Articles
To read the articles in this section, simply click on the article title or read button on the far right (if visible).
Use the below filters to customise the number of articles displayed or search for specific title topics/keywords.
| Articles | |
|---|---|
| Read | |
| Read | |
| Read | |
|
Articles:
The OSI Model: Layer 5 - Session Layer
| Read |
|
Articles:
The OSI Model: Layer 4 - Transport Layer
| Read |
|
Articles:
The OSI Model: Layer 3 - Network Layer
| Read |
|
Articles:
The OSI Model: Layer 2 - Datalink Layer
| Read |
|
Articles:
The OSI Model: Layer 1 - Physical Layer
| Read |
Suggested Articles:
Subnetting
IP Subnetting - Part 5: Subnetting Guidelines
There is always that day when you are called upon to provide a solution to a network problem. The number of problems that can occur in a network ar...
Network Cabling
Early Communication Technology - Morse Code and...
We tend to think of digital communication as a new idea but in 1844 a man called Samuel Morse sent a message 37 miles from Washington D.C. to Balti...
Network Cabling
Serial Direct Cable Connection, DB9, DB25, COM ...
This article covers the popular serial ports on workstations, servers and laptop computers. We cover serial data transfer, port pinouts, port speed...
ICMP Protocol
ICMP Protocol - Part 2: Echo / Echo Reply (Ping...
As mentioned in the previous page, an Echo is simply what we networking engineers call a 'ping'. The Echo Reply is, as most would guess, the ...
Featured Subcategories:
Netflow Articles:

Netflow: Monitor Bandwidth & Network Utilizatio...
Monitoring network traffic & bandwidth usage via Netflow is mandatory for any type and size network. Gaining visibility into user traffic, appl...
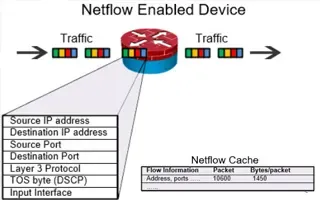
Complete Guide to Netflow: How Netflow & its Co...
This article will cover the basics of Netflow, including its use cases, Netflow supported devices, Netflow history, and variants. We’ll also dive i...
NetFlow Analyzer: Free Download, Step-by-Step I...
In our previous article we explained how a Netflow Analyzer can help you gain visibility into your user traffic, application traffic and data flows...
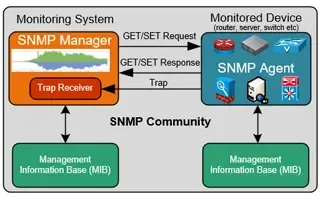
Netflow vs SNMP. Two Different Approaches to Ne...
SNMP (Simple Network Management Protocol) and Netflow are both popular protocols with admins, prized for their ability to give visibility over the ...
Your IP address:
18.222.81.215
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!

VLAN Networks
VLAN Security - Making the Most of VLANs
It's easy to see why virtual LANs have become extremely popular on networks of all sizes. In practical terms, multiple VLANs are pretty much the same as...

VLAN Networks
VLANs - Access & Trunk Links
If you've read our previous article The VLAN Concept - Introduction to VLANs then you should feel comfortable with terms such as 'VLAN', 'Sta...
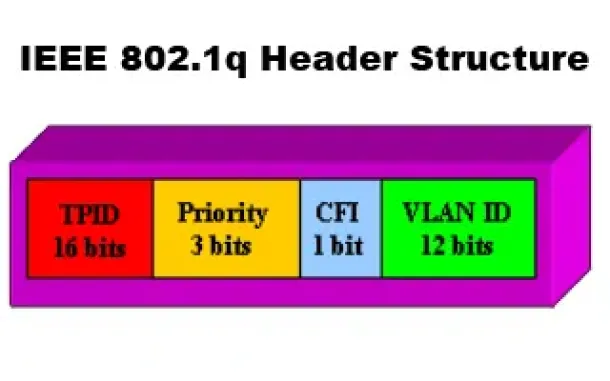
VLAN Networks
VLANs - IEEE 802.1q Trunk Link Protocol Analysis
While the VLAN Tagging article briefly covered the IEEE 802.1q protocol this article will continue building upon it by further analyzing the IEEE 802.1q...

VLAN Networks
VLAN InterSwitch Link (ISL) Protocol Analysis
Deciding whether to use ISL or IEEE 802.1q to power your trunk links can be quite confusing if you cannot identify the advantages and disadvantages of e...
Routing
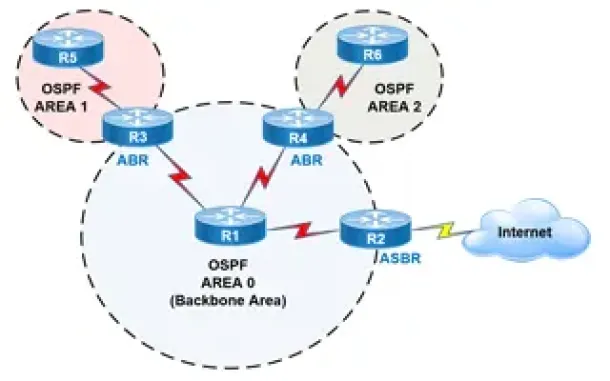
OSPF - Part 2: How OSPF Protocol Works & Basic Conce...
This article covers basic OSPF concepts and operation. We explain how OSPF works, how OSPF tables are built on an OSPF-enabled router and their purpose ...
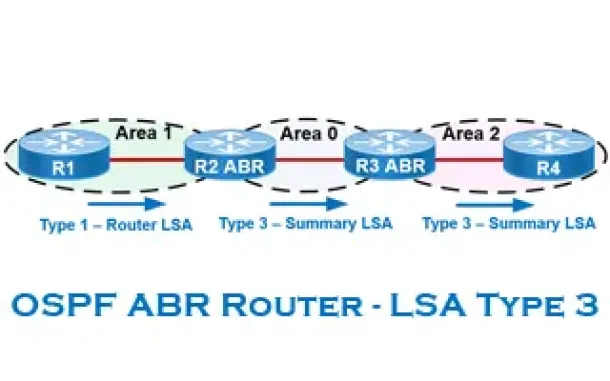
Routing
OSPF - Part 6: OSPF LSA Types - Purpose and Function...
Our previous article explained the purpose of Link State Update (LSU) packets and examined the Link State Advertisement (LSA) information contained with...
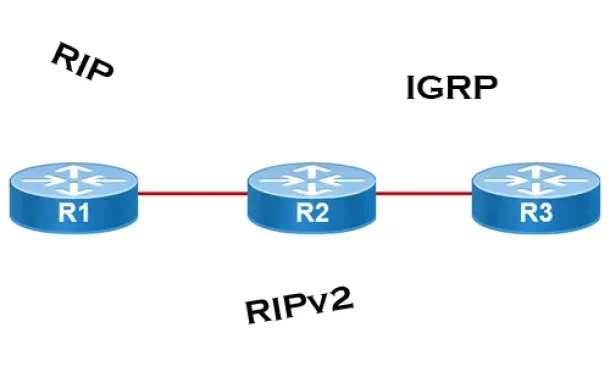
Routing
Distance Vector Routing Protocols
Distance Vector routing protocols use frequent broadcasts (255.255.255.255 or FF:FF:FF:FF) of their entire routing table every 30 sec. on all their inte...
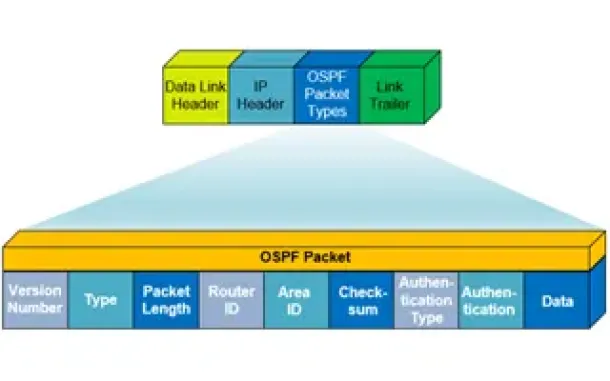
Routing
OSPF - Part 1: Introduction, OSPF Packet Structure, ...
Open Shortest Path First (OSPF) is a popular routing protocol developed for Internet Protocol (IP) networks by the Interior Gateway Protocol (IGP) worki...
Cisco Routers
Cisco Router 'User Exec' Mode
Introduction
Let's see what it looks like to be in User-Exec mode on a Cisco router. Below, we have telneted into our lab router and are in User Exec M...
Cisco Routers
Configuring NAT Overload On A Cisco Router
NAT (Network Address Translation) is a method that allows the translation (modification) of IP addresses while packets/datagrams are traversing the netw...
Virtualization & VM Backup
How to Enable SNMP on VMware ESXi Host & Configure E...
In this article we will show you how to enable SNMP on your VMware ESXi host, configure SNMP Community string and configure your ESXi firewall to allow ...
Windows Servers
Windows Server 2016 Licensing Made Easy – Understand...
This article describes the new Windows Server 2016 Licensing model (per-core licensing) Microsoft has implemented for its new server-based operating sys...


















