliance is a fundamental pillar of network security, acting as the first line of defense against cyber threats. However, its strengt...
Network Protocol Analyzers
Advanced Network Protocol Analyzer Review: Cola...
Firewall.cx has covered Colasoft Capsa several times in the past, but its constant improvements make it well worth revisiting. Since the last revie...
Featured Subcategories:
WireShark Articles:
How to Detect SYN Flood Attacks with Capsa Netw...
This article explains how to detect a SYN Flood Attack using an advanced protocol analyser like Colasoft Capsa. We’ll show you how to identify and ...
How to Perform TCP SYN Flood DoS Attack & Detec...
This article will help you understand TCP SYN Flood Attacks, show how to perform a SYN Flood Attack (DoS attack) using Kali Linux & hping3 and ...
How to Detect P2P (peer-to-peer) File Sharing, ...
Peer-to-Peer file sharing traffic has become a very large problem for many organizations as users engage in illegal (most times) file sharing proce...
How to Use Multi-Segment Analysis to Troublesho...
Troubleshooting network problems can be a very intensive and challenging process. Intermittent network problems are even more difficult to troubles...
Your IP address:
3.143.218.86
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!
Palo Alto Networks
The Ultimate Guide to Palo Alto Networks Software NG...
Discover the ins and outs of using Palo Alto Networks’ Software NGFW (Flex) credits to seamlessly renew your cloud-based or virtualized software NGFW de...

Palo Alto Networks
Complete Guide: Configuring IPSec VPN between Palo A...
This article will show you how to configure an IPSec VPN tunnel between a Palo Alto firewall (all PANOS versions) and Meraki MX security appliance. Our ...
Palo Alto Networks
How to Fix Palo Alto Firewall “Error: Image File Aut...
Keeping your Palo Alto Firewall up to date with the latest PAN-OS software updates is an important step to ensure your organization is protected against...
Palo Alto Networks
Introduction to Palo Alto Next-Generation Network Fi...
During the past decade, we’ve seen the global IT security market flooded with new network security and firewall security appliances. New vendors emergin...
Windows Servers
Free Hyper-V eBook - Create, Manage and Troubleshoot...
With the introduction of Hyper-V on the Windows Server platform, virtualization has quickly become the de facto standard for all companies seeking to co...
Windows Servers
Guide to Windows Server 2016 Hyper-V Hypervisor: New...
One of Windows Server 2016 highlights is the newer Hyper-V server that not only extends the hypervisor’s features and capabilities but also introduces a...
Windows Servers
Introduction To Windows Server 2012 R2 Virtualizatio...
FREE Hyper-V & VMware Backup: FREE for Firewall.cx readers for a Limited Time! Download Now!
Virtualization is an abstraction layer th...
Windows Servers
How to Install and Configure Windows 2012 DNS Server...
Our previous article covered introduction to the Domain Name System (DNS) and explained the importance of the DNS Server role within the network infrast...
Popular Topics
VLAN Networks
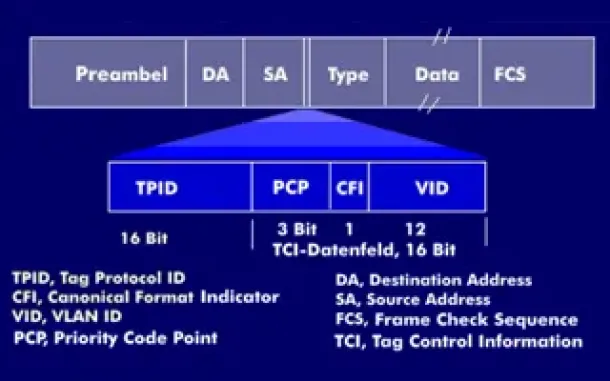
VLAN Tagging - Understanding VLANs Ethernet Frames
We mentioned that Trunk Links are designed to pass frames (packets) from all VLANs, allowing us to connect multiple switches together and independently ...
SASE & SD-WAN Networks
Understanding Secure Access Service Edge (SASE) and ...
Software Defined Wide Area Networking (SD-WAN) is changing the way that businesses connect to the cloud. With SD-WAN, organizations can move away from c...
Network Fundamentals
Network Broadcast
The term "Broadcast" is used very frequently in the networking world . You will see it in most networking books and articles, or see it happening on you...
Virtualization & VM Backup
Differences Between VMware vSphere, vCenter, ESXi Fr...
In this article we will cover the differences between VMware ESXi, vSphere and vCenter while also explain the features supported by each vSphere edition...

Cisco Data Center (Nexus/UCS)
Introduction to Cisco Nexus Switches – Nexus Product...
This article introduces the Cisco Nexus product family (Nexus 9000, Nexus 7000, Nexus 5000, Nexus 3000, Nexus 2000, Nexus 1000V and MDS 9000). We explai...
Cisco CallManager-CCME
IP Phone 7945, 7965, 7975 Factory Reset Procedure, S...
This article explains how to reset your Cisco 7945, 7965 and 7975 IP phone to factory defaults, and how to upgrade the firmware to the latest available ...
Cisco CallManager-CCME
IP Phone 7900 Series (7940, 7941, 7942, 7960, 7961, ...
This article explains how to reset your Cisco 7940, 7941, 7942, 7960, 7961, 7962 & 7920 IP phone to factory defaults, and how to upgrade its firmwar...
Cisco CallManager-CCME
Connecting & Configuring SPA8000 with UC500, 520, 54...
When it comes to connecting multiple analog phones to VoIP systems like Cisco’s Unified Communication Manager Express (CallManager Express) or UC500 ser...


















