Articles
To read the articles in this section, simply click on the article title or read button on the far right (if visible).
Use the below filters to customise the number of articles displayed or search for specific title topics/keywords.
| Articles | |
|---|---|
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
Suggested Articles:
Network Protocol Analyzers
How to Detect P2P (peer-to-peer) File Sharing, ...
Peer-to-Peer file sharing traffic has become a very large problem for many organizations as users engage in illegal (most times) file sharing proce...
Network Protocol Analyzers
How to Use Multi-Segment Analysis to Troublesho...
Troubleshooting network problems can be a very intensive and challenging process. Intermittent network problems are even more difficult to troubles...
Network Protocol Analyzers
How To Detect ARP Attacks & ARP Flooding With C...
ARP attacks and ARP flooding are common problems small and large networks are faced with. ARP attacks target specific hosts by using their MAC addr...
Network Protocol Analyzers
How to Perform TCP SYN Flood DoS Attack & Detec...
This article will help you understand TCP SYN Flood Attacks, show how to perform a SYN Flood Attack (DoS attack) using Kali Linux & hping3 and ...
Featured Subcategories:
WireShark Articles:
How to Detect Routing Loops and Physical Loops ...
When working with medium to large scale networks, IT departments are often faced dealing with network loops and broadcast storms that are caused by...
How to Perform TCP SYN Flood DoS Attack & Detec...
This article will help you understand TCP SYN Flood Attacks, show how to perform a SYN Flood Attack (DoS attack) using Kali Linux & hping3 and ...
How to Detect SYN Flood Attacks with Capsa Netw...
This article explains how to detect a SYN Flood Attack using an advanced protocol analyser like Colasoft Capsa. We’ll show you how to identify and ...
Introducing Colasoft Unified Performance Manage...
Colasoft Unified Performance Management (UPM) is a business-oriented network performance management system, which analyzes network performance, qua...
Your IP address:
18.227.89.169
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!
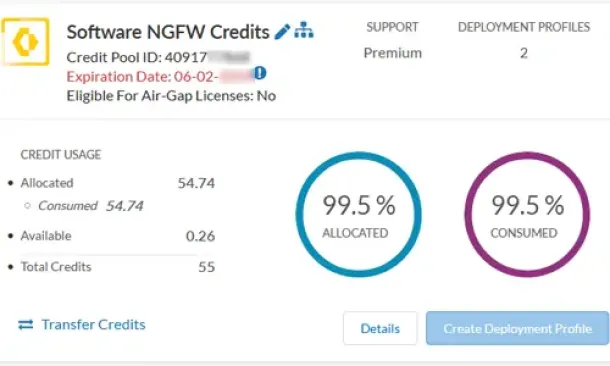
Palo Alto Networks
The Ultimate Guide to Palo Alto Networks Software NG...
Discover the ins and outs of using Palo Alto Networks’ Software NGFW (Flex) credits to seamlessly renew your cloud-based or virtualized software NGFW de...
Palo Alto Networks
Palo Alto Firewall Application-based Policy Enforcem...
Our previous article examined the benefits of Palo Alto Networks Firewall Single Pass Parallel Processing (SP3) architecture and how its combine with th...
Palo Alto Networks
The Benefits of Palo Alto Networks Firewall Single P...
What makes Palo Alto Networks Next-Generation Firewall (NGFW) so different from its competitors is its Platform, Process and Architecture. Palo Alto Net...
Palo Alto Networks
Introduction to Palo Alto Next-Generation Network Fi...
During the past decade, we’ve seen the global IT security market flooded with new network security and firewall security appliances. New vendors emergin...
Windows Servers
How to Install/Enable Telnet Client for Windows Serv...
IT professionals frequently need connectivity and management tools. The Telnet Client is one of the most basic tools for such activities. Using this too...
Windows Servers
Understanding, Creating, Configuring & Applying Wind...
This article explains what Group Policies are and shows how to configure Windows Server 2012 Active Directory Group Policies. Our next article will cove...
Windows Servers
Windows 2003 DHCP Server Installation & Configuration
DHCP (Dynamic Host Configuration Protocol) is a protocol that allows clients on a network to request network configuration settings from a server runnin...
Windows Servers
Windows 2003 DHCP Server Advanced Configuration - Pa...
In this article, we will cover more advanced DHCP features and topics such as server options, superscopes, multicast scopes, dynamic DNS, DHCP database ...
Popular Topics
Windows Servers
Installing Active Directory Services & Domain Contro...
This article serves as an Active Directory tutorial covering installation and setup of Windows 2012 Active Directory Services Role & Domain Controll...
Virtualization & VM Backup
Differences Between VMware vSphere, vCenter, ESXi Fr...
In this article we will cover the differences between VMware ESXi, vSphere and vCenter while also explain the features supported by each vSphere edition...
Windows Servers
Windows Server 2016 Licensing Made Easy – Understand...
This article describes the new Windows Server 2016 Licensing model (per-core licensing) Microsoft has implemented for its new server-based operating sys...
Network Protocol Analyzers
Improve Network Analysis Efficiency with Colasoft's ...
Troubleshooting network problems can be a very difficult and challenging task. While most IT engineers use a network analyzer to help solve network prob...
Cisco CallManager-CCME
IP Phone 7945, 7965, 7975 Factory Reset Procedure, S...
This article explains how to reset your Cisco 7945, 7965 and 7975 IP phone to factory defaults, and how to upgrade the firmware to the latest available ...
Cisco Switches
Cisco 4507R+E Layer 3 Installation: Redundant WS-X45...
It's no news that we here at Firewall.cx enjoy writing about our installations of Cisco equipment and especially devices that we don’t get to see and pl...
Cisco CallManager-CCME
Configuring CallManager Express (CME) To Support Cis...
Cisco is continuously developing its CallManager Express product, introducing new features and services to help keep up with its customers' and the mark...
Cisco Firewalls
Cisco ASA5500 (5505, 5510, 5520, etc) Series Firewal...
The Cisco ASA 5500 series security appliances have been around for quite some time and are amongst the most popular hardware firewalls available in the ...


















