Suggested Articles:

EventLog Analyzer
Unlock Deep Visibility & Insight into Windows S...
This article explores the exciting new features of Windows Server 2022 and emphasizes the critical role of analyzing Windows Server logs. You'll al...
Network Protocol Analyzers
How To Detect ARP Attacks & ARP Flooding With C...
ARP attacks and ARP flooding are common problems small and large networks are faced with. ARP attacks target specific hosts by using their MAC addr...

OpManager - Network Monitoring & Management
Optimizing Cisco Router Performance: Best Pract...
Effective monitoring and management of Cisco routers and network devices are essential for ensuring a robust and efficient network infrastructure. ...

ManageEngine Firewall Analyzer
Discover the Ultimate Firewall Management Tool:...
Firewall security management is a combination of monitoring, configuring, and managing your firewall to make sure it runs at its best to effectivel...
Featured Subcategories:
WireShark Articles:
How to Detect SYN Flood Attacks with Capsa Netw...
This article explains how to detect a SYN Flood Attack using an advanced protocol analyser like Colasoft Capsa. We’ll show you how to identify and ...
Introducing Colasoft Unified Performance Manage...
Colasoft Unified Performance Management (UPM) is a business-oriented network performance management system, which analyzes network performance, qua...
Advanced Network Protocol Analyzer Review: Cola...
Firewall.cx has covered Colasoft Capsa several times in the past, but its constant improvements make it well worth revisiting. Since the last revie...
How to Detect P2P (peer-to-peer) File Sharing, ...
Peer-to-Peer file sharing traffic has become a very large problem for many organizations as users engage in illegal (most times) file sharing proce...
Your IP address:
18.225.95.186
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!
Palo Alto Networks
Complete Guide to Upgrading Palo Alto Firewall PAN-O...
Upgrading your Palo Alto Firewall or Panorama Management System to the preferred PAN-OS release is always recommended as it ensures it remains stable, s...
Palo Alto Networks
Palo Alto Firewalls Security Zones – Tap Zone, Virtu...
Palo Alto Networks Next-Generation Firewalls rely on the concept of security zones in order to apply security policies. This means that access lists (fi...
Palo Alto Networks
Palo Alto Firewall Application-based Policy Enforcem...
Our previous article examined the benefits of Palo Alto Networks Firewall Single Pass Parallel Processing (SP3) architecture and how its combine with th...
Palo Alto Networks
Palo Alto Networks Firewall - Web & CLI Initial Conf...
This article is the second-part of our Palo Alto Networks Firewall technical articles. Our previous article was introduction to Palo Alto Networks Firew...
Windows Servers
How to Install Desktop Icons (Computer, User’s Files...
One of the first things IT Administrators and IT Managers notice after a fresh installation of Windows 2012 Server is that there are no Desktop Icons ap...
Windows Servers
How to Install Windows 2012 Hyper-V via Server Manag...
Our previous article covered the basic concepts of Virtualization and Windows Server 2012 Hyper-V. This article takes a closer look at Microsoft’s...
Windows Servers
Hyper-V Best Practices - Replica, Cluster, Backup Ad...
Hyper-V has proven to be a very cost effective solution for server consolidation. Evidence of this is also the fact that companies are beginning to move...
Windows Servers
Easy, Fast & Reliable Hyper-V & VMware Backup with A...
As more companies around the world adopt the virtualization technology to increase efficiency and productivity, Microsoft’s Hyper-V virtualization platf...
Popular Topics
SASE & SD-WAN Networks
Converged SASE Backbone – How Leading SASE Provider,...
Global connectivity is top of mind for many IT teams at organizations of all sizes. We are currently in the middle of a dramatic shift in business and t...
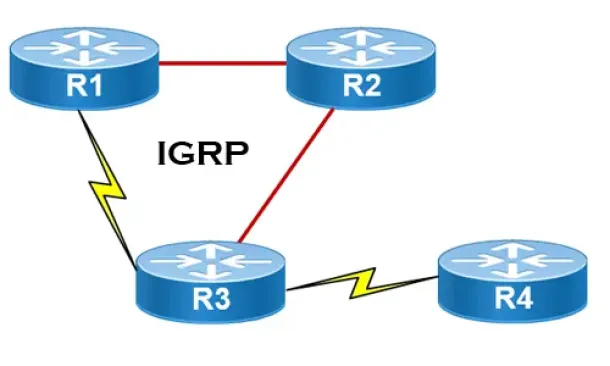
Routing
Interior Gateway Protocol - IGRP
IGRP (Interior Gateway Routing Protocol) is a Cisco proprietary distance-vector routing protocol used in enterprise networks to exchange routing informa...
Virtualization & VM Backup
How to Fix VMware ESXi Virtual Machine 'Invalid Status'
In this article, we'll show you how to deal with VMs which are reported to have an Invalid Status as shown in the screenshot below. This is a commo...

Network Fundamentals
Measuring Network Performance: Test Network Throughp...
Measuring network performance has always been a difficult and unclear task, mainly because most engineers and administrators are unsure which approach i...
Cisco Wireless
Cisco Aironet 1100 & 1200 Series (1110, 1121, 1142, ...
Resetting a Cisco Aironet access point can be required if you’ve lost your password or need to wipe out the configuration of a previously configured acc...
Cisco CallManager-CCME
Cisco CallManager Express Basic Concepts - Part 2
Our previous article, Cisco CallManager Express Basic Concepts - Part 1 covered the very basic concepts of CCME and its operation. This article continue...
Cisco Routers
Cisco Router PPP Multilink Setup and Configuration
This article provides an in-depth explanation of PPP Multilink and shows how to configure a Cisco router to use PPP Multilink between two serial interfa...
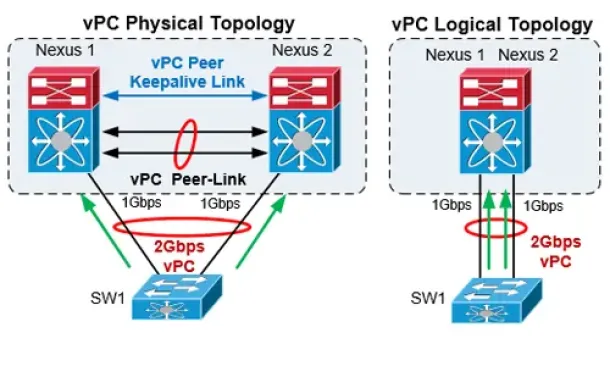
Cisco Data Center (Nexus/UCS)
The Complete Cisco Nexus vPC Guide. Features & Advan...
Cisco virtual Port Channel (vPC) is a virtualization technology, launched in 2009, which allows links that are physically connected to two different Cis...


















