How to Detect P2P (peer-to-peer) File Sharing, Torrent Traffic & Users with a Network Analyzer
 Peer-to-Peer file sharing traffic has become a very large problem for many organizations as users engage in illegal (most times) file sharing processes that not only consumes valuable bandwidth, but also places the organization in danger as high-risk connections are made from the Internet to the internal network and malware, pirated or copyrighted material or pornography is downloaded into the organization’s systems. The fact is that torrent traffic is responsible for over 29% of US Internet's traffic in North America, indicating how big the problem is.
Peer-to-Peer file sharing traffic has become a very large problem for many organizations as users engage in illegal (most times) file sharing processes that not only consumes valuable bandwidth, but also places the organization in danger as high-risk connections are made from the Internet to the internal network and malware, pirated or copyrighted material or pornography is downloaded into the organization’s systems. The fact is that torrent traffic is responsible for over 29% of US Internet's traffic in North America, indicating how big the problem is.
To help network professionals in the P2P battle, we’ll show how Network Analyzers such as Colasoft Capsa, can be used to identify users or IP addresses involved the file sharing process, allowing IT departments to take the necessary actions to block users and similair activities.
While all network analyzers capture and display packets, very few have the ability to display P2P traffic or users creating multiple connections with remote peers - allowing network administrators to quickly and correctly identify P2P activity.
Visit our Network Protocol Analyzer Section for high-quality technical articles covering Wireshark topics, detecting and creating different type of network attacks plus many more great security articles.
One of the main traffic characteristics of P2P host traffic is that they create many connections to and from hosts on the Internet, in order to download from multiple sources or upload to multiple destinations.
Apart from using the correct tools, network administrators and engineers must also ensure they capture traffic at strategic areas within their network. This means that the network analyzer must be placed at the point where all network traffic, to and from the Internet, passes through it.
The two most common places network traffic is captured is at the router/firewall connecting the organization to the Internet or the main switch where the router/firewall device connects to. To learn how to configure these devices and enable the network analyzer to capture packets, visit the following articles:
- Configuring SPAN On Cisco Catalyst Switches - Monitor & Capture Network Traffic/Packets
- How to Capture Packets on your Cisco Router with Embedded Packet Capture - Configuration, Troubleshooting & Data Export
While capturing commences, data will start being displayed in Capsa, and thanks to the Matrix display feature, we can quickly identify hosts that have multiple conversations or connections with peer hosts on the Internet.
By selecting the Matrix tab and hovering the mouse on a host of interest (this also automatically selects the host), Capsa will highlight all conversations with other IP addresses made by the selected host, while at the same time provide additional useful information such as bytes sent and received by the host, amount of peer connections (extremely useful!) and more:
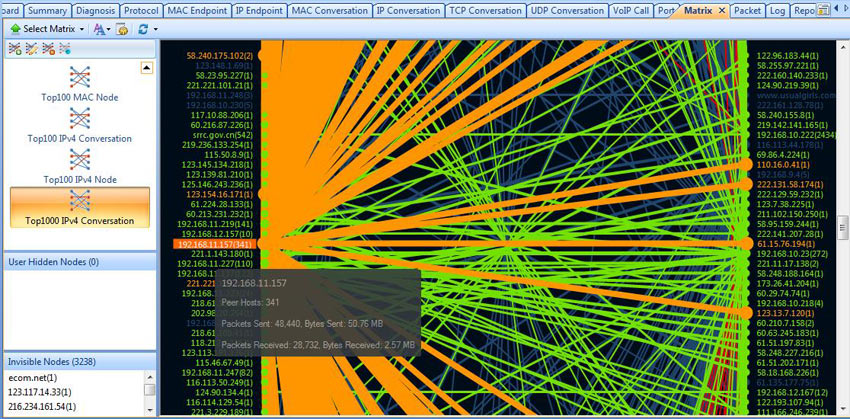
Figure 1. Using the Capsa Matrix feature to highlight conversations of a specific host suspected of P2P traffic
In most cases, an excessive amount of peer connections means that there is a P2P application running, generating all the displayed traffic and connections.
Next, to drill into to the host's traffic, simply click on the Protocol tab to automatically show the amount of traffic generated by each protocol. Here we will happily find the BitTorrent & eMule protocol listed:
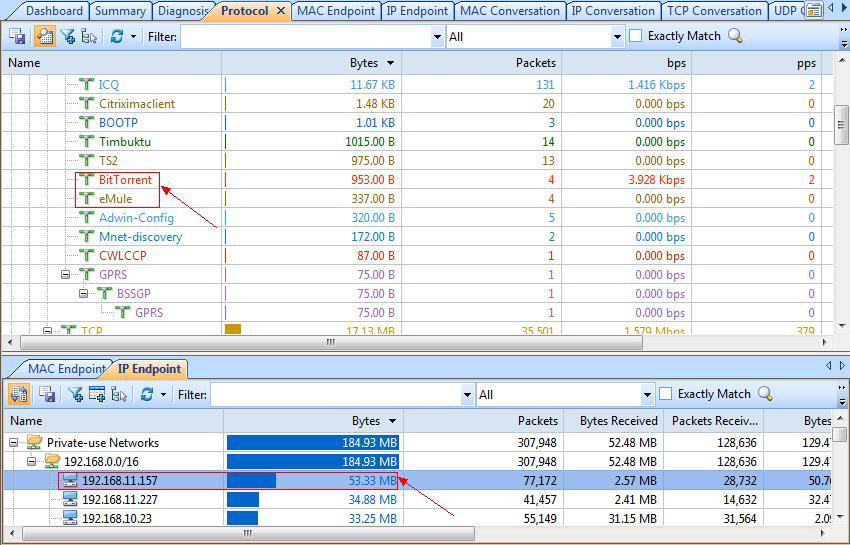
Figure 2. Identifying P2P Traffic and associated hosts in Capsa Network Analyzer
The IP Endpoint tab below provides additional useful information such as IP address, bytes of traffic associated with the host, number of packets, total amount of bytes and more.
By double-clicking on the host of interest (under IP EndPoint), Capsa will open a separate window and display all data captured for the subject host, allowing extensive in-depth analysis of packets:
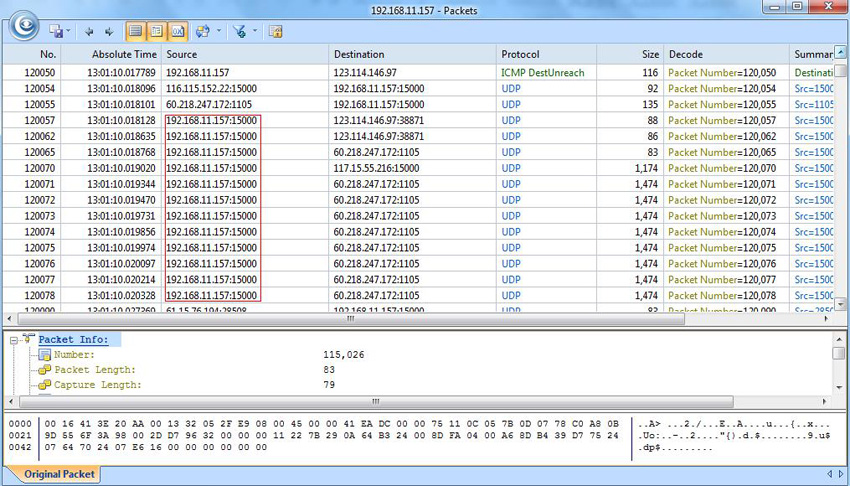
Figure 3. Diving into a host’s captured packets with the help of Capsa Network Analyzer
Multiple UDP conversations through the same port, indicate that there may be a P2P download or upload in progress.
Further inspection of packet information such as info hash, port, remote peer(s), etc. in ASCII decoding mode will confirm the capture traffic is indeed from P2P traffic.
This article demonstrated how Capsa network analyser can be used to detect Peer-to-Peer (P2P) traffic in a network environment. We examined the Matrix feature of Capsa, plus its ability to automatically identify P2P/Torrent traffic, making it easier for network administrators to track down P2P clients within their organization.
Your IP address:
18.191.74.140
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!













