Network Fundamentals: Top Picks
Network Fundamentals
Introduction To Networking
A network is simply a group of two or more Personal Computers linked together. Many types of networks exist, but the most common types of networks ...
Network Fundamentals
Media Access Control - MAC Addresses
A MAC address, or Media Access Control address, is a unique identifier assigned to a network interface controller (NIC) for use as a network addr...
Network Fundamentals
Hubs & Repeaters
Network hubs were once the primary method of interconnecting network devices to create a local area network (LAN). Hubs were inexpensive, easy to i...
Network Fundamentals
The Importance of a Network Analyzer – Packet S...
Network Analyzers, also known as Packet Sniffers, are amongst the most popular network tools found inside any Network Engineer’s toolkit. A Network...
Featured Subcategories:
Netflow Articles:
Netflow
Netflow: Monitor Bandwidth & Network Utilizatio...
Monitoring network traffic & bandwidth usage via Netflow is mandatory for any type and size network. Gaining visibility into user traffic, appl...
Netflow
NetFlow Analyzer: Free Download, Step-by-Step I...
In our previous article we explained how a Netflow Analyzer can help you gain visibility into your user traffic, application traffic and data flows...
Netflow
Netflow vs SNMP. Two Different Approaches to Ne...
SNMP (Simple Network Management Protocol) and Netflow are both popular protocols with admins, prized for their ability to give visibility over the ...
Netflow
Complete Guide to Netflow: How Netflow & its Co...
This article will cover the basics of Netflow, including its use cases, Netflow supported devices, Netflow history, and variants. We’ll also dive i...
Network Protocols:
Subnetting
IP Subnetting - Part 2: Subnet Masks & Their Ef...
There are a few different ways to approach subnetting and it can get confusing because of the complexity of some subnets and the flexibility they o...
Domain Name System (DNS)
The DNS Protocol - Part 3: DNS Query Message Fo...
This section will deal with the analysis of the DNS packets by examining how DNS messages are formatted and the options and variables they contain....
TCP - UDP Protocol Analysis
Transmission Control Protocol - Part 1: Introdu...
Understanding how each protocol fits into the OSI Model is essential for any network engineer. This page analyses how TCP is classified as a 'trans...
TCP - UDP Protocol Analysis
TCP Header Anaylsis - Section 1: TCP Source & D...
This section contains one of the most well-known fields in the TCP header, the Source and Destination port numbers. These fields are used to specif...
Domain Name System (DNS)
The DNS Protocol - Part 2: DNS Queries & Resolu...
This section will help you understand how the DNS queries work on the Internet and your home network. There are two ways to use the domain name sys...
TCP - UDP Protocol Analysis
TCP Header Anaylsis - Section 6: TCP Options
The TCP Options (MSS, Window Scaling, Selective Acknowledgements, Timestamps, Nop) are located at the end of the TCP Header which is also why they ...
Domain Name System (DNS)
The DNS Protocol - Part 1: Introduction
If you ever wondered where DNS came from, this is your chance to find out ! The quick summary on DNS's history will also help you understand why DN...
Subnetting
IP Subnetting - Part 4: Routing Between Subnets
Routing and Communication between subnets is the main topic here. This article analyses communications between subnets. We provide examples on diff...
STP/ICMP Protocols:
ICMP Protocol
ICMP Protocol - Part 4: Destination Unreachable...
The 'ICMP Destination unreachable' message is quite interesting, because it doesn't actually contain one message, but infact six! This means that t...
ICMP Protocol
ICMP Protocol - Part 1: Introduction
The Internet Control Message Protocol (ICMP), is a very popular protocol and actually part of an Internet Protocol (IP) implementation. Because IP ...
ICMP Protocol
ICMP Protocol - Part 5: Source Quench Message A...
The ICMP - Source Quench message is one that can be generated by either a gateway or host. You won't see any such message pop up on your workstatio...
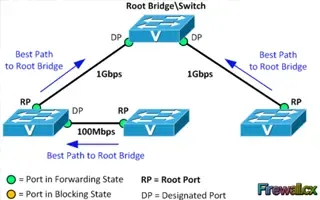
Spanning Tree Protocol (STP)
Spanning Tree Protocol – Part 2: Rapid STP Port...
Spanning Tree Protocol, Rapid STP port costs and port states are an essential part of the STP algorithm that affect how STP decides to forward or b...
Your IP address:
3.139.90.0
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!

VLAN Networks
VTP Introduction & Modes
The invention of VLANs was very much welcomed by all engineers and administrators, allowing them to extend, redesign and segment their existing network ...
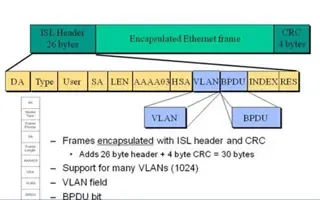
VLAN Networks
VLAN InterSwitch Link (ISL) Protocol Analysis
Deciding whether to use ISL or IEEE 802.1q to power your trunk links can be quite confusing if you cannot identify the advantages and disadvantages of e...

VLAN Networks
VTP Protocol - In-Depth Analysis
The previous article introduced the VTP protocol, we examined how it can be used within a network, to help manage VLANs and ease the administrative over...

VLAN Networks
VLANs - IEEE 802.1q Trunk Link Protocol Analysis
While the VLAN Tagging article briefly covered the IEEE 802.1q protocol this article will continue building upon it by further analyzing the IEEE 802.1q...
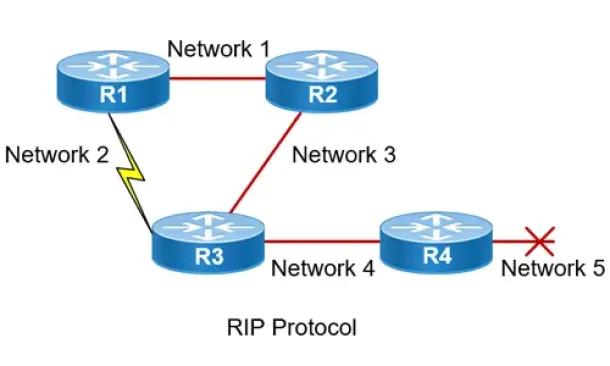
Routing
Routing Information Protocol - RIP
Routing Information Protocol (RIP) is a distance-vector routing protocol that is commonly used in small to medium-sized networks. It is one of the...
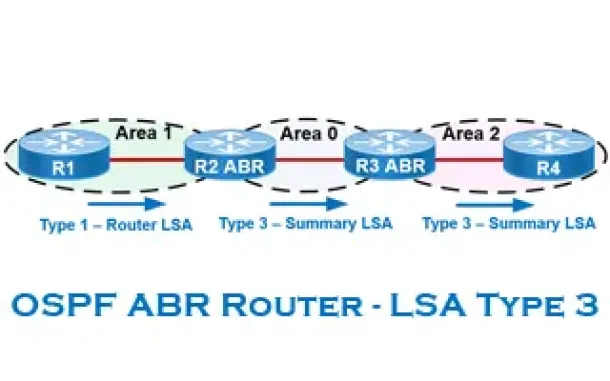
Routing
OSPF - Part 6: OSPF LSA Types - Purpose and Function...
Our previous article explained the purpose of Link State Update (LSU) packets and examined the Link State Advertisement (LSA) information contained with...
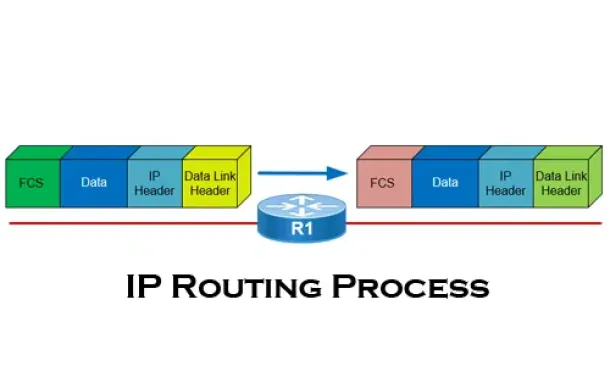
Routing
The IP Routing Process - Step-by-Step Analysis
We are going to analyse what happens when routing occurs on a network (IP routing process). When I was new to the networking area, I thought that all yo...
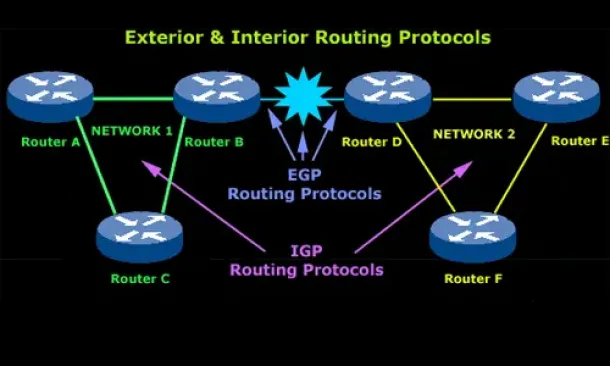
Routing
Introduction to Routing Protocols
Distance Vector, Link State RIP, IGRP, EIGRP, OSPF
Routing protocols were created for routers. These protocols have been designed to allow the exchan...
Network Address Translation - NAT
Network Address Translation (NAT) Concepts
Before we dive into the deep waters of NAT, we need to make sure we understand exactly what NAT does. So let me give you the background of NAT, why it's...
Network Address Translation - NAT
Network Address Translation (NAT) Overload - Part 2
In our previous article, Network Address Translation (NAT) Overload - Part 1, we explained what NAT Overload is and how it works. This page deals with t...
Network Address Translation - NAT
The Network Address Translation Table
After that simple and informative introduction to the NAT concept, it's time to find out more about how it works and this is where the NAT table comes i...
Network Address Translation - NAT
Network Address Translation (NAT) Overload - Part 1
NAT Overload is the most common NAT method used throughout all networks that connect to the Internet. This is because of the way it functions and the li...


















