Configuring PPTP (VPDN) Server On A Cisco Router
The Point to Point Tunneling Protocol (PPTP) is a network protocol used to create VPN tunnels between public networks. These VPN tunnels are encrypted from one end to the other and allow the secure transfer of data between them. PPTP is usually implemented between a server and a client, the server belonging to the enterprise network and the client being a remote workstation.
While PPTP's encryption algorithms do offer a certain level of security and privacy, they aren't the best encryption technologies available today. PPTP does have its weaknesses and therefore is not used for long term transactions. PPTP uses the Password Authentication Protocol and the Challenge Handshake Authentication Protocol encryption algorithms. It can offer encryption options of 40, 56 and 128 bit, depending on your needs.
PPTP is an excellent quick VPN solution for short-term transactions and is natively supported by all current Windows platforms without the need for additional drivers or programs.
Cisco routers can be set up to act as PPTP servers, alternatively known as a Virtual Private Dialup Network (VPDN) servers. PPTP has been supported by Cisco routers since IOS release 12.1(5)T.
We should point out that Windows Servers are also capable of handing PPTP connections by configuring their RAS services, however, we feel that being able to provide this service from a Cisco router makes it more flexible and easier to implement in any environment.
Note: You can read our article on Windows VPDN setup to get all the information on how to set up a remote teleworker to connect to the VPDN configured on your Cisco router.
Example Scenario
In this example, we need to set up our Cisco router so that it accepts VPDN requests, allow our remote clients to connect to the internal network, assign them an internal IP address and provide them access to all network resources:
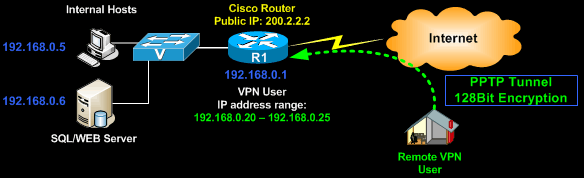
The remote VPN user will have to create a VPDN dialup from its operating system (we assume Windows XP) in order to initiate the VPN connection and authenticate to the Cisco router.
First step is to enable VPDN and create the VPDN group parameters that will define various aspects of the PPTP connection:
R1# configure terminal
R1(config)# vpdn enable
R1(config)# vpdn-group 1
R1(config-vpdn)# accept-dialin
R1(config-vpdn-acc-in)# protocol pptp
R1(config-vpdn-acc-in)# virtual-template 1
R1(config-vpdn-acc-in)# exit
The above configuration enables the router to accept incoming PPTP connections and specifies the virtual interface to which the PPTP tunnel is configured.
Next up, we need to bind the virtual interface to a real interface. This effectively binds the PPTP connections to the real interface. We'll also need to create a pool of IP addresses that will be assigned to the VPDN users. This pool is named 'PPTP-Pool' and we'll later on assign the addresses to be allocated to the VPN users.
R1(config)# interface Virtual-Template1
R1(config-if)# ip unnumbered FastEthernet 0/0
R1(config-if)# peer default ip address pool PPTP-Pool
R1(config-if)# no keepalive
R1(config-if)# ppp encrypt mppe 128
R1(config-if)# ppp authentication ms-chap ms-chap-v2
The 'ppp encrypt' command specifies the encryption to be used - in our case, that's 128 bit. This can be set to 'auto' for maximum compatibility. The authentication is set to ms-chap and ms-chap v2 so that we can offer the best possible authentication method for this case.
The 'ip unnumbered <interface>' command is worth analysing a bit further.
All VPDN clients will either obtain an IP address that is part of the existing internal network (as in our example), or they will be assigned an IP address that is totally different from the internal network scheme e.g 192.168.5.20 - 192.168.5.25.
If you want to assign them an IP address that's part of the existing internal network (most cases), you need to use the 'ip unnumbered' command to bind the virtual adapter to the real interface connected to the internal network - in our example, this is FastEthernet 0/0.
If on the other hand you wish to provide VPDN clients with a totally different IP address from that of your internal network, then you must configure the Virtual-Template interface with an IP address belonging to that network e.g 192.168.5.1 and configure the VPDN pool with the appropriate range e.g 192.168.5.20 - 192.168.5.25.
Older Cisco router models such as the 836 & 837 series had problems assigning the VPDN clients an IP address that belonged to the existing internal network, so engineers didn't have much choice but to assign a different IP addressing scheme for the VPDN clients.
From the configuration and diagram provided so far, you can see that we'll be assigning the VPDN clients an IP address range that's part of the existing internal network:
R1(config)# ip local pool PPTP-Pool 192.168.0.20 192.168.0.25
Last step is to create the user accounts our VPDN clients will require to authenticate to the router and access internal resources.
This is a fairly simple task as you only need to add a username, followed by the password:
R1(config)# username firewall password gfk$251!
The remote user will need the above username and password to successfully connect to the VPN.
You can read our article on Windows VPDN setup to get all the information on how to set up a remote teleworker to connect to the VPN.
Summary
This article covered the configuration of a PPTP or VPDN server on a Cisco router. We saw all aspects of its configuration, plus alternative configurations that will help you adjust the set up to your needs.
If you have found the article useful, we would really appreciate you sharing it with others by using the provided services on the top left corner of this article. Sharing our articles takes only a minute of your time and helps Firewall.cx reach more people through such services.
Your IP address:
3.145.26.180
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!













