Articles
To read the articles in this section, simply click on the article title or read button on the far right (if visible).
Use the below filters to customise the number of articles displayed or search for specific title topics/keywords.
| Articles | |
|---|---|
| Read | |
|
Articles:
802.3 Fast Ethernet (100 Mbit/Sec) Model
| Read |
|
Articles:
Migrating From Ethernet To Fast Ethernet
| Read |
| Read | |
| Read | |
|
Articles:
The Novell Proprietary Frame Format
| Read |
|
Articles:
The IEEE 802.3 SNAP Frame Format
| Read |
|
Articles:
The Ethernet II Frame Format
| Read |
|
Articles:
The IEEE 802.3 Frame Format
| Read |
|
Articles:
Manchester Signal Encoding
| Read |
|
Articles:
IEEE 802.3 Interframe Spacing
| Read |
| Read | |
|
Articles:
Propagation Delay
| Read |
|
Articles:
Late Ethernet Collisions
| Read |
|
Articles:
Early Ethernet Collisions
| Read |
|
Articles:
Introduction to Ethernet Collisions
| Read |
|
Articles:
What is CSMA/CD ?
| Read |
Suggested Articles:
Domain Name System (DNS)
The DNS Protocol - Part 1: Introduction
If you ever wondered where DNS came from, this is your chance to find out ! The quick summary on DNS's history will also help you understand why DN...
Network Address Translation - NAT
Network Address Translation (NAT) Concepts
Before we dive into the deep waters of NAT, we need to make sure we understand exactly what NAT does. So let me give you the background of NAT, why...
Ethernet Protocol, CSMA/CD, Collisions
Ethernet Troubleshooting - Physical Frame Corru...
When troubleshooting your Ethernet network, the first thing to look for is physical frame corruption. In this essay, we will discuss the different ...
Network Cabling
1Gigabit 802.3ab -10GBase (10Gigabit) 802.3an E...
The 1000Base Ethernet standard, also referred to as Gigabit Ethernet (GbE or 1GigE) is defined by the IEEE 802.3-2008 standard and provides 10 time...
Featured Subcategories:
Netflow Articles:
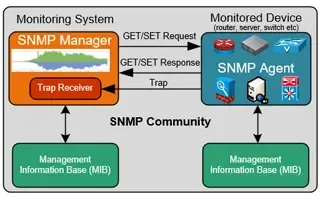
Netflow vs SNMP. Two Different Approaches to Ne...
SNMP (Simple Network Management Protocol) and Netflow are both popular protocols with admins, prized for their ability to give visibility over the ...

Netflow: Monitor Bandwidth & Network Utilizatio...
Monitoring network traffic & bandwidth usage via Netflow is mandatory for any type and size network. Gaining visibility into user traffic, appl...
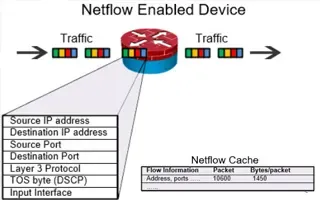
Complete Guide to Netflow: How Netflow & its Co...
This article will cover the basics of Netflow, including its use cases, Netflow supported devices, Netflow history, and variants. We’ll also dive i...
NetFlow Analyzer: Free Download, Step-by-Step I...
In our previous article we explained how a Netflow Analyzer can help you gain visibility into your user traffic, application traffic and data flows...
Your IP address:
3.145.88.233
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!

VLAN Networks
VLANs - Access & Trunk Links
If you've read our previous article The VLAN Concept - Introduction to VLANs then you should feel comfortable with terms such as 'VLAN', 'Sta...

VLAN Networks
VTP Pruning
VTP (VLAN Trunking Protocol) pruning is a feature that is used in Cisco switches to reduce unnecessary traffic in VLAN (Virtual Local Area Network) trun...

VLAN Networks
VTP Protocol - In-Depth Analysis
The previous article introduced the VTP protocol, we examined how it can be used within a network, to help manage VLANs and ease the administrative over...

VLAN Networks
Dynamic VLANs
Dynamic VLANs were introduced to grant the flexibility and complexity(!) that Static VLANs did not provide. Dynamic VLANs are quite rare because of thei...
Routing
Interior Gateway Protocol - IGRP
IGRP (Interior Gateway Routing Protocol) is a Cisco proprietary distance-vector routing protocol used in enterprise networks to exchange routing informa...
Routing
Hybrid Routing Protocols - Advantages and Disadvanta...
Hybrid routing protocols are a combination of distance-vector and link-state routing protocols, and are used to provide a more efficient and scala...
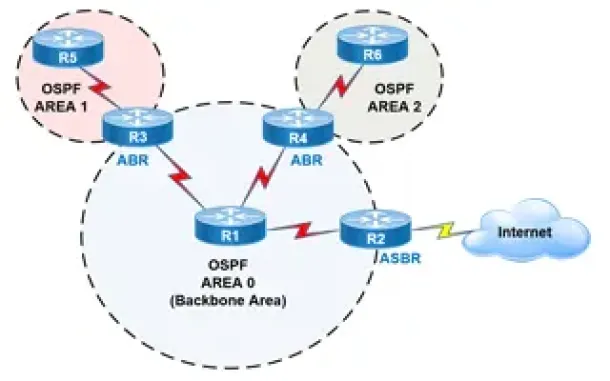
Routing
OSPF - Part 2: How OSPF Protocol Works & Basic Conce...
This article covers basic OSPF concepts and operation. We explain how OSPF works, how OSPF tables are built on an OSPF-enabled router and their purpose ...
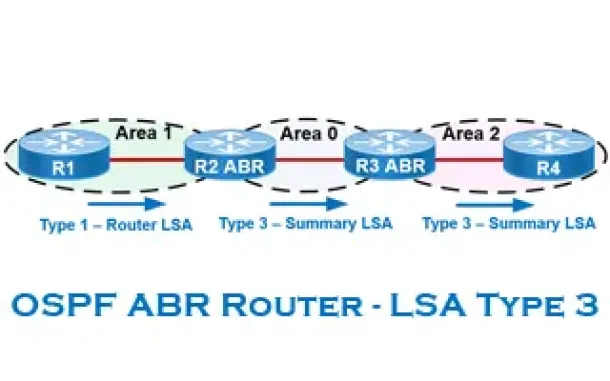
Routing
OSPF - Part 6: OSPF LSA Types - Purpose and Function...
Our previous article explained the purpose of Link State Update (LSU) packets and examined the Link State Advertisement (LSA) information contained with...
Cisco Routers
Configuring Policy-Based Routing (PBR) with IP SLA T...
What is Policy-Based Routing?
Policy-Based Routing (PBR) is a very popular feature in Cisco routers, it allows the creation of policies that can select...
Windows Servers
Renaming Windows 2000 Domain Name
Sometimes renaming a domain is an essential business requirement. There are many situations, such as mergers, change of company name or migration from a...
Cisco Routers
Troubleshooting PPP Internet Connection On A Cisco R...
The Point-to-Point Protocol is one of the most popular protocols around used by engineers, ISPs and companies around the globe for authentication of rem...
Cisco Switches
Forcing A Cisco Catalyst Switch To Use 3rd Party SFP...
Many companies are seeking for Cisco SFP alternatives to help cut down the costs on these expensive modules.
A frequent customer problem with Cisco's n...


















