Network Management Articles:

ManageEngine Firewall Analyzer
7 Essential Firewall Management Strategies for ...
A firewall appliance is a fundamental pillar of network security, acting as the first line of defense against cyber threats. However, its strength is only as good as its configuration, monitoring...
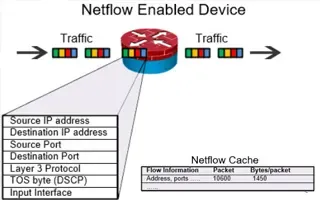
Netflow
Complete Guide to Netflow: How Netflow & its Co...
This article will cover the basics of Netflow, including its use cases, Netflow supported devices, Netflow history, and variants. We’ll also dive into the technical details of how the Netflow proto...

ManageEngine Firewall Analyzer
Ensuring Compliance and Business Continuity in ...
In the wake of digital transformation, the work landscape as we know it has undergone a dynamic shift. People can now work from home, from the office, or anywhere with a stable internet connection....

Netflow
Netflow: Monitor Bandwidth & Network Utilizatio...
Monitoring network traffic & bandwidth usage via Netflow is mandatory for any type and size network. Gaining visibility into user traffic, application traffic and data flows allows network engi...
Featured Subcategories:
Network Protocol Analyzer Articles:
Network Protocol Analyzers
How To Detect ARP Attacks & ARP Flooding With C...
ARP attacks and ARP flooding are common problems small and large networks are faced with. ARP attacks target specific hosts by using their MAC address and responding on their behalf, while at the s...
Network Protocol Analyzers
How to Detect SYN Flood Attacks with Capsa Netw...
This article explains how to detect a SYN Flood Attack using an advanced protocol analyser like Colasoft Capsa. We’ll show you how to identify and inspect abnormal traffic spikes, drill into captur...
Network Protocol Analyzers
How to Detect P2P (peer-to-peer) File Sharing, ...
Peer-to-Peer file sharing traffic has become a very large problem for many organizations as users engage in illegal (most times) file sharing processes that not only consumes valuable bandwidth, bu...
Network Protocol Analyzers
Detect Brute-Force Attacks with nChronos Networ...
Brute-force attacks are commonly known attack methods by which hackers try to get access to restricted accounts and data using an exhaustive list/database of usernames and passwords. Brute-force at...
Virtualization & VM Backup:
Virtualization & VM Backup
How to Enable or Disable SSH on VMware ESXi via...
SSH access to VMware’s ESXi server is by disabled by default however there are many reasons where SSH might be required. VMware and System administrators often find the need to perform advanced adm...
Virtualization & VM Backup
5 Most Critical Microsoft M365 Vulnerabilities ...
Microsoft 365 is an incredibly powerful software suite for businesses, but it is becoming increasingly targeted by people trying to steal your data. The good news is that there are plenty of ways a...
Virtualization & VM Backup
SysAdmin Day 2020 - Get your Free Amazon Vouche...
SysAdmin Day has arrived, and with it, gratitude for all the unsung heroes that 2020 has needed. Your hard work has made it possible for all of us to keep going, despite all challenges thrown our w...

Virtualization & VM Backup
Ultimate Guide: Install Windows 11 on VMware ES...
In this article, we’ll show you how to setup or install Microsoft Windows 11 on VMware’s ESXi servers and bypass the Trusted Platform Module version 2.0 (TPM 2.0) requirement. We've also made the&n...
Firewall Articles:
Cisco Firewalls
Understand & Configure NAT Reflection, NAT Loop...
This article examines the concept of NAT Reflection, also known as NAT Loopback or Hairpinning, and shows how to configure a Cisco ASA Firewall running ASA version 8.2 and earlier plus ASA version ...
Palo Alto Networks
Complete Guide to Upgrading Palo Alto Firewall ...
Upgrading your Palo Alto Firewall or Panorama Management System to the preferred PAN-OS release is always recommended as it ensures it remains stable, safe from known vulnerabilities and exploits b...
Cisco Firewalls
Demystifying Cisco AnyConnect 4.x Licensing. Pl...
In late 2014, Cisco announced the new licensing model for the latest AnyConnect Secure Mobility client v4.x. With this new version, Cisco introduced a number of new features, but also simplified th...
Palo Alto Networks
Palo Alto Firewall Application-based Policy Enf...
Our previous article examined the benefits of Palo Alto Networks Firewall Single Pass Parallel Processing (SP3) architecture and how its combine with the separate Data and Control planes to boost f...
Your IP address:
3.17.142.93
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!
Top Picks
Windows Servers
Active Directory Tombstone Lifetime Modification
Tombstone is a container object that contains the deleted objects from Active Directory. Actually when an object is deleted from Active Directory, ...
Network Address Translation - NAT
Network Address Translation (NAT) Overload - Part 1
NAT Overload is the most common NAT method used throughout all networks that connect to the Internet. This is because of the way it functions and t...
Cisco Routers
Cisco Router 'Privileged' Mode
To get into Privileged Mode we enter the "Enable" command from User Exec Mode. If set, the router will prompt you for a password. Once in Privilege...
Network Address Translation - NAT
Dynamic NAT - Part 1
Dynamic NAT is the second NAT mode we're going to talk about. Dynamic NAT, like Static NAT, is not that common in smaller networks but you'll find ...


















