Suggested Articles:
OpManager - Network Monitoring & Management
Ensuring Enterprise Network Readiness for Mobil...
Demands for Enterprise networks to properly support mobile users is on a continuous rise making it more than ever necessary for IT departments to p...

OpManager - Network Monitoring & Management
Maximizing Network Security: A Deep Dive into O...
In the rapidly evolving landscape of cyber threats, network security has never been more crucial. With the frequency and sophistication of cyberatt...
Network Protocol Analyzers
How to Perform TCP SYN Flood DoS Attack & Detec...
This article will help you understand TCP SYN Flood Attacks, show how to perform a SYN Flood Attack (DoS attack) using Kali Linux & hping3 and ...
Network Protocol Analyzers
How to Detect Routing Loops and Physical Loops ...
When working with medium to large scale networks, IT departments are often faced dealing with network loops and broadcast storms that are caused by...
Featured Subcategories:
WireShark Articles:
Improve Network Analysis Efficiency with Colaso...
Troubleshooting network problems can be a very difficult and challenging task. While most IT engineers use a network analyzer to help solve network...
How to Detect SYN Flood Attacks with Capsa Netw...
This article explains how to detect a SYN Flood Attack using an advanced protocol analyser like Colasoft Capsa. We’ll show you how to identify and ...
How to Detect P2P (peer-to-peer) File Sharing, ...
Peer-to-Peer file sharing traffic has become a very large problem for many organizations as users engage in illegal (most times) file sharing proce...
How to Reconstruct HTTP Packets/Data & Monitor ...
HTTP reconstruction is an advanced network security feature offered by nChronos version 4.3.0 and later. nChronos is a Network Forensic Analysis ap...
Your IP address:
3.17.9.140
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!

Palo Alto Networks
Complete Guide: Configuring IPSec VPN between Palo A...
This article will show you how to configure an IPSec VPN tunnel between a Palo Alto firewall (all PANOS versions) and Meraki MX security appliance. Our ...
Palo Alto Networks
Palo Alto Networks Firewall - Web & CLI Initial Conf...
This article is the second-part of our Palo Alto Networks Firewall technical articles. Our previous article was introduction to Palo Alto Networks Firew...

Palo Alto Networks
How to Manually Download, Import & Install PAN-OS on...
This article provides comprehensive guidance on the manual processes involved in downloading, uploading, and installing (import) any PAN-OS version on a...

Palo Alto Networks
Configuring QoS on Palo Alto Firewalls: Class-based ...
This article’s purpose is to help you quickly master Palo Alto QoS concepts and learn to configure QoS on Palo Alto Firewalls in a simple and efficient ...
Windows Servers
Creating Windows Users and Groups with Windows 2003
In a Windows server environment, it is very important that only authenticated users are allowed to log in for security reasons. To fulfill this requirem...
Windows Servers
Windows 2003 DHCP Server Advanced Configuration - Pa...
In this article, we will cover more advanced DHCP features and topics such as server options, superscopes, multicast scopes, dynamic DNS, DHCP database ...
Windows Servers
Free Webinar & eBook on Microsoft Licensing for Virt...
Microsoft Licensing for Virtual environments can become a very complicated topic, especially with all the misconceptions and false information out there...
Windows Servers
Windows Server 2016 Licensing Made Easy – Understand...
This article describes the new Windows Server 2016 Licensing model (per-core licensing) Microsoft has implemented for its new server-based operating sys...
Popular Topics
Windows Servers
Introduction To Windows Server 2012 R2 Virtualizatio...
FREE Hyper-V & VMware Backup: FREE for Firewall.cx readers for a Limited Time! Download Now!
Virtualization is an abstraction layer th...
Windows Servers
Easy, Fast & Reliable Hyper-V & VMware Backup with A...
As more companies around the world adopt the virtualization technology to increase efficiency and productivity, Microsoft’s Hyper-V virtualization platf...
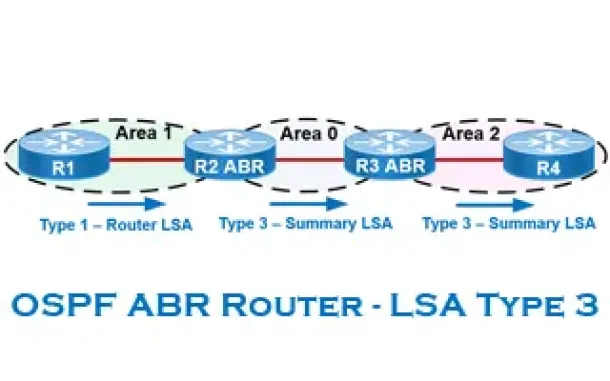
Routing
OSPF - Part 6: OSPF LSA Types - Purpose and Function...
Our previous article explained the purpose of Link State Update (LSU) packets and examined the Link State Advertisement (LSA) information contained with...

Network Fundamentals
Network Switches & Bridges
Network Switches are the evolution of Hubs and Repeaters, and enable the creation of networks by connecting multiple devices together. They are critical...
Cisco Routers
How To Configure Dynamic DNS Server On A Cisco Router
Hosting your own webserver or email server would normaly require a static IP address from your ISP. This ensures that your services are always reachable...
Cisco Services & Technologies
Comparing DMVPN Single Tier and Dual Tier Headend Ar...
This article extends our DMVPN article series by answering common questions regarding the differences between Single Tier Headend and Dual Tier Headend ...
Cisco Switches
Installation and Setup of Cisco SG500-52P - 500 Seri...
The SG500 series Cisco switches are the next step up from the already popular SG300 Layer-3 switches. Cisco introduced the SG Small Business series swit...
Cisco CallManager-CCME
Cisco Unity Express Installation/Setup - Service Mod...
Mentioned in Part-1 of our Cisco Unity Express installation article, the Cisco Unity Express setup procedure is identical for ISM-SRE-300-K9 and SM-SRE-...


















