Palo Alto: Top Picks
Palo Alto Networks
Complete Guide to Upgrading Palo Alto Firewall ...
Upgrading your Palo Alto Firewall or Panorama Management System to the preferred PAN-OS release is always recommended as it ensures it remains stab...
Palo Alto Networks
Palo Alto Networks Firewall - Web & CLI Initial...
This article is the second-part of our Palo Alto Networks Firewall technical articles. Our previous article was introduction to Palo Alto Networks ...
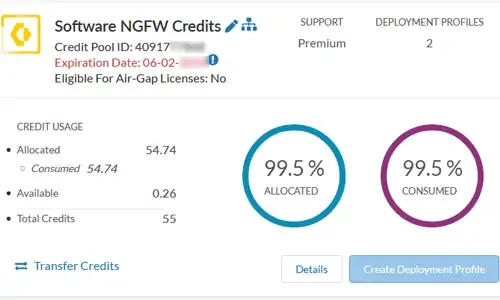
Palo Alto Networks
The Ultimate Guide to Palo Alto Networks Softwa...
Discover the ins and outs of using Palo Alto Networks’ Software NGFW (Flex) credits to seamlessly renew your cloud-based or virtualized software NG...
Palo Alto Networks
Palo Alto Firewall Configuration Options. Tap M...
Our previous article explained how Palo Alto Firewalls make use of Security Zones to process and enforce security policies. This article will expla...
Featured Subcategories:
SD-WAN & SASE Articles:
Security Service Edge (SSE)
Security Service Edge (SSE) Limitations & Disad...
This article explores the Security Service Edge (SSE) portion of Secure Access Service Edge (SASE) and the need for holistic cybersecurity protecti...
SASE & SD-WAN Networks
How To Secure Your SD-WAN. Comparing DIY, Manag...
With so much enterprise network traffic now destined for the cloud, backhauling traffic across an expensive MPLS connection to a data center to app...
SASE & SD-WAN Networks
WAN Optimization vs SD WAN Networks. Today’s Ch...
Enterprises have been successfully running WAN optimization appliances at their many distributed sites for years. The devices have done a good job ...
SASE & SD-WAN Networks
Understanding Secure Access Service Edge (SASE)...
Software Defined Wide Area Networking (SD-WAN) is changing the way that businesses connect to the cloud. With SD-WAN, organizations can move away f...
F5 Networks:
Network Protocol & Firewall Analyzers:
Network Protocol Analyzers
How to Perform TCP SYN Flood DoS Attack & Detec...
This article will help you understand TCP SYN Flood Attacks, show how to perform a SYN Flood Attack (DoS attack) using Kali Linux & hping3 and ...
Network Protocol Analyzers
Introducing Colasoft Unified Performance Manage...
Colasoft Unified Performance Management (UPM) is a business-oriented network performance management system, which analyzes network performance, qua...

ManageEngine Firewall Analyzer
Dealing with Security Audit Challenges: Discove...
The utilization of log analyzers, such as Firewall Analyzer, in network infrastructure plays a pivotal role in enhancing cybersecurity and fortifyi...
Network Protocol Analyzers
How to Detect Routing Loops and Physical Loops ...
When working with medium to large scale networks, IT departments are often faced dealing with network loops and broadcast storms that are caused by...
Your IP address:
18.188.80.46
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!
Web Vulnerability Application Scanners & VPN Services
Web Application Vulnerability Scanners
Acunetix v13 Release Introduces Groundbreaking Innov...
The newest release of the Acunetix Web Vulnerability Scanner further improves performance and premieres best-of-breed technologies.
Acunetix, the pione...
Web Application Vulnerability Scanners
Everything You Need to Know About SQL Injection Atta...
SQL Injection Attacks are one of the most popular attacks against web servers, websites and web applications. A fairly popular website can expect to rec...
VPN Services & Guides
Best VPN Review: StrongVPN. Download Speed Τest, Tor...
StrongVPN is one of the most popular VPN service around the world. With a presence in over 23 countries,+650 servers, cheap prices, Strong Encrypti...
VPN Services & Guides
Best VPN Review: Private Internet Access (PIA) Featu...
The market for Virtual Private Networks has exploded over the past few years. A wealth of new providers has appeared, promising logless browsing, true a...

















