Unlock Deep Visibility & Insight into Windows Server 2022 Logs
 This article explores the exciting new features of Windows Server 2022 and emphasizes the critical role of analyzing Windows Server logs. You'll also discover how EventLog Analyzer provides comprehensive, helps you achieve 360-degree protection against threats targeting these logs, ensuring robust security for your server environment.
This article explores the exciting new features of Windows Server 2022 and emphasizes the critical role of analyzing Windows Server logs. You'll also discover how EventLog Analyzer provides comprehensive, helps you achieve 360-degree protection against threats targeting these logs, ensuring robust security for your server environment.
Key Topics:
- The Importance of Proactive Log Management
- Windows Server 2022 and its Key Features
- Understanding Windows Server Logs
- The Importance of Analyzing Windows Server Logs
- Benefits of Using EventLog Analyzer for Windows Server Log Analysis
- Configuring EventLog Analyzer to Connect to Windows Server
- Summary
Related Articles:
- Event Log Monitoring System: Implementation, Challenges & Standards Compliance
- Detecting Windows Server Security Threats with Advanced Event Log Analyzers
The Importance of Proactive Log Management
Did you know that threats targeting Windows Server and its logs are becoming more significant? To protect your systems, you must monitor and analyze these logs effectively. Ensuring system security, compliance, and health requires effective log management.
Administrators can ensure optimal performance by promptly identifying and resolving issues through routine log review. Log analysis also protects sensitive data by assisting in the detection of any security breaches and unwanted access. Proactive log management ultimately improves the security and dependability of the IT infrastructure as a whole.
EventLog Analyzer monitors various Windows event logs, such as security audit, account management, system, and policy change event logs. The insights gleaned from these logs are displayed in the forms of comprehensive reports and user-friendly dashboards to facilitate the proactive resolution of security issues.
Windows Server 2022 and its Key Features
Windows Server 2022 is a server operating system developed by Microsoft as a part of the Windows New Technology family. It is the most recent version of the Windows Server operating system, having been released in August 2021. Large-scale IT infrastructures can benefit from the enterprise-level administration, storage, and security features offered by Windows Server 2022. Compared to its predecessors, it has various new and improved capabilities, with an emphasis on application platform advancements, security, and hybrid cloud integrations.
Let’s take a look at a few key features of Windows Server 2022:
- Cutting-edge security features, such as firmware protection, virtualization-based security, hardware roots of trust, and secured-core servers, that protect against complex attacks.
- Improved management and integrations with Azure services via Azure Arc's support for hybrid cloud environments.
- New storage features, which include Storage Migration Service enhancements, support for larger clusters, and improvements to Storage Spaces Direct.
- Enhancements to Kubernetes, container performance, and Windows containers in Azure Kubernetes Service to improve support for containerized applications.
- Support for more powerful hardware configurations, including more memory and CPU capacity, with enhanced performance for virtualized workloads.
- File size reductions during transfers to increase efficiency and speed through the use of Server Message Block (SMB) compression.
- An integration with Azure Automanage for easier deployment, management, and monitoring of servers in hybrid and on-premises environments.
- Improved networking features, such as enhanced network security and performance as well as support for DNS over HTTPS.
- Enhanced VPN and hybrid connectivity options, such as an SMB over QUIC capability that permits safe, low-latency file sharing over the internet.
- Improvements to Windows Subsystem for Linux and tighter integration for cross-platform management, which provides better support for executing Linux workloads.
- A range of flexible deployment and licensing options, such as the usage of Azure's subscription-based licensing.
- Support for modernizing existing .NET applications and developing new applications using the latest .NET 5.0 technologies.
- Enhanced automation capabilities with the latest version of PowerShell, PowerShell 7.
Understanding Windows Server Logs
Windows Server event logs are records of events that occur within the operating system or other software running on a Windows server. You can manage, observe, and troubleshoot the server environment with the help of these logs. The logs capture numerous pieces of information, such as application problems, security incidents, and system events. By examining and evaluating these logs, administrators can ensure the security, functionality, and health of the server.
Here are the different types of Windows Server logs:
- System logs: These logs document operating-system-related events, including hardware modifications, driver issues, and system startups and shutdowns.
- Application logs: These logs capture events generated by applications running on the server and include software errors, warnings, and informational messages.
- Security logs: Security logs keep track of events related to security, such as successful and unsuccessful login attempts, actions taken by users to manage their accounts (such as adding or removing accounts), and modifications made to security guidelines.
- Setup logs: Setup logs record activities about Windows Server and the installation and configuration of its components.
- Forwarded event logs: These logs gather events and are sent from one computer to another, enabling the centralized management of several workstations or servers.
The Importance of Analyzing Windows Server Logs
Windows Server log analysis is essential for several reasons, most of which have to do with security, system performance, and troubleshooting. Here are a few reasons:
- Logs help you identify any unauthorized access attempts, such as failed login attempts, which may point to possible security risks.
- For forensic investigations, logs offer a thorough audit record of user activities, which facilitates action tracing on the server.
- Administrators can identify unusual trends in logs, such as unexpected file changes or system modifications, which could indicate malware or other malicious activity.
- Logs can assist administrators in optimizing server performance and avoiding bottlenecks by revealing the resource utilization of the CPU, memory, and disk.
- Regular log analysis enables proactive maintenance and minimizes downtime by helping you discover any hardware or software issues before they become severe, aiding in system health monitoring.
- Windows Server event logs record errors and warnings that occur during the operation of the system, providing detailed information that is essential for troubleshooting and problem resolution.
- Logs provide information about the performance and stability of different services and applications that are operating on the server, assisting administrators in promptly finding and fixing problems.
- Many industries are subject to regulations that require detailed logging of server activities. Regular log analysis ensures that organizations meet these compliance requirements.
- Logs can be used to generate reports for management or auditors, providing evidence of security measures, performance metrics, and system usage.
Benefits of Using EventLog Analyzer for Windows Server Log Analysis
EventLog Analyzer provides valuable insights and better extractions from logs, making it a superior event logging tool compared to other tools. Here are a few key capabilities of EventLog Analyzer that help in Windows Server event log analysis:
- Automate log file management: With EventLog Analyzer's auto-discover option (see below screenshot), you can quickly identify all Windows log sources inside your domain and begin collecting Windows event logs. This feature automatically detects Windows workstations, firewalls, IIS servers, and SQL servers. To strengthen your network security, you can just choose the important sources and automate log file management.
 EventLog Analyzer's auto-discover option (click to enlarge)
EventLog Analyzer's auto-discover option (click to enlarge)
- Analyze logs comprehensively: With the help of EventLog Analyzer's robust correlation engine, you can obtain thorough insights into log data from every log source in the network (see screenshot below). More than 40 prebuilt correlation rules are included in the Windows log monitoring application to identify common cyberattacks, including brute-force, ransomware, DoS, and SQL injection attacks. You also have the option to build custom rules to detect more complex attack patterns.
- Conduct root cause analysis: EventLog Analyzer provides real-time Windows activity monitoring and lets you look through raw event logs to identify the precise log entry that resulted in a security issue (see screenshot below). So, in just a few minutes, you can determine the root cause of any security incident in your network.
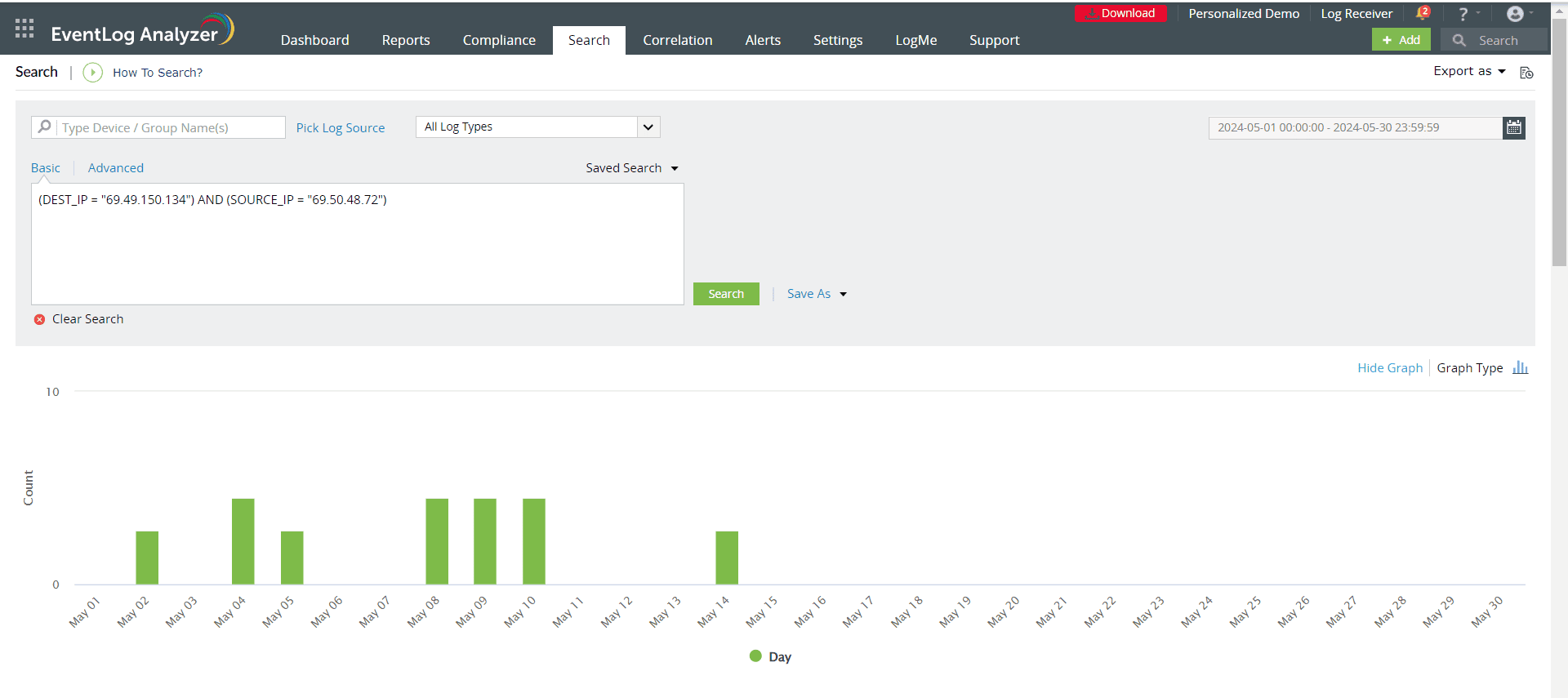 EventLog Analyzer's log search feature (click to enlarge)
EventLog Analyzer's log search feature (click to enlarge)
- Finding critical details about the identified incident, such as its severity, the time, the location, and the user involved, is made simple with the help of the log search feature (see screenshot below). This enables you to quickly take the necessary countermeasures to expedite the resolution of incidents.
- Obtain detailed reports: For the Windows environment, EventLog Analyzer generates a number of reports that help with more detailed event auditing and monitoring. Reports on common attacks against Windows devices are also included (see screenshot below). EventLog Analyzer uses the event logs from Windows desktops and servers to provide comprehensive reports. It includes many Windows-specific report templates for security events such as failed logins, account lockouts, and security log manipulation. EventLog Analyzer also issues an email or SMS alert message as soon as it identifies a suspicious occurrence.
 EventLog Analyzer's reports related to Windows Server activities (click to enlarge)
EventLog Analyzer's reports related to Windows Server activities (click to enlarge)
Additionally, the solution includes report templates that help ensure compliance with regulations like the PCI DSS, SOX, HIPAA, the GDPR, and FISMA (see screenshot below). Custom reports can also be created to measure adherence to internal audit guidelines.
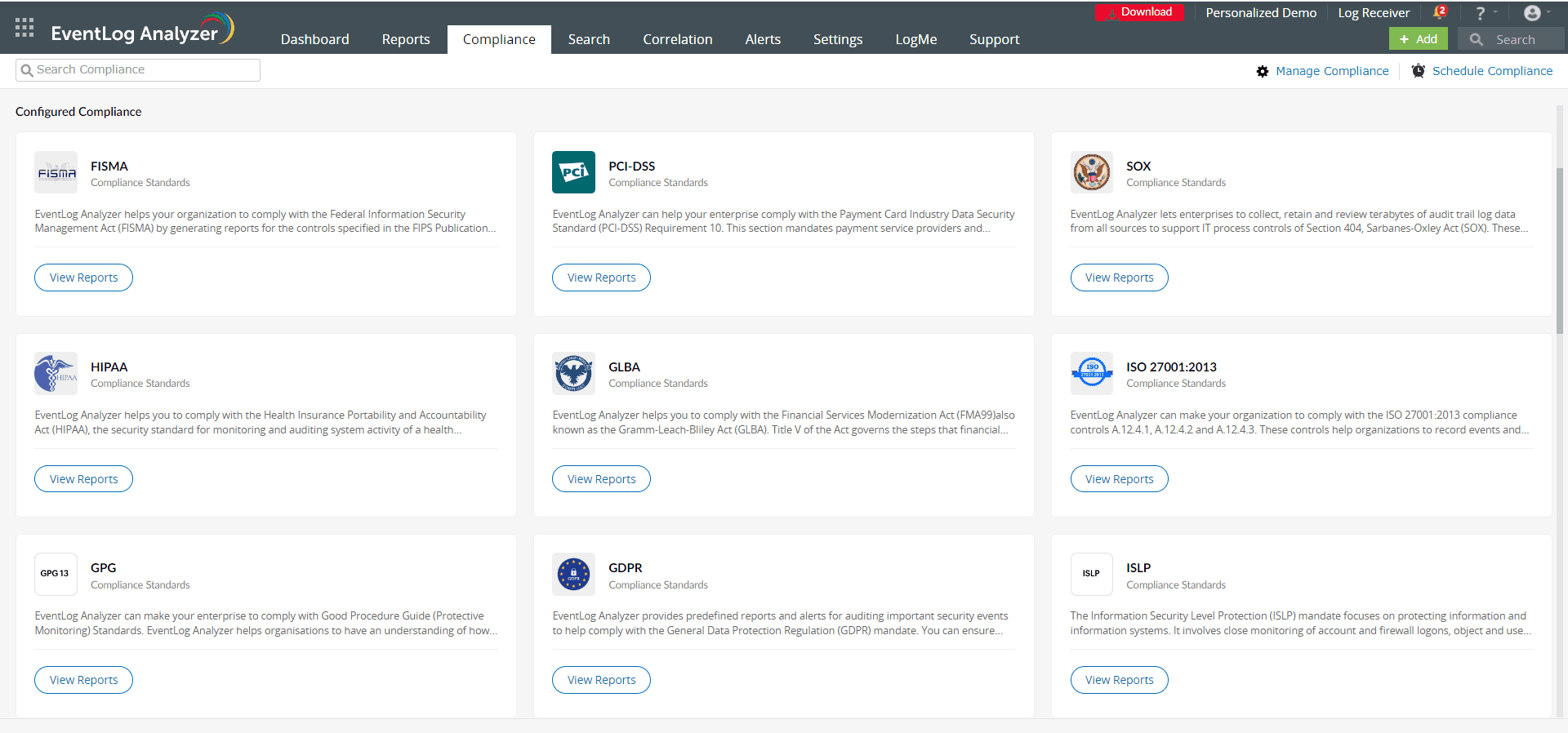 EventLog Analyzer's compliance reports (click to enlarge)
EventLog Analyzer's compliance reports (click to enlarge)
- Receive instant alerts: Instantly identify security incidents occurring in your network and accelerate the troubleshooting process with EventLog Analyzer. You can use EventLog Analyzer to provide real-time alerts to manage incidents based on logs generated with a given log type, event ID, message, or severity (see screenshot below). The solution also supports integrations with help desks, so tickets can be raised automatically in your help desk software.
 Real-time alerts generated in EventLog Analyzer (click to enlarge)
Real-time alerts generated in EventLog Analyzer (click to enlarge)
- Utilize advanced threat analytics: Through the use of reputation scores for potentially malicious URLs, domains, and IP addresses, the Advanced Threat Analytics add-on provides insightful information about the severity of threats (see screenshot below). By retrieving information about malicious IPs and domains with reputation scores, this feature alerts administrators about any suspicious IPs attempting to join your network.
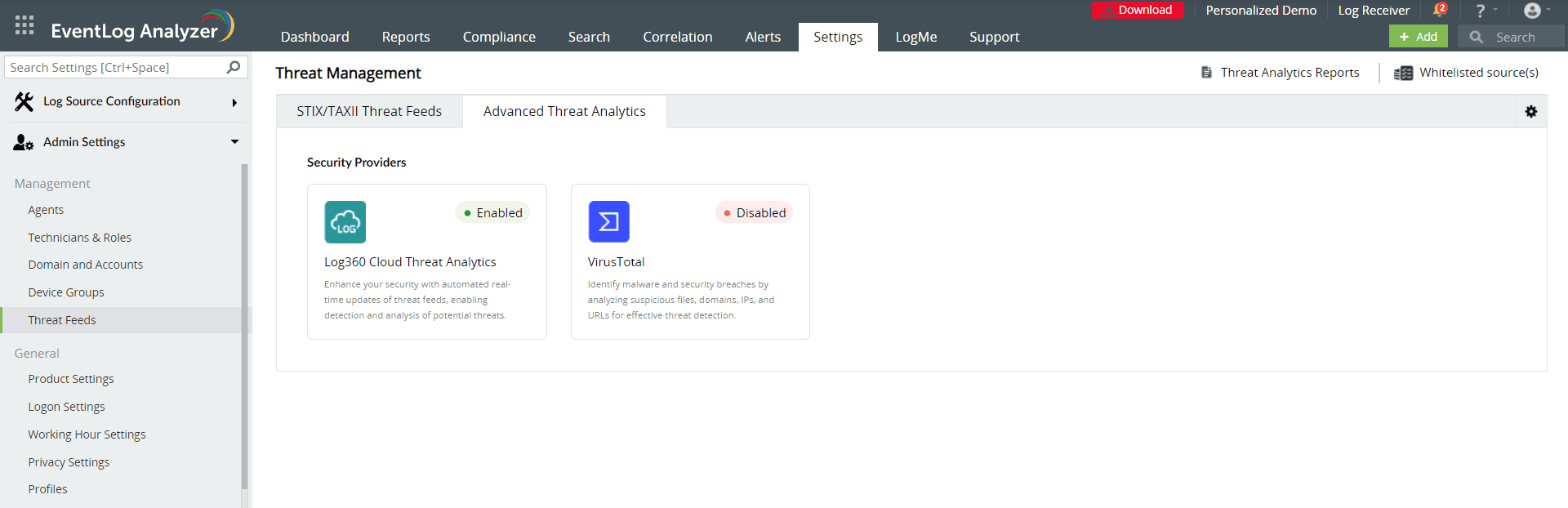 EventLog Analyzer's Advanced Threat Analytics feature (click to enlarge)
EventLog Analyzer's Advanced Threat Analytics feature (click to enlarge)
- Archive logs: EventLog Analyzer lets you specify the number of days after which event logs must be moved to the archive so you can automate the archiving of event logs (see screenshot below). After the archive period has been configured, EventLog Analyzer will organize event logs into folders on its own and compress those folders before encrypting them to ensure integrity and guard against tampering. Whenever they're needed, the archived log files can be imported into EventLog Analyzer for forensics purposes.
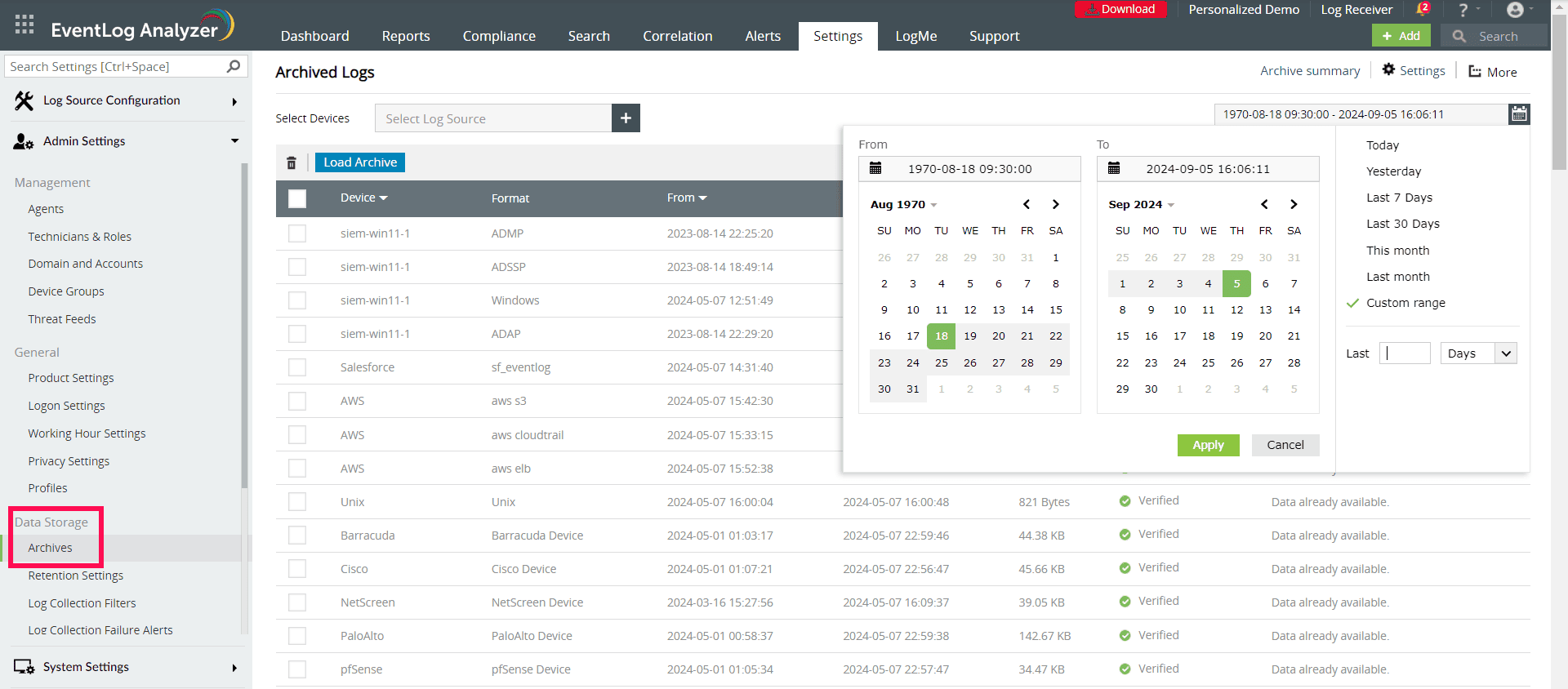 Event log archiving with EventLog Analyzer (click to enlarge)
Event log archiving with EventLog Analyzer (click to enlarge)
Configuring EventLog Analyzer to Connect to Windows Server
Installing the Windows agent is mandatory for monitoring the files on Windows Server and collecting Windows event logs for EventLog Analyzer when it's deployed on Linux operating systems.
Here are the steps to install the EventLog Analyzer agent using the product console:
1. On the Settings tab, navigate to Admin Settings > Agents.
2. Click '+ Install Agent', then click the '+' icon next to Device(s):
 Installing the EventLog Analyzer agent (click to enlarge)
Installing the EventLog Analyzer agent (click to enlarge)
3. Select the devices on which you want to install the agent:
 Selecting the devices on which to install the EventLog Analyzer agent (click to enlarge)
Selecting the devices on which to install the EventLog Analyzer agent (click to enlarge)
4. Enter the username and password to access the devices. This account should have admin privileges to install the agent successfully. Alternatively, you can select the Use Default Credentials option:
Following this, in order to add the Windows devices, follow the steps given below:
- On the Settings tab, navigate to Log Source Configuration > Devices.
- Click '+ Add Device(s)' and select the domain from the Select Category drop-down menu. The Windows devices in the selected domain will be automatically discovered and listed:
 Automatically discovering devices in EventLog Analyzer (click to enlarge)
Automatically discovering devices in EventLog Analyzer (click to enlarge)
- Select the devices by clicking the respective check boxes. You can easily search for a device by using the search box or by filtering based on the OU with the OU Filter option:
 Using the OU Filter option in EventLog Analyzer to search for devices (click to enlarge)
Using the OU Filter option in EventLog Analyzer to search for devices (click to enlarge)
- Click Add to add the devices for monitoring.
With EventLog Analyzer, you can customize log collection based on time. You have the option of collecting logs from the current time or from the past few hours, days, weeks, or even months.
To collect logs according to time:
- On the Settings tab, navigate to Log Source Configuration > Devices > + Add Device(s) > + Configure Manually.
- Click the historical log collection icon in the top-right corner as shown below:
 Historical log collection in EventLog Analyzer.
Historical log collection in EventLog Analyzer.
- For the Collect log from last option, select the number of hours, days, weeks, or months for which you would like to collect the historical logs.
- Click Apply.
Summary
Analyzing and monitoring Windows Server event logs involves checking for errors, security breaches, or malfunctions in system-generated logs in real time. This facilitates enhancing security, ensuring high system performance, and promptly resolving issues. It ensures proactive issue resolution and compliance with security policies.
EventLog Analyzer is a comprehensive log management tool that supports Windows event logs along with other log sources—all on a single console. It parses, analyzes, correlates, and archives log data to complete the log management process once the logs are collected on a central server.
Your IP address:
3.15.158.138
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!