Discover the Ultimate Firewall Management Tool: 7 Essential Features for Unleashing Unrivaled Network Security!
 Firewall security management is a combination of monitoring, configuring, and managing your firewall to make sure it runs at its best to effectively ward off network security threats. In this article, we will explore the seven must-have features of a firewall security management tool and introduce Firewall Analyzer, a popular Firewall Management Tool that has set the golden standard in Firewall Management across all vendors of firewall and security products. Furthermore, we'll explain how central firewall policy management, VPN management, log analysis, log retention, compliance management and threat identification/forensics, help create a robust cybersecurity and network security posture that increases your organization's ability to protect its networks, information, and systems from threats.
Firewall security management is a combination of monitoring, configuring, and managing your firewall to make sure it runs at its best to effectively ward off network security threats. In this article, we will explore the seven must-have features of a firewall security management tool and introduce Firewall Analyzer, a popular Firewall Management Tool that has set the golden standard in Firewall Management across all vendors of firewall and security products. Furthermore, we'll explain how central firewall policy management, VPN management, log analysis, log retention, compliance management and threat identification/forensics, help create a robust cybersecurity and network security posture that increases your organization's ability to protect its networks, information, and systems from threats.
The seven must-have features of a firewall security management tool are:
- Firewall Policy Management
- VPN Management
- Firewall Change Management
- Compliance Management
- Log Analysis & Threat Identification
- Log Retention & Forensics
- Network Security Alerts
Let’s take a look at each of these features and provide examples that showcase their importance.
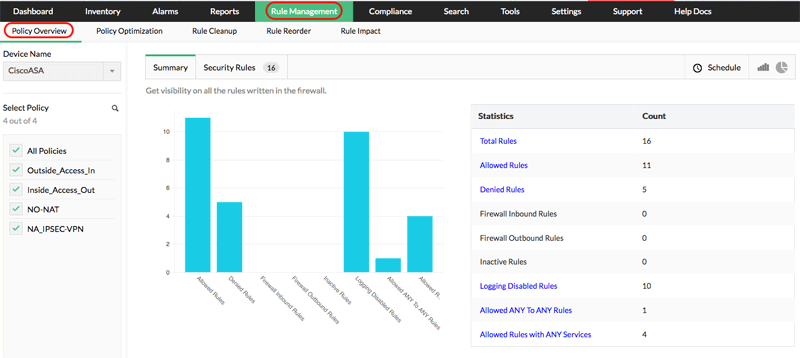
Firewall Policy Management
 This is the process of managing and organizing your firewall rules. These firewall rules and policies dictate the traffic that is entering and exiting your network, and can also be used to block illegitimate traffic.
This is the process of managing and organizing your firewall rules. These firewall rules and policies dictate the traffic that is entering and exiting your network, and can also be used to block illegitimate traffic.
Why is this important? Effective firewall policy management can be used to ensure firewall policies never become outdated, redundant, or misconfigured, leaving the network open to attacks.
One of the primary challenges in firewall policy management is the potential for human error. Configuring firewall rules and policies requires a deep understanding of network architecture, application requirements, and security best practices. Unfortunately, even experienced IT professionals can make mistakes due to various factors, such as time constraints, lack of communication, or a misunderstanding of the network's specific needs.
Different individuals within an organization may also have different levels of expertise and understanding when it comes to firewall policies. This diversity in knowledge and experience can lead to inconsistencies, redundant rules, or conflicting configurations, compromising the firewall's overall effectiveness.
Taking proactive steps to manage firewall policies effectively can significantly enhance an organization's security posture and protect valuable assets from potential breaches and cyberattacks. This is where solutions such as Firewall Analyzer can undertake the burden of managing firewall policies through an intuitive, simplified and easy-to-follow interface no matter the vendor of firewall you’re dealing with.
Few of the key-features offered by Firewall Analyzer include:
- Gain enhanced visibility on all the rules in your firewall and a comprehensive understanding of your security posture.
- Quickly identify and record anomalies in redundant, generalized, correlated, shadowed, or grouped rules.
- Analyze firewall policies and get suggestions on changes to rule order to optimize performance.
- Simplify the rule creation, modification, and deletion process.
- Check the impact of a new rule on the existing rule set.
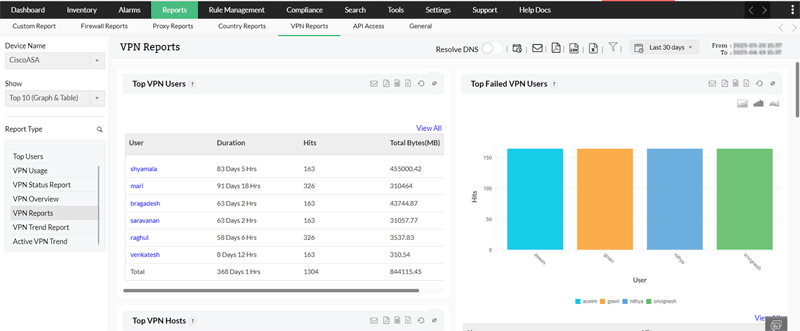
VPN Management
 Virtual private networks (VPNs) enable remote access to a company's resources, allowing employees to work from any location across the globe. Popular solutions include Cisco’s AnyConnect VPN client, Palo Alto Global Protect amongst others.
Virtual private networks (VPNs) enable remote access to a company's resources, allowing employees to work from any location across the globe. Popular solutions include Cisco’s AnyConnect VPN client, Palo Alto Global Protect amongst others.
Why is this important? A well-planned VPN strategy can make or break your organizations work-from-home infrastructure and is critical for employee productivity and security. A lapse in VPN management can be abused by attackers to break into the network.
A VPN Management solution can aid in capturing and analyzing cyberattacks aimed at the VPN infrastructure. By monitoring network traffic logs, user behavior, Multi-Factor Authentication (MFA) attacks and suspicious user logins from multiple locations, you can diminish the chances of unauthorized access and potential data breaches.
The combination of a VPN Management and Firewall Security Policy Management solution, grants organizations greater control over access rights and permissions. It provides administrators and security teams with the ability to manage user privileges based on their roles and responsibilities – reducing the attack surface while at the same time limiting the exposure of critical assets and sensitive information to selected authorized users or groups.
Features to look for in a VPN Management solution should include:
- Identify network attacks and malicious attempts made on your VPN users.
- Understand VPN usage trends and plan for capacity.
- See when there have been multiple login attempts, view the top VPN consumers, and more.
- Identify MFA bombing attacks.
-
Correlate logs between firewalls and VPN gateways to identify attacks and unauthorized login or access attempts.
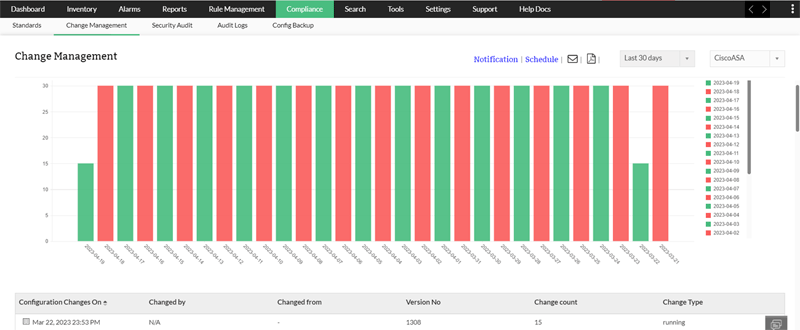
Firewall Change Management
This is the process of controlling the changes made to firewall configurations. This includes managing changes made to firewall rules, policies, and configurations.
Why is this important? Change management should be adequately monitored to prevent unauthorized tampering. Changes are often left unmonitored, which can deal a huge blow to network security when unwanted changes aren't detected in time.
With Firewall Analyzer, you can:
- Gain visibility on the changes made to your firewall configurations.
- View detailed reports on who, when, what, and where changes were made.
-
Enforce advanced user access control to restrict unauthorized users from making changes to the firewall.
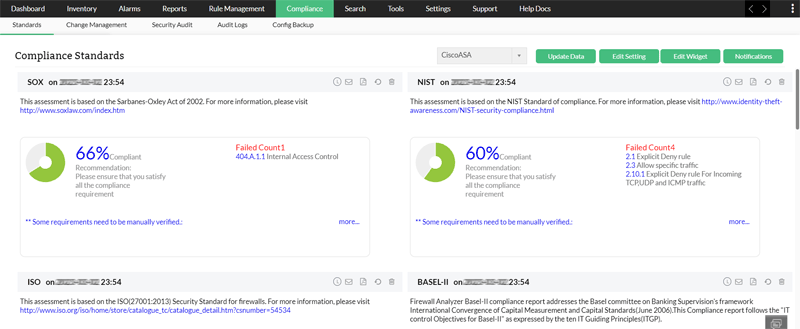
Compliance Management
This is the process of ensuring that an organization's network security policies and procedures align with regulatory requirements and industry standards.
Compliance management is extremely important in a firewall security product as it ensures the firewall’s configuration and policies align with industry standards and regulatory requirements.
Regulatory compliance is mandatory in many industries, for example, healthcare, government, finance are just to name a few, all which are subject to strict regulations and compliance standards.
Why is this important? This is crucial for organizations to avoid fines, penalties, or legal issues that will arise from non-compliance to security mandates. Staying compliant ensures the organization's security posture is strong enough to tackle cyberattacks and security breaches.
How does Firewall Analyzer help?
- Firewall Analyzer offers out-of-the-box compliance reports for leading compliance mandates such as the PCI DSS, ISO 27001, NIST, SANS, NERC-CIP, etc.
-
Firewall security audit reports easily audit firewalls on a regular basis and offer suggestions to address vulnerabilities.
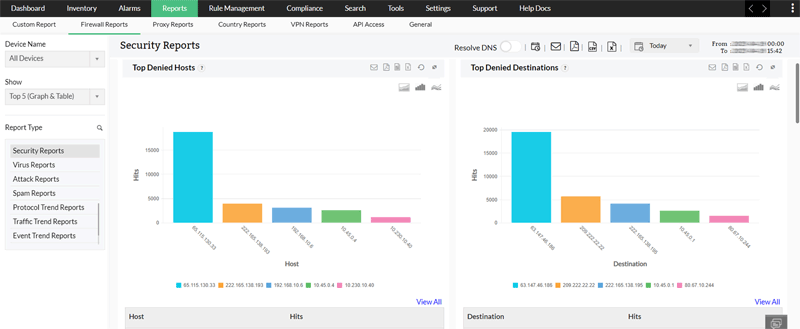
Log Analysis & Threat Identification
Log analysis and threat identification are essential features in any firewall security product as they provide critical insights into network traffic, activities and potential security threats. By analyzing firewall logs, security teams can gain visibility into network traffic, user behavior and attempted intrusions.
This information help identify unusual patterns, suspicious activities, or even potential security breaches allowing for a timely mitigation of threats. The threat identification capability enables organizations to respond to emerging threats, bolstering the network’s security posture and safeguarding sensitive data and assets from cyberattacks.
With Firewall Analyzer, you can:
- Analyzes huge volumes of logs generated and view insightful information in the form of reports.
- These reports include information on top denied hosts, denied protocols, and top security events generated.
- Investigate security events in real time.
- Help proactively take measures to prevent security breaches.
Log Retention & Forensics
This is the practice of storing and archiving network activity logs for a specified period. Various compliance mandates require the logs to be stored for different amounts of time.
Log retention and forensics play a pivotal role in modern cybersecurity and incident response strategies. The importance of log retention lies in its ability to provide a detailed record of activities occurring within an information system, network, or application. By capturing and retaining logs, organizations can gain valuable insights into user actions, system events, and security incidents.
The implications of inadequate log retention can be severe. Without comprehensive log data, organizations risk missing critical indicators of compromise, which can lead to prolonged security breaches or a delayed response to cyberattacks. Moreover, inadequate log retention may hinder incident investigation and forensic analysis, leaving organizations ill-equipped to understand the nature of an attack or fulfill legal and compliance requirements.
Why is this important? To comply with regulations like HIPAA, the PCI DSS, the GDPR, etc., organizations are required to retain specific types of logs for a defined period. Retaining logs is also useful in investigating security incidents, identifying malicious activity patterns, and performing forensic analysis.
Solutions such as Firewall Analyzer enable organizations to:
- Retain logs in the database and set a time period for log retention.
- Use advanced search reports for log forensics, allowing you to search for a specific historical security event and identify the log responsible for said event.
-
Assist with the compliance of HIPAA, PCI DSS, GDPR regulations.
Network Security Alerts
These denote the notifications generated that indicate a potential security threat or anomaly detected in the network.
Why is this important? Considering the large number of network events generated on a daily basis, it is easy for critical alerts to get buried under a pile of low priority alert messages. Failing to take action on crucial network security alerts can jeopardize the integrity of an organizations entire network security infrastructure, paving the way for hackers to infiltrate the system.
With Firewall Analyzer, you can:
- Leverage real-time monitoring capabilities to help identify and prevent network threats.
- Set bandwidth- and security-based triggers and get notified via email or SMS when thresholds are violated.
-
Proactively monitor your network security posture and stop security breaches for they happen.
Summary
Effective management of firewalls, VPNs, compliance, log analysis, log retention, and threat identification/forensics is of paramount importance in ensuring robust cybersecurity. Firewall change and policy management enable organizations to control network traffic, safeguard critical assets, and prevent unauthorized access. Proper VPN management ensures secure remote connectivity and protects data during transmission. Compliance management ensures adherence to industry regulations and standards, safeguarding sensitive data and avoiding legal repercussions.
Log analysis and retention provide valuable insights into network activities, aiding in real-time threat detection and post-incident investigations. Threat identification and forensics empower organizations to promptly respond to cyberattacks, mitigate damages, and enhance overall security. Together, these practices form the cornerstone of a comprehensive cybersecurity strategy, strengthening an organization's resilience against evolving threats and safeguarding data integrity.
A robust firewall security management tool such as Firewall Analyzer covers all above features while at the same time reduces manual intervention, automates reports, helps mitigate security risks, and keeps you notified about any anomalies. Download a free trial or sign up for a personalized demo today to learn more about the tool's capabilities.
Your IP address:
3.135.190.188
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!