7 Essential Firewall Management Strategies for Maximum Security

A firewall appliance is a fundamental pillar of network security, acting as the first line of defense against cyber threats. However, its strength is only as good as its configuration, monitoring, and ongoing maintenance. A poorly managed firewall is like a high-security vault with a weak lock—inviting trouble. Simply deploying a firewall isn’t enough; effective management is essential to ensure it remains a robust safeguard rather than a security blind spot.
Proper firewall administration involves real-time traffic monitoring, rule-set optimization, and timely updates to block evolving threats while allowing legitimate access. Without these crucial practices, even the most advanced firewall can become a liability, leaving your network exposed to exploitation.
To fortify your cybersecurity posture, here are seven essential best practices for effective firewall management.
Key Topics:
- Routing Testing and Patch Management
- Firewall Policy Optimization
- Monitor Firewall Performance
- Log Monitoring and Alerts
- Backup Firewall Rule Sets & Configuration
- Policy Decision-Making
- Periodical Reviewing of Firewall Access Controls
- Summary
Download your copy of the industry's leading Firewall Management Platform.
Routine Testing and Patch Management
Routine Testing: Your firewall needs regular testing to ensure it is working effectively. The testing includes vulnerability scanning, penetration testing, and compliance audits to identify weaknesses, simulate attacks, and ensure alignment with security standards.
Patch Management:Firewalls may develop vulnerabilities as time passes. Patch management is the process of installing updates and patches to fix these security weaknesses. It is essential to consistently update the software and firmware of your firewall to defend against new threats and maintain peak performance.
Example: Applying the most recent vendor patch when routine testing reveals a new vulnerability in your firewall software can help reduce this risk and improve the security of your network.
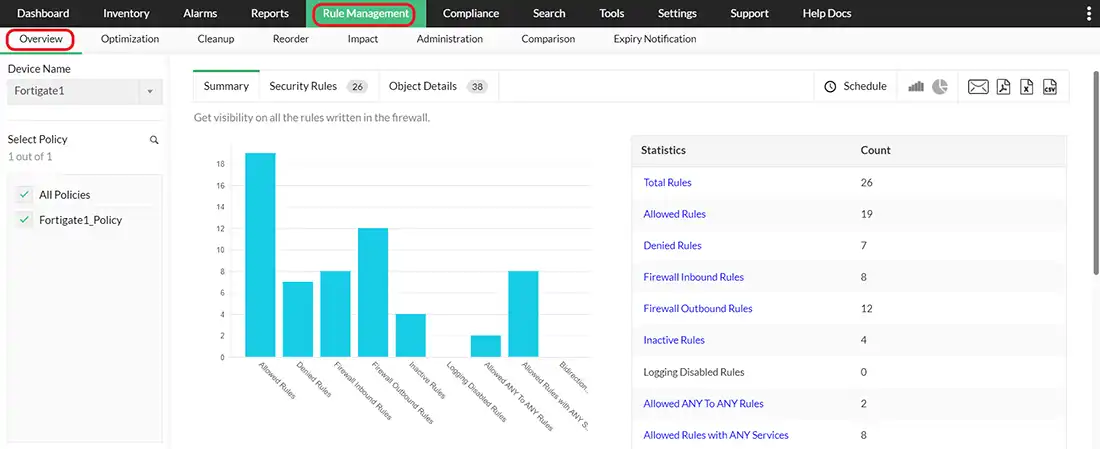
Firewall Policy Optimization
Identifying Emerging Risks: Firewall policies must keep up with emerging cyber threats. These measures guarantee that your firewall is able to efficiently prevent or reduce the impact of emerging and evolving attack methods.
Security Requirements changes: When you add a new host or an application, or when your network undergoes any kind of change, you need to update your firewall policies to ensure maximum protection.

Revise and Review Policies: Make sure to revise and review your firewall policies periodically to ensure your company's security goals are met.
Example: If a new cloud-based collaboration tool is being implemented by your organization, you will need to adjust your firewall rules to permit traffic through the specific ports required for communication with its servers. It is important to make sure that these modifications do not accidentally expose your network to other security risks. For example, you may need to restrict the IP addresses or domains that are allowed to connect to these ports in order to reduce the chances of unauthorized access.
Monitor Firewall Performance
Monitor performance: Monitor your firewall's performance on a regular basis to identify issues like high CPU or memory usage. This will help prevent interruptions and maintain smooth functioning.
Anomaly Detection: Analyzing performance data trends and anomalies through a monitoring solution enables the detection of unusual activities or traffic changes that could signal a security threat or performance problem. By examining patterns over time, you can receive alerts for potential issues.
Example: High CPU usage could indicate that your firewall is having difficulty handling the amount of traffic, which could result in performance issues or downtime. A sudden increase in traffic may indicate a potential attack or misconfiguration.
Monitor, Patch, and Backup your Firewall with Firewall Analyzer - The industry's leading Firewall Management Platform. Download Now!
Log Monitoring and Alerts
Log Monitoring: Monitor firewall logs consistently to analyze traffic trends and detect any abnormal behavior. These logs offer important information about network activity and possible security breaches.
Manage Alerts: Set alerts for any unusual activities or irregularities to promptly detect and address possible threats.
Threat Intelligence: Use log data for developing internal threat intelligence capabilities, which can help in predicting future attacks by recognizing repetitive patterns.
Example: Unusual traffic patterns in logs could suggest a possible attack, leading to the need for prompt investigation and action.
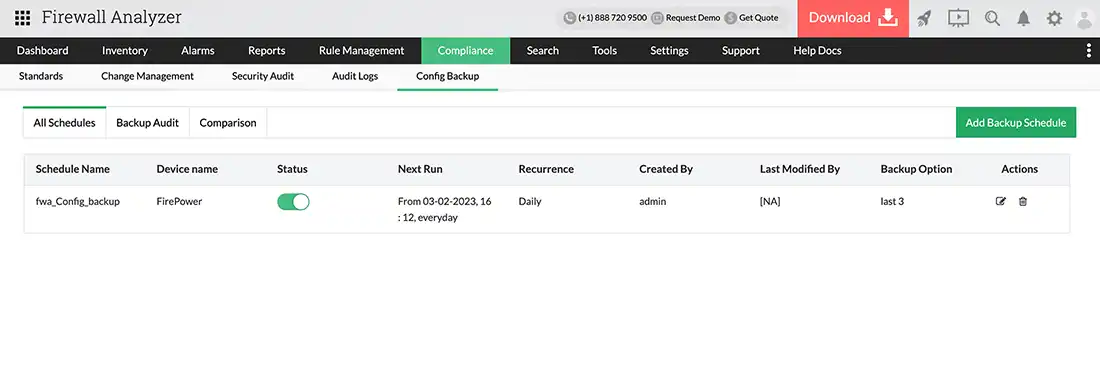
BackUp Firewall Rule Sets & Configuration
Backup Rule Sets: Periodically back up your firewall rule sets without fail to make sure the configurations are ready for restoration in case of failure or misconfiguration. The frequency of backups should be based on the complexity of your network and your tolerance for risk.
Store Backups Securely: Ensure backups are securely stored to prevent unauthorized access or corruption, protecting configuration integrity in case of a security breach or system failure.
Test your Rules: Ensure your firewall rules are periodically tested to confirm the rules are working and no unintended access is allowed.
Example: Enabling a backup allows for the quick restoration of the previous configuration in case a rule is unintentionally deleted. But utilizing insecurely stored backups for restoration may result in the introduction of vulnerabilities.
Policy Decision-Making
Decision Logging: Detailed logs should be maintained for all firewall policy changes, documenting the individuals responsible for the changes and the reasoning behind them. This allows for monitoring changes over time and comprehending their effects.
Example: If a security issue arises due to a policy change, examining logs can help determine the reason for the change and facilitate a quick resolution.
Periodical Reviewing of Firewall Access Controls
Review Access Controls: Regularly review and update access controls to ensure that only authorized individuals can access firewall configurations and management tools. This ensures that unauthorized modifications are prevented and policy integrity is preserved.
Example: Revoking access to management tools for employees who leave the organization or change roles helps reduce security risks. Implementing these guidelines establishes a solid base for network security.
To simplify firewall management, you may want to explore more advanced solutions such as ManageEngine Firewall Analyzer. This solution provides in-depth examination of firewall setups, live traffic tracking, and adherence confirmation through functionalities like:
Rule Management: Simplifies the process of creating, modifying, and deleting rules within structured rule sets:
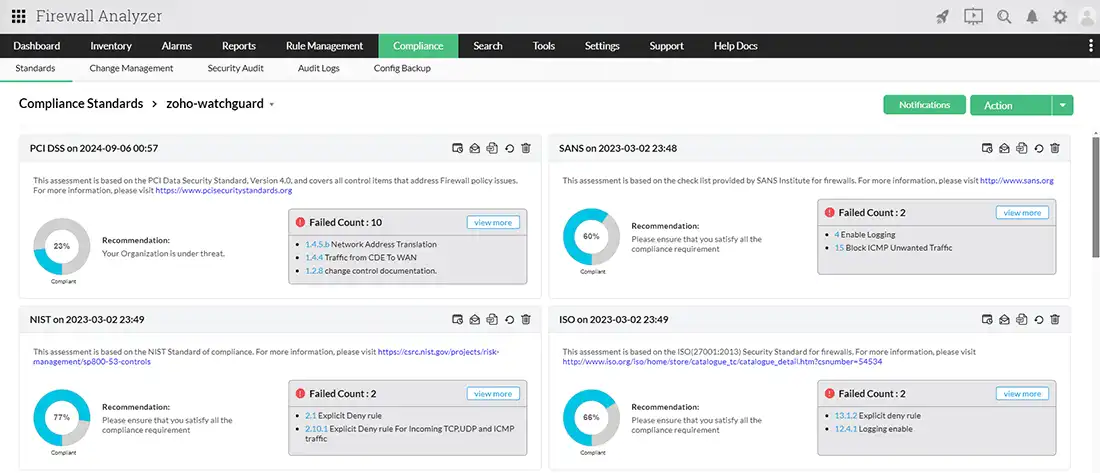
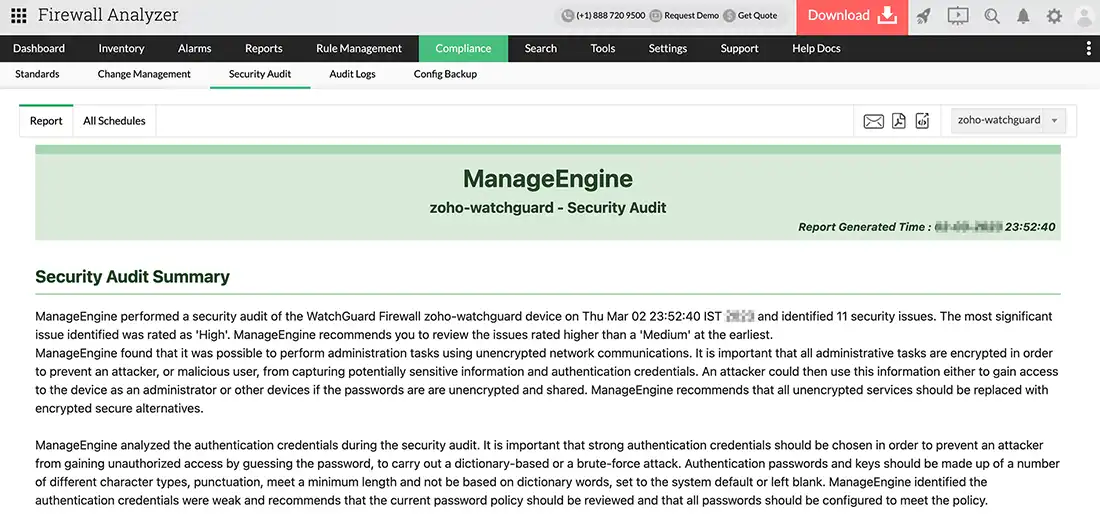
Compliance Audits: Track firewall configurations against common regulatory frameworks, providing audit-ready reports for compliance validation:
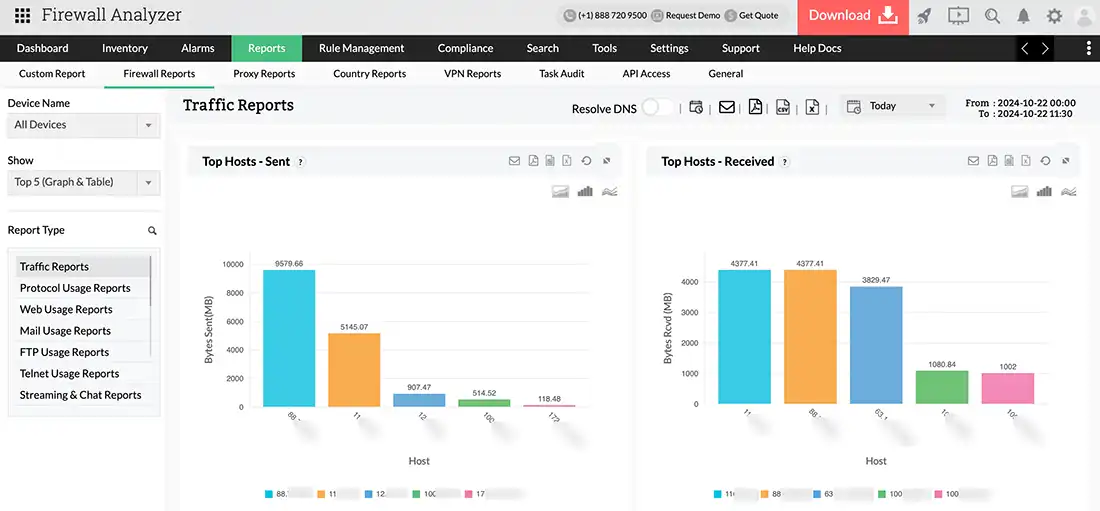
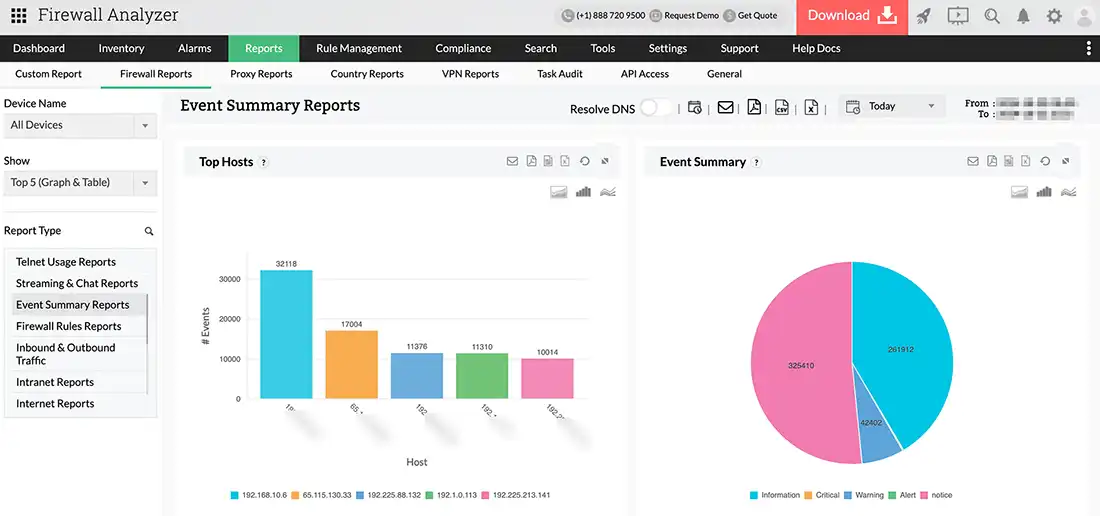
Traffic Monitoring: Analyze firewall traffic in real time to monitor bandwidth usage, spot traffic spikes, and detect anomalies:
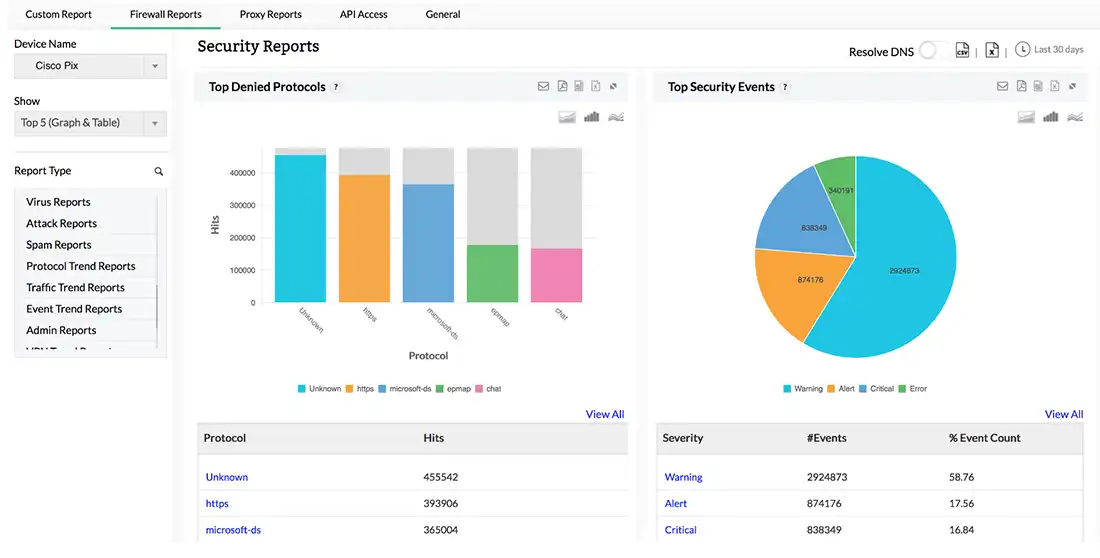
Log Analysis: Gain detailed insights from firewall logs, to detect security threats, traffic patterns and more:
Configuration Backups: Automated firewall configuration backups to enable fast recovery:
Performance Monitoring: Tracks significant metrics like CPU and memory utilization:
Security Audits: Identifies security issues, evaluates their impact and exploitation ease, and offers mitigation commands and best practices:
Reporting and Alerts: Offers instant alerts and detailed reports, providing visibility into firewall activity, security incidents, compliance metrics and more:
By integrating a solution that includes these characteristics, you can greatly improve your firewall management process. Download your copy of Firewall Analyzer today to experience how it can bolster your network security!
Summary
Effective firewall management is not a one-time task but an ongoing process that ensures your network remains resilient against evolving cyber threats. By implementing key practices such as routing testing and patch management, firewall policy optimization, performance monitoring, and proactive log analysis, organizations can strengthen their security posture. Additionally, regular backups of rule sets and configurations, informed policy decision-making, and periodic access control reviews help maintain compliance and minimize vulnerabilities.
To streamline and enhance firewall management, ManageEngine's Firewall Analyzer provides comprehensive visibility, real-time monitoring, and in-depth analytics to optimize security policies, detect anomalies, and ensure regulatory compliance. Leverage Firewall Analyzer to take control of your network security with automated insights, proactive alerts, and efficient firewall administration.
Your IP address:
3.22.42.249
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!