Suggested Articles:
Subnetting
IP Subnet Calculator
This free online Subnet Calculator provides a fast and easy way to calculate all aspects of any IP Address and Subnet Mask. Simply enter your desir…
Network Cabling
100Base-(T) TX/T4/FX - Ethernet
The 100Base-TX (sometimes referred to 100Base-T) cable was until 2010 perhaps the most popular cable around since it has actually replaced the older…
Network Address Translation - NAT
Dynamic NAT - Part 1
Dynamic NAT is the second NAT mode we're going to talk about. Dynamic NAT, like Static NAT, is not that common in smaller networks but you'll find it…

Spanning Tree Protocol (STP)
Spanning Tree Protocol – Part 1: Understand STP P…
One of the most used terms in network is LAN (Local Area Network). It’s a form of network that we encounter in our daily lives, at home, at work, stu…
Featured Subcategories:
Netflow Articles:
NetFlow Analyzer: Free Download, Step-by-Step Ins…
In our previous article we explained how a Netflow Analyzer can help you gain visibility into your user traffic, application traffic and data flows w…

Netflow: Monitor Bandwidth & Network Utilization…
Monitoring network traffic & bandwidth usage via Netflow is mandatory for any type and size network. Gaining visibility into user traffic, applic…
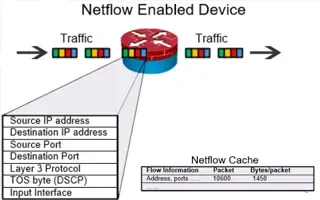
Complete Guide to Netflow: How Netflow & its Comp…
This article will cover the basics of Netflow, including its use cases, Netflow supported devices, Netflow history, and variants. We’ll also dive int…
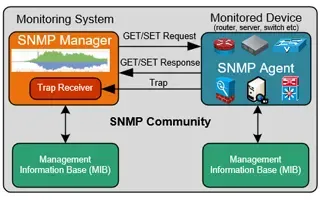
Netflow vs SNMP. Two Different Approaches to Netw…
SNMP (Simple Network Management Protocol) and Netflow are both popular protocols with admins, prized for their ability to give visibility over the ne…
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!

VLAN Networks
VTP Pruning
VTP (VLAN Trunking Protocol) pruning is a feature that is used in Cisco switches to reduce unnecessary traffic in VLAN (Virtual Local Area Network) trunks…
VLAN Networks
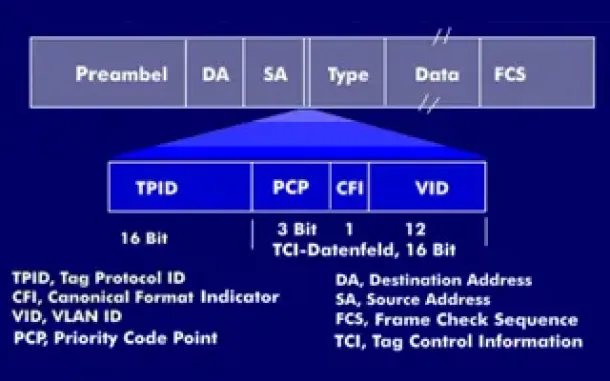
VLAN Tagging - Understanding VLANs Ethernet Frames
We mentioned that Trunk Links are designed to pass frames (packets) from all VLANs, allowing us to connect multiple switches together and independently co…

VLAN Networks
VLANs - IEEE 802.1q Trunk Link Protocol Analysis
While the VLAN Tagging article briefly covered the IEEE 802.1q protocol this article will continue building upon it by further analyzing the IEEE 802.1q T…

VLAN Networks
VTP Protocol - In-Depth Analysis
The previous article introduced the VTP protocol, we examined how it can be used within a network, to help manage VLANs and ease the administrative overhe…
Routing
Distance Vector Routing Protocols
Distance Vector routing protocols use frequent broadcasts (255.255.255.255 or FF:FF:FF:FF) of their entire routing table every 30 sec. on all their interf…
Routing
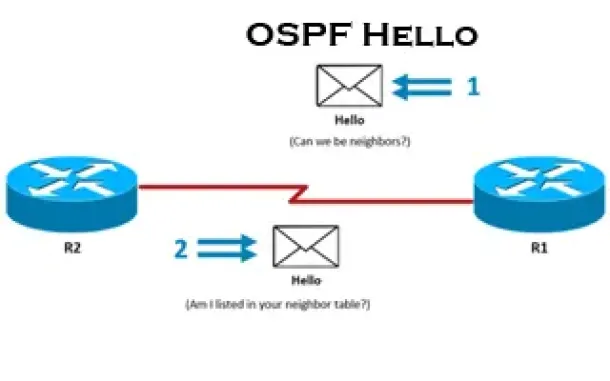
OSPF - Part 3: OSPF Adjacency & Neighbor Forming Proce…
This is the thrid article of our 6-part OSPF series (see below) that describes how OSPF routers perform neighbor relationship and adjacency. We’ll examine…
Routing
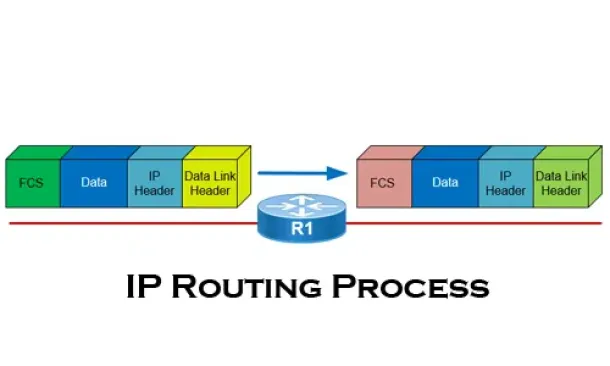
The IP Routing Process - Step-by-Step Analysis
We are going to analyse what happens when routing occurs on a network (IP routing process). When I was new to the networking area, I thought that all you…
Routing
Interior Gateway Protocol - IGRP
IGRP (Interior Gateway Routing Protocol) is a Cisco proprietary distance-vector routing protocol used in enterprise networks to exchange routing informati…
Cisco Wireless
Wireless (Wifi) WEP WPA WPA2 Key Generator
The Firewall.cx Wireless LAN Key Generator will allow the generation of a WEP or WPA ASCII based encryption key and will provide the equivalent HEX or…
Virtualization & VM Backup
5 Most Critical Microsoft M365 Vulnerabilities Reveale…
Microsoft 365 is an incredibly powerful software suite for businesses, but it is becoming increasingly targeted by people trying to steal your data. The g…
Windows Servers
Free Webinar: Migrating from Hyper-V to VMware
If your organization is planning to migration from a Hyper-V virtualization environment to VMware then this FREE webinar is just for you.
Aimed toward Hy…
Cisco Firewalls
Demystifying Cisco AnyConnect 4.x Licensing. Plus, Plu…
In late 2014, Cisco announced the new licensing model for the latest AnyConnect Secure Mobility client v4.x. With this new version, Cisco introduced a num…



















