MS Server Articles:
Windows Servers
Free Hyper-V eBook - Create, Manage and Trouble...
With the introduction of Hyper-V on the Windows Server platform, virtualization has quickly become the de facto standard for all companies seeking ...
Windows Servers
Introduction to Windows DNS – The Importance of...
The Domain Name System (DNS) is perhaps one of the most important services for Active Directory. DNS provides name resolution services for Active D...
Windows Servers
Hyper-V Best Practices - Replica, Cluster, Back...
Hyper-V has proven to be a very cost effective solution for server consolidation. Evidence of this is also the fact that companies are beginning to...
Windows Servers
Renaming Windows 2000 Domain Name
Sometimes renaming a domain is an essential business requirement. There are many situations, such as mergers, change of company name or migration f...
Featured Subcategories:
Virtualization & VM Backup Articles:
FREE Webinar - Fast Track your IT Career with V...
Everyone who attends the webinar has a chance of winning a VMware VCP course (VMware Install, Config, Manage) worth $4,500!
Climbing the career la...
How to Enable SNMP on VMware ESXi Host & Config...
In this article we will show you how to enable SNMP on your VMware ESXi host, configure SNMP Community string and configure your ESXi firewall to a...
How to Enable or Disable SSH on VMware ESXi via...
SSH access to VMware’s ESXi server is by disabled by default however there are many reasons where SSH might be required. VMware and System administ...
World Backup Day with Free Amazon Voucher and P...
Celebrate World Backup Day and WIN with Altaro!
We all remember how grateful we were to have backup software when facing so many data loss mishap...
Your IP address:
3.149.248.173
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!
Linux - Unix
Linux CentOS - Redhat EL Installation on HP Smart Ar...
This article was written thanks to our recent encounter of a HP DL120 G7 rack mount server equipped with a HP Smart Array B110i SATA Raid controller, ne...
Linux - Unix
Linux BIND DNS - Part 5: Configure Secondary (Slave)...
Setting up a Secondary (or Slave) DNS sever is much easier than you might think. All the hard work is done when you setup the Master DNS server by creat...
Linux - Unix
Installation and Configuration of Linux DHCP Server
For a cable modem or a DSL connection, the service provider dynamically assigns the IP address to your PC. When you install a DSL or a home cable router...
Linux - Unix
Advanced Linux Commands
Now that you're done learning some of the Basic Linux commands and how to use them to install Linux Software, it's time we showed you some of the other ...
Popular Topics
Cisco Routers
Configuring Cisco Site to Site IPSec VPN with Dynami...
This article serves as an extension to our popular Cisco VPN topics covered here on Firewall.cx. While we’ve covered Site to Site IPSec VPN Tunnel Betwe...
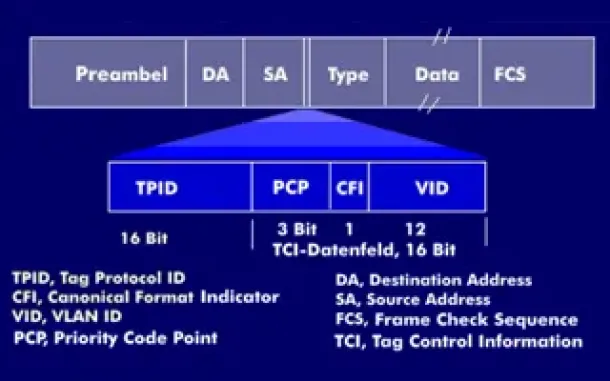
VLAN Networks
VLAN Tagging - Understanding VLANs Ethernet Frames
We mentioned that Trunk Links are designed to pass frames (packets) from all VLANs, allowing us to connect multiple switches together and independently ...
Cisco Routers
Configuring PPTP (VPDN) Server On A Cisco Router
The Point to Point Tunneling Protocol (PPTP) is a network protocol used to create VPN tunnels between public networks. These VPN tunnels are encrypted f...
OpManager - Network Monitoring & Management
Network Management Systems Help Businesses Accuratel...
Accurately monitoring your organization’s business application performance, service provider SLA breaches, network infrastructure traffic, bandwidth ava...

















