Installing Active Directory Services & Domain Controller via Windows PowerShell. Active Directory Concepts
This article serves as an Active Directory tutorial covering installation and setup of Windows 2012 Active Directory Services Role & Domain Controller using Windows 2012 PowerShell.
Our previous article covered the installation of Windows Server 2012 Active Directory Services role and Domain Controller installation using the Windows Server Manager (GUI) interface.
FREE Hyper-V & VMware Backup: FREE for Firewall.cx readers for a Limited Time! Download Now!
What Is Active Directory?
Active Directory is a heart of Windows Server operating systems. Active Directory Domain Services (AD DS) is central repository of active directory objects like user accounts, computer accounts, groups, group policies and so on. Similarly, Active Directory authenticates user accounts and computer accounts when they login into the domain. Computers must be joined to the domain in order to authenticate Active Directory users.
Active Directory is a database that is made up of several components which are important for us to understand before attempting to install and configure Active Directory Services on Windows Server 2012. These components are:
- Domain Controller (DC): - Domain Controllers are servers where the Active Directory Domain Services role is installed. The DC stores copies of the Active Directory Database (NTDS.DIT) and SYSVOL (System Volume) folder.
- Data Store: - It is the actual file (NTDS.DIT) that stores the Active Directory information.
- Domain: - Active Directory Domain is a group of computers and user accounts that share common administration within a central Active Directory database.
- Forest: - Forest is a collection of Domains that share common Active Directory database. The first Domain in a Forest is called a Forest Root Domain.
- Tree: - A tree is a collection of domain names that share common root domain.
- Schema: - Schema defines the list of attributes and object types that all objects in the Active Directory database can have.
- Organizational Units (OUs): - OUs are simply container or folders in the Active Directory that stores other active directory objects such as user accounts, computer accounts and so on. OUs are also used to delegate control and apply group policies.
- Sites: - Sites are Active Directory object that represent physical locations. Sites are configured for proper replication of Active Directory database between sites.
- Partition: - Active Directory database file is made up of multiple partitions which are also called naming contexts. The Active Directory database consists of partitions such as application, schema, configuration, domain and global catalog.
Checking Active Directory Domain Services Role Availability
Another method of installing an Active Directory Services Role & Domain Controller is with the use of Windows PowerShell. PowerShell is a powerful scripting tool and an alternative to the Windows GUI wizard we covered in our previous article. Open PowerShell as an Administrator and type the following cmdlet to check for the Active Directory Domain Services Role availability:
The system should return the Install State as Available, indicating the role is available for immediate installation. We can now safely proceed to the next step.
Install Active Directory Services Role & Domain Controller Using Windows PowerShell
To initiate the installation of Active Directory Services Role on Windows Server 2012 R2, issue the following cmdlet:
The system will immediately begin the installation of the Active Directory Domain Services role and provide an update of the installation's progress:
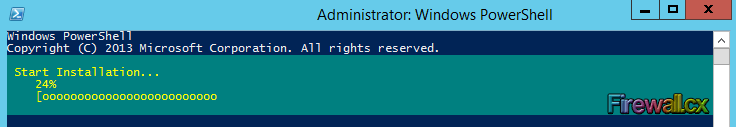
Figure 1. Installing Active Directory Domain Services with PowerShell
Once the installation is complete, the prompt is updated with a success message (Exit Code) as shown below:
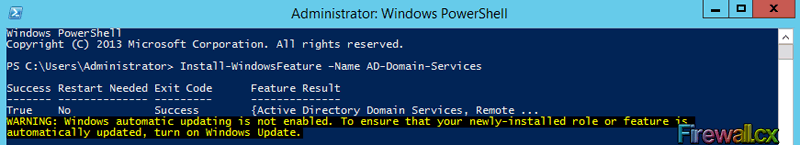
Figure 2. Finished Installing ADDS with PowerShell
PS C:\Users\Administrator> Test-ADDSForestInstallation
The following figure shows the command execution and system output:
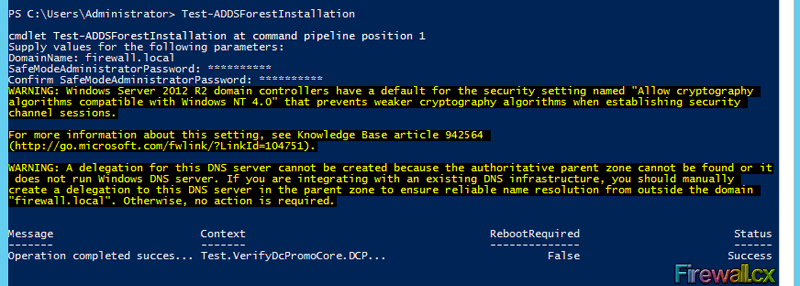
Figure 3. Prerequisite Installation
Now it's time to promote the server to a domain controller. For this step, we need to save all parameters in a PowerShell script (using notepad), which will then be used during the domain controller installation.
FREE Hyper-V & VMware Backup: FREE for Firewall.cx readers for a Limited Time! Download Now!
Below are the options we used - these are identical to what we selected in our GUI Wizard installation covered in our Windows Server 2012 Active Directory Services role and Domain Controller installation using the Windows Server Manager (GUI) article:
# Windows PowerShell script for AD DS Deployment
#
Import-Module ADDSDeployment
Install-ADDSForest
-CreateDnsDelegation:$false
-DatabasePath "C:\Windows\NTDS"
-DomainMode "Win2012R2"
-DomainName "firewall.local"
-DomainNetbiosName "FIREWALL"
-ForestMode "Win2012R2"
-InstallDns:$true
-LogPath "C:\Windows\NTDS"
-NoRebootOnCompletion:$false
-SysvolPath "C:\Windows\SYSVOL"
-Force:$true
Save the script at an easy accessible location e.g Desktop, with the name InstallDC.ps1.
PS C:\Users\Administrator\Desktop> Set-executionpolicy remotesigned
The following figure shows the command execution and system output:
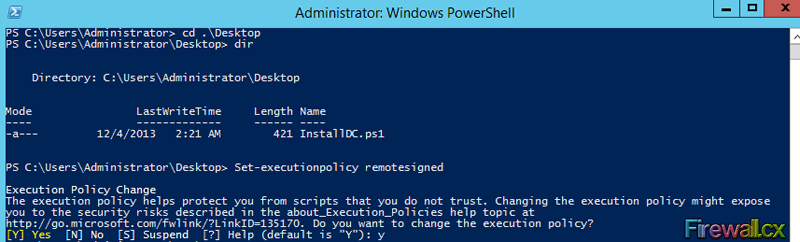
Figure 4. Changing the Execution Policy of PowerShell
Now we can execute our script from within PowerShell by changing the PowerShell directory to the location where the script resides and typing the following cmdlet:
Once executed, the server is promoted to Domain Controller and installation updates are provided at the PowerShell prompt:

Figure 5. Promoting Server to Domain Controller
After the installation is complete, the server will reboot and the server will have Active Directory Domain Services installed with the server being a Domain Controller.
This completes the installation and setup of Windows 2012 Active Directory Services Role & Domain Controller using Windows 2012 PowerShell.
FREE Hyper-V & VMware Backup: FREE for Firewall.cx readers for a Limited Time! Download Now!
Your IP address:
18.224.200.110
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!













