Articles
To read the articles in this section, simply click on the article title or read button on the far right (if visible).
Use the below filters to customise the number of articles displayed or search for specific title topics/keywords.
| Articles | |
|---|---|
| Read | |
| Read | |
| Read | |
|
Articles:
The DNS Protocol - Part 1: Introduction
| Read |
Suggested Articles:
Ethernet Protocol, CSMA/CD, Collisions
802.3 Fast Ethernet (100 Mbit/Sec) Model
Here we see a logical drawing of the Fast Ethernet Data Link Layer sublayers. Data is passed down from the upper layers (such as TCP/IP or Novell N...
TCP - UDP Protocol Analysis
Transmission Control Protocol - Part 4: In-Dept...
This article is an introduction to the 7-page TCP Header analysis section that follows. We briefly view each section of the TCP Header and then mov...
Network Cabling
Unshielded Twisted Pair (UTP) - CAT 1 to CAT5, ...
Unshielded Twisted Pair (UTP) cable is most certainly by far the most popular cable around the world. UTP cable is used not only for networking but...
Network Protocols
Introduction To The ISDN Protocol
ISDN (Integrated Services Digital Network) is a digital telephone standard designed to replace analogue connections by utilising ordinary copper wi...
Featured Subcategories:
Netflow Articles:
NetFlow Analyzer: Free Download, Step-by-Step I...
In our previous article we explained how a Netflow Analyzer can help you gain visibility into your user traffic, application traffic and data flows...

Netflow: Monitor Bandwidth & Network Utilizatio...
Monitoring network traffic & bandwidth usage via Netflow is mandatory for any type and size network. Gaining visibility into user traffic, appl...
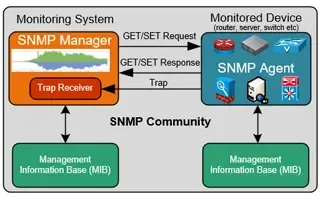
Netflow vs SNMP. Two Different Approaches to Ne...
SNMP (Simple Network Management Protocol) and Netflow are both popular protocols with admins, prized for their ability to give visibility over the ...
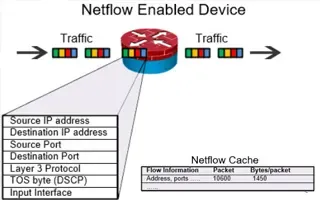
Complete Guide to Netflow: How Netflow & its Co...
This article will cover the basics of Netflow, including its use cases, Netflow supported devices, Netflow history, and variants. We’ll also dive i...
Your IP address:
3.14.152.212
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!

VLAN Networks
Static VLANs
VLANs are usually created by the network administrator, assigning each port of every switch to a VLAN. Depending on the network infrastructure and secur...

VLAN Networks
InterVLAN Routing - Routing between VLAN Networks
This article deals with the popular topic of InterVLAN routing, which is used to allow routing & communication between VLAN networks. Our article an...

VLAN Networks
Dynamic VLANs
Dynamic VLANs were introduced to grant the flexibility and complexity(!) that Static VLANs did not provide. Dynamic VLANs are quite rare because of thei...
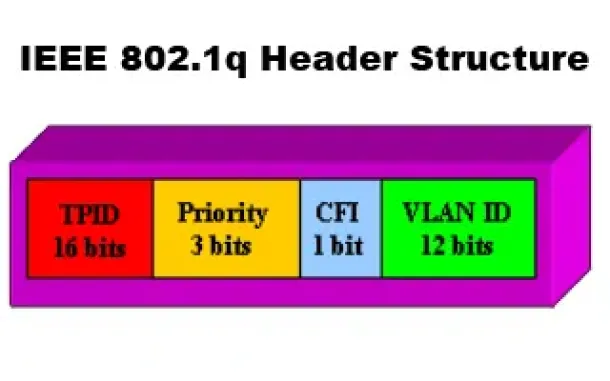
VLAN Networks
VLANs - IEEE 802.1q Trunk Link Protocol Analysis
While the VLAN Tagging article briefly covered the IEEE 802.1q protocol this article will continue building upon it by further analyzing the IEEE 802.1q...
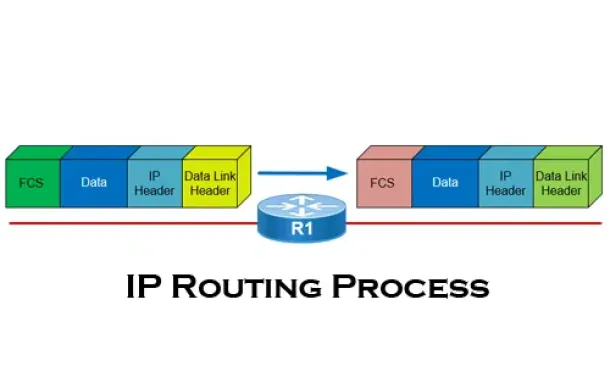
Routing
The IP Routing Process - Step-by-Step Analysis
We are going to analyse what happens when routing occurs on a network (IP routing process). When I was new to the networking area, I thought that all yo...
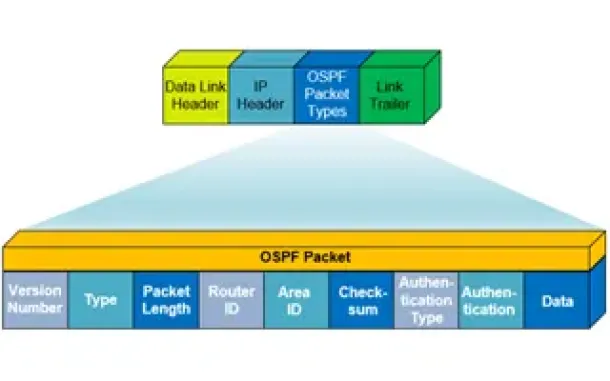
Routing
OSPF - Part 1: Introduction, OSPF Packet Structure, ...
Open Shortest Path First (OSPF) is a popular routing protocol developed for Internet Protocol (IP) networks by the Interior Gateway Protocol (IGP) worki...
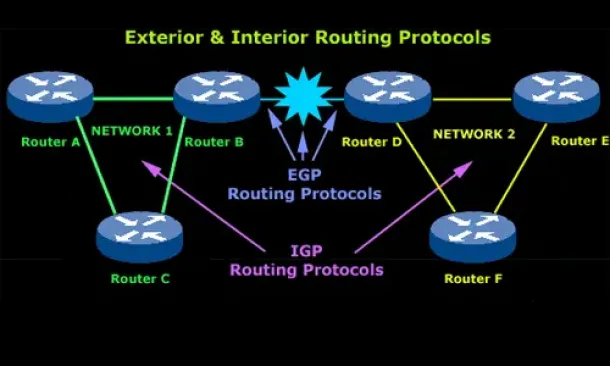
Routing
Introduction to Routing Protocols
Distance Vector, Link State RIP, IGRP, EIGRP, OSPF
Routing protocols were created for routers. These protocols have been designed to allow the exchan...
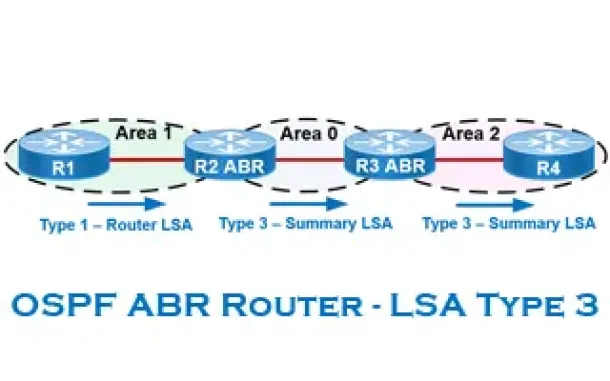
Routing
OSPF - Part 6: OSPF LSA Types - Purpose and Function...
Our previous article explained the purpose of Link State Update (LSU) packets and examined the Link State Advertisement (LSA) information contained with...
Windows Servers
Download Altaro Free VM Backup & Win a PlayStation 4...
We have some exciting news for you today!
Altaro has launched a great contest in celebration of SysAdmin Day on 27th July!
They will be giving away Am...
Cisco Switches
Cisco Catalyst 4500 Series Zero-Downtime IOS Upgrade...
The Supervisor Engine is the heart of the Cisco Catalyst 4500 and 6500 series switches. It is the equivalent of an engine in a car. Every packet that en...
Network Protocol Analyzers
Introducing Colasoft Unified Performance Management
Colasoft Unified Performance Management (UPM) is a business-oriented network performance management system, which analyzes network performance, quality,...
Cisco Wireless
Cisco Wireless Controllers (WLC) Datasheets Availabl...
We would like to inform our readers that Firewall.cx has just made available as a free download all of Cisco's Wireless Controller Datasheets.
The data...


















