Articles
To read the articles in this section, simply click on the article title or read button on the far right (if visible).
Use the below filters to customise the number of articles displayed or search for specific title topics/keywords.
| Articles | |
|---|---|
| Read | |
| Read | |
|
Articles:
Direct Cable Connection
| Read |
| Read | |
| Read | |
| Read | |
|
Articles:
Important Direct Cable Connection Notes
| Read |
| Read | |
|
Articles:
100Base-(T) TX/T4/FX - Ethernet
| Read |
|
Articles:
10Base-T/2/5/F/35 - Ethernet
| Read |
| Read | |
|
Articles:
Straight Thru UTP Cables
| Read |
| Read | |
Suggested Articles:
Domain Name System (DNS)
The DNS Protocol - Part 1: Introduction
If you ever wondered where DNS came from, this is your chance to find out ! The quick summary on DNS's history will also help you understand why DNS…
The OSI Model
The OSI Model: Layer 4 - Transport Layer
The Transport layer is responsible for providing mechanisms for multiplexing upper-layer application, session establishment, data transfer and tear d…
Network Cabling
10Base-T/2/5/F/35 - Ethernet
The 10Base-T UTP Ethernet and 10Base-2 Coax Ethernet were very popular in the early to mid 1990's when 100 Mbps network cards and hubs/switches were…
Subnetting
IP Subnetting - Part 4: Routing Between Subnets
Routing and Communication between subnets is the main topic here. This article analyses communications between subnets. We provide examples on differ…
Featured Subcategories:
Netflow Articles:
NetFlow Analyzer: Free Download, Step-by-Step Ins…
In our previous article we explained how a Netflow Analyzer can help you gain visibility into your user traffic, application traffic and data flows w…

Netflow: Monitor Bandwidth & Network Utilization…
Monitoring network traffic & bandwidth usage via Netflow is mandatory for any type and size network. Gaining visibility into user traffic, applic…
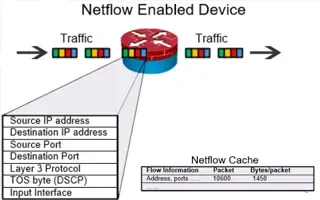
Complete Guide to Netflow: How Netflow & its Comp…
This article will cover the basics of Netflow, including its use cases, Netflow supported devices, Netflow history, and variants. We’ll also dive int…
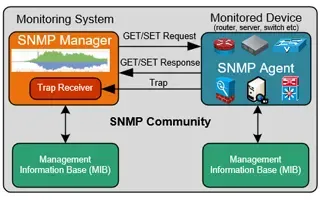
Netflow vs SNMP. Two Different Approaches to Netw…
SNMP (Simple Network Management Protocol) and Netflow are both popular protocols with admins, prized for their ability to give visibility over the ne…
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!

VLAN Networks
VLANs - Access & Trunk Links
If you've read our previous article The VLAN Concept - Introduction to VLANs then you should feel comfortable with terms such as 'VLAN', 'Stati…

VLAN Networks
VTP Pruning
VTP (VLAN Trunking Protocol) pruning is a feature that is used in Cisco switches to reduce unnecessary traffic in VLAN (Virtual Local Area Network) trunks…

VLAN Networks
InterVLAN Routing - Routing between VLAN Networks
This article deals with the popular topic of InterVLAN routing, which is used to allow routing & communication between VLAN networks. Our article anal…
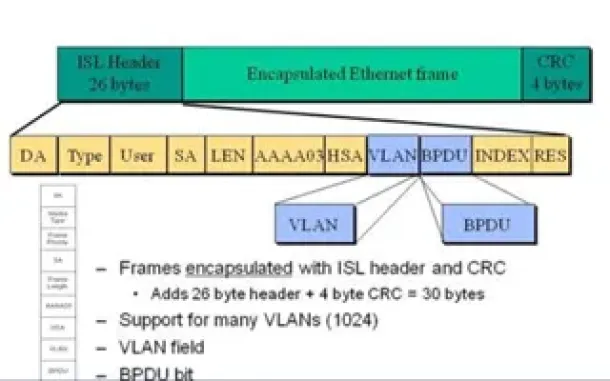
VLAN Networks
VLAN InterSwitch Link (ISL) Protocol Analysis
Deciding whether to use ISL or IEEE 802.1q to power your trunk links can be quite confusing if you cannot identify the advantages and disadvantages of eac…
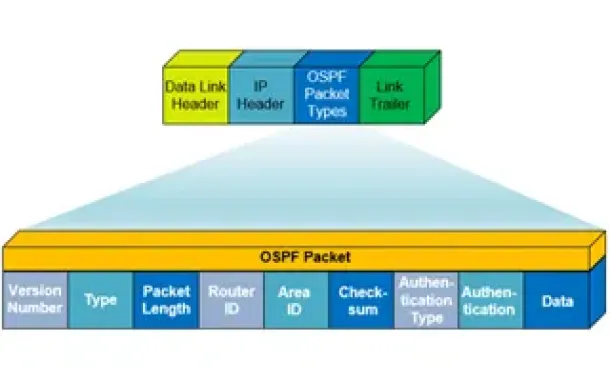
Routing
OSPF - Part 1: Introduction, OSPF Packet Structure, OS…
Open Shortest Path First (OSPF) is a popular routing protocol developed for Internet Protocol (IP) networks by the Interior Gateway Protocol (IGP) working…
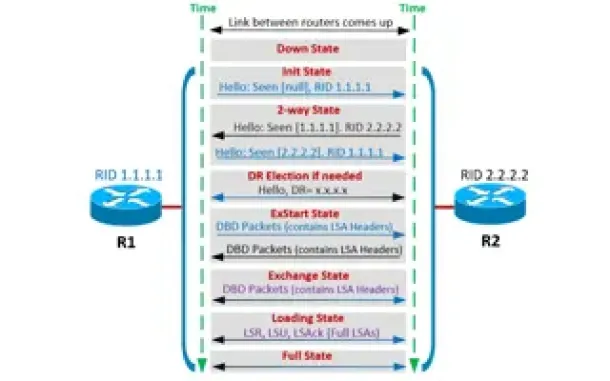
Routing
OSPF - Part 4: OSPF Neighbor States – OSPF Neighbor Fo…
This is the third article of our OSPF series which analyzes the different OSPF States routers go through during the OSPF discovery and neighbor forming pr…
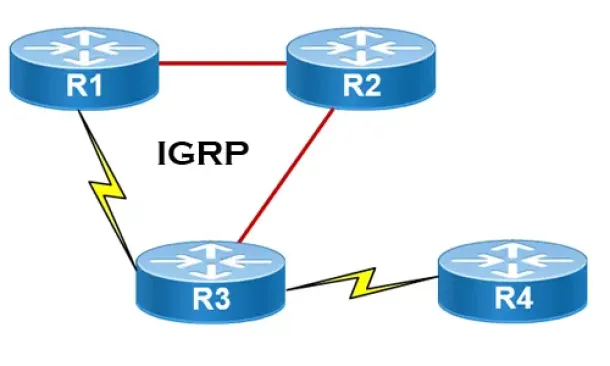
Routing
Interior Gateway Protocol - IGRP
IGRP (Interior Gateway Routing Protocol) is a Cisco proprietary distance-vector routing protocol used in enterprise networks to exchange routing informati…
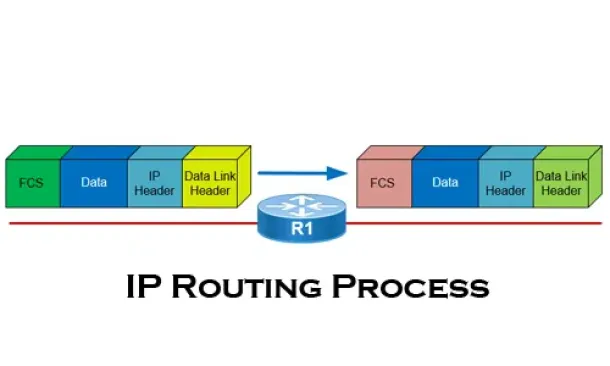
Routing
The IP Routing Process - Step-by-Step Analysis
We are going to analyse what happens when routing occurs on a network (IP routing process). When I was new to the networking area, I thought that all you…
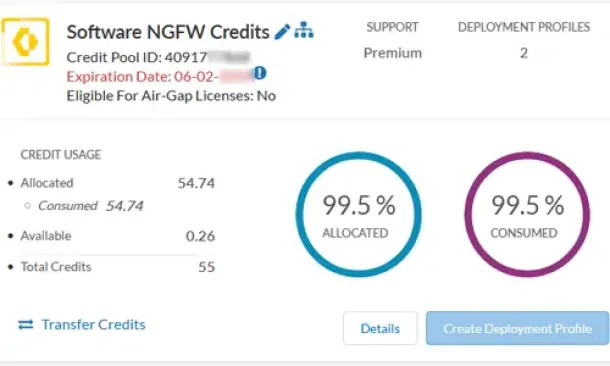
Palo Alto Networks
The Ultimate Guide to Palo Alto Networks Software NGFW…
Discover the ins and outs of using Palo Alto Networks’ Software NGFW (Flex) credits to seamlessly renew your cloud-based or virtualized software NGFW devi…
Windows Servers
Introduction To Windows Server 2012 R2 Virtualization…
FREE Hyper-V & VMware Backup: FREE for Firewall.cx readers for a Limited Time! Download Now!
Virtualization is an abstraction layer that…
Cisco Routers
MPLS Case Study: Why Route Summarization is not Recomm…
MPLS generates Implicit Null label (The Implicit NULL label is the label that has a value of 3) for directly connected interfaces and for the summary rout…
Cisco Routers
Configuring Cisco SSL VPN AnyConnect (WebVPN) on Cisco…
Our Web SSL VPN article written back in 2011 introduced this new wave of VPN services. This article extends the topic by covering the installation a…



















