Suggested Articles:
Network Protocol Analyzers
How To Detect ARP Attacks & ARP Flooding With C...
ARP attacks and ARP flooding are common problems small and large networks are faced with. ARP attacks target specific hosts by using their MAC addr...

OpManager - Network Monitoring & Management
Maximizing Network Security: A Deep Dive into O...
In the rapidly evolving landscape of cyber threats, network security has never been more crucial. With the frequency and sophistication of cyberatt...
Network Protocol Analyzers
Introducing Colasoft Unified Performance Manage...
Colasoft Unified Performance Management (UPM) is a business-oriented network performance management system, which analyzes network performance, qua...
OpManager - Network Monitoring & Management
Ensuring Enterprise Network Readiness for Mobil...
Demands for Enterprise networks to properly support mobile users is on a continuous rise making it more than ever necessary for IT departments to p...
Featured Subcategories:
WireShark Articles:
How to Detect SYN Flood Attacks with Capsa Netw...
This article explains how to detect a SYN Flood Attack using an advanced protocol analyser like Colasoft Capsa. We’ll show you how to identify and ...
How to Use Multi-Segment Analysis to Troublesho...
Troubleshooting network problems can be a very intensive and challenging process. Intermittent network problems are even more difficult to troubles...
Advanced Network Protocol Analyzer Review: Cola...
Firewall.cx has covered Colasoft Capsa several times in the past, but its constant improvements make it well worth revisiting. Since the last revie...
How To Detect ARP Attacks & ARP Flooding With C...
ARP attacks and ARP flooding are common problems small and large networks are faced with. ARP attacks target specific hosts by using their MAC addr...
Your IP address:
18.221.201.67
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!
Palo Alto Networks
Palo Alto Firewalls Security Zones – Tap Zone, Virtu...
Palo Alto Networks Next-Generation Firewalls rely on the concept of security zones in order to apply security policies. This means that access lists (fi...

Palo Alto Networks
Complete Guide: Configuring IPSec VPN between Palo A...
This article will show you how to configure an IPSec VPN tunnel between a Palo Alto firewall (all PANOS versions) and Meraki MX security appliance. Our ...

Palo Alto Networks
How to Manually Download, Import & Install PAN-OS on...
This article provides comprehensive guidance on the manual processes involved in downloading, uploading, and installing (import) any PAN-OS version on a...
Palo Alto Networks
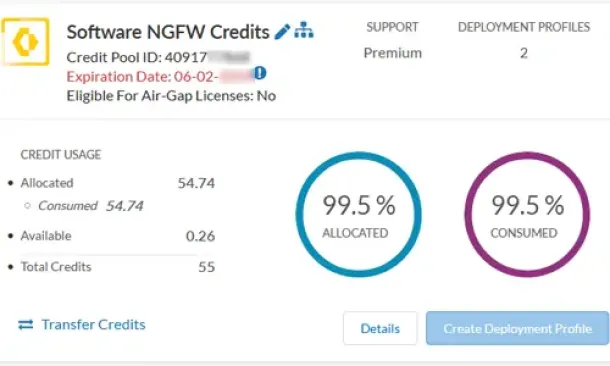
The Ultimate Guide to Palo Alto Networks Software NG...
Discover the ins and outs of using Palo Alto Networks’ Software NGFW (Flex) credits to seamlessly renew your cloud-based or virtualized software NGFW de...
Windows Servers
Windows 2003 DHCP Server Installation & Configuration
DHCP (Dynamic Host Configuration Protocol) is a protocol that allows clients on a network to request network configuration settings from a server runnin...
Windows Servers
How to Enable & Configure Shadow Copy for Shared Fol...
When you shadow copy a disk volume, you are actually generating a snapshot of the changes made to the folders and files within the disk volume at a cert...
Windows Servers
Hyper-V Best Practices - Replica, Cluster, Backup Ad...
Hyper-V has proven to be a very cost effective solution for server consolidation. Evidence of this is also the fact that companies are beginning to move...
Windows Servers
Windows Server 2016 VM Backup with Altaro's New VM B...
Altaro has released Altaro VM Backup, a faster and lighter upgrade to its flagship Hyper-V and VMware backup solution, which now supports all Windows Se...
Popular Topics
Virtualization & VM Backup
How to Enable or Disable SSH on VMware ESXi via Web ...
SSH access to VMware’s ESXi server is by disabled by default however there are many reasons where SSH might be required. VMware and System administrator...
Windows Servers
How to Easily Change Network Card Profile / Network ...
Network Location Awareness (NLA) is a feature offered on Windows Server 2012 R2 and all Windows workstation editions from Windows 8.1 and above, includi...

VLAN Networks
VTP Introduction & Modes
The invention of VLANs was very much welcomed by all engineers and administrators, allowing them to extend, redesign and segment their existing network ...
VLAN Networks
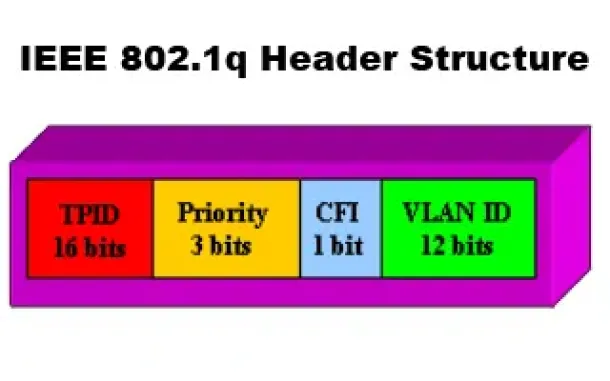
VLANs - IEEE 802.1q Trunk Link Protocol Analysis
While the VLAN Tagging article briefly covered the IEEE 802.1q protocol this article will continue building upon it by further analyzing the IEEE 802.1q...
Cisco Wireless
Cisco Aironet 1242AG /1240 - Multiple SSID & 802.1...
This article explains how the Cisco 1240 series access point can be setup to provide support for multiple SSID, each SSID assigned to a separa...
Cisco Services & Technologies
Cisco SmartCare Update - Next Generation Appliance
It's been more than a year since we introduced the Cisco SmartCare service and appliance. It's been extremely popular and has successfully penetrated th...
Cisco Routers
Cisco Router Password Recovery
Password recovery is a fairly frequently used procedure for administrators and engineers. Even though we usually stack our passwords in some word, excel...
Cisco Services & Technologies
Renewing Cisco Certifications without sitting for a ...
Without a doubt, Cisco certifications and specializations are among the most popular vendor certifications in the IT industry, and earning them doesn’t ...


















