Dealing with Security Audit Challenges: Discovering vulnerabilities, unauthorized access, optimize network security & reporting
 The utilization of log analyzers, such as Firewall Analyzer, in network infrastructure plays a pivotal role in enhancing cybersecurity and fortifying the overall security posture of an organization. Security audits, facilitated by log analyzers, serve as a critical mechanism for systematically reviewing and analyzing recorded events within the network.
The utilization of log analyzers, such as Firewall Analyzer, in network infrastructure plays a pivotal role in enhancing cybersecurity and fortifying the overall security posture of an organization. Security audits, facilitated by log analyzers, serve as a critical mechanism for systematically reviewing and analyzing recorded events within the network.
This proactive approach enables the identification of potential security risks, unauthorized access attempts, and abnormal activities that might signify a breach. The log analyzer sifts through vast amounts of data & logs, providing insights into patterns and anomalies that might go unnoticed otherwise.
By uncovering vulnerabilities and irregularities, organizations can take timely corrective actions, preventing potential security breaches. Moreover, the information gleaned from these audits is instrumental in formulating a comprehensive security strategy that extends across the entire network infrastructure.
This strategic approach ensures a holistic defense against cyber threats, fostering a resilient and adaptive cybersecurity framework that aligns with the evolving landscape of security challenges.
This article will delve into the concept of security audits and how a product like Firewall Analyzer can streamline this crucial procedure.
Key Topics:
- Security Audits Explained
- Security Audit Challenges
- Tool for Effective Network Security Management
- Conducting a Security Audit with Firewall Analyzer
- Summary
Download your copy of ManageEngine's popular Firewall Analyzer here.
Security Audits Explained
A security audit serves as a systematic evaluation of an organization's capacity to thwart threats and safeguard sensitive data. This comprehensive process involves the identification of vulnerabilities, the formulation of recommendations for enhancements, and the reinforcement of the overall security posture.
By delving into an organization's security protocols, infrastructure and system logs, a security audit offers a subtle assessment of its ability to resist various cyber threats. It not only pinpoints existing vulnerabilities but also recommends specific measures to fortify defenses, ensuring a resilient cybersecurity framework.
In the contemporary landscape, where cybercrime is on the rise, organizations face an escalating number of sophisticated attacks that pose significant risks to their data and operations. The financial repercussions of a data breach are substantial, with the average cost reaching $4.45 million in 2023 — a 2.3% increase compared to the previous year.
Against this backdrop, conducting thorough security audits emerges as a critical strategy for organizations to proactively protect themselves from potential attackers. These audits not only help in identifying and addressing vulnerabilities but also contribute to cost-effective risk mitigation, thereby playing a pivotal role in fortifying the network and organizational defenses against the evolving threat landscape.
Security Audit Challenges
Carrying out security audits can be difficult and intricate, varying based on the organization and audit scope. The following are the primary obstacles linked to performing a security audit.
- Defining the target: It is crucial to define a specific scope to ensure that the security audit addresses the relevant areas of your organization's environment. Determining the networks, databases, apps, etc. that require auditing is part of this important process however one of the fundamental issues faced during the definition of the audit target is the need to strike a delicate balance between comprehensiveness and practicality. On one hand, an exhaustive audit that scrutinizes every nook and cranny of an organization's digital infrastructure may be resource-intensive, time-consuming, and, in some cases, impractical. On the other hand, a narrowly defined scope might inadvertently overlook critical vulnerabilities lurking in overlooked corners of the system.
- Adapting to an evolving cyber landscape: Navigating the challenges of security audits within an ever-evolving cyber landscape involves facing a dynamic and shifting terrain. It's akin to safeguarding a futuristic city where the buildings change shape, new streets appear, and the bad guys constantly come up with new tricks. New technologies, software, and gadgets emerge regularly.
Security audits must adapt to include these novel elements, ensuring that the audit doesn't miss potential vulnerabilities in the latest tech. This requires security experts to stay updated on the latest trends and continuously update their audit methods. Tools like Firewall Analyzer have built-in correlation engines, automating this whole process, making it easier for organizations to adapt to the evolving cyber landscape and not fall behind.
- Crafting clear reports: Crafting clear and concise security audit reports poses its own set of challenges, as it involves distilling complex technical information into a format that is understandable for a diverse audience, including non-technical stakeholders.
Here are some key challenges associated with creating such reports:
- Technical Complexity vs. Non-Technical Audience: Security audits often uncover intricate technical details about vulnerabilities, threats, and countermeasures. Communicating these technical aspects in a way that is easily digestible for non-technical stakeholders, such as executives or board members, is a significant challenge. Striking the right balance between providing sufficient detail for IT professionals and offering a high-level overview for executives is crucial.
- Prioritization of Findings: Security audits typically reveal multiple vulnerabilities and issues. Deciding which ones to highlight, based on their severity and potential impact on the organization, can be challenging.
- Actionable Recommendations: While identifying cybersecurity issues is important, providing actionable and practical recommendations for addressing these issues is equally vital.
- Continuous Monitoring Challenges: Cybersecurity is a dynamic field, and threats can evolve rapidly. Communicating the need for continuous monitoring and periodic re-evaluation of security measures can be challenging. Reports should convey that cybersecurity is an ongoing process rather than a one-time fix.
- Compliance Reporting: For organizations subject to regulatory requirements, security audits often need to address specific compliance standards. Balancing the technical aspects of security with the intricacies of compliance reporting requires a comprehensive understanding of both realms.
-
Resource management challenges: Insufficiently trained staff can significantly hinder security audits. Conducting security audits, whether through an in-house cybersecurity team or by outsourcing, can be a significant financial burden.
-
Human-factor challenges: The accuracy of the security audit can be affected by human error. Some of the examples of potential security risks include miscommunication, insider threats, misinterpretation of findings, and failure to adhere to security protocols.
Tool for Effective Network Security Management
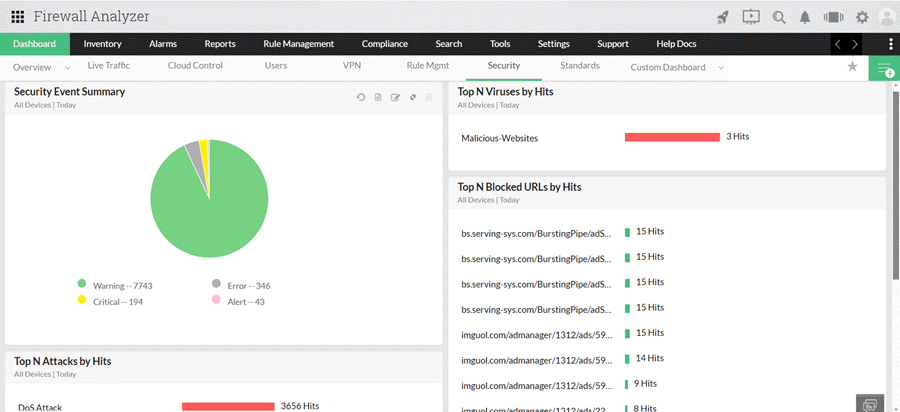
The process of a successful security audit may seem daunting, but utilizing tools such as Firewall Analyzer and its comprehensive range of capabilities can simplify the entire audit procedure and convert it into a concise and practical plan for enhancing your protection against cybersecurity threats.
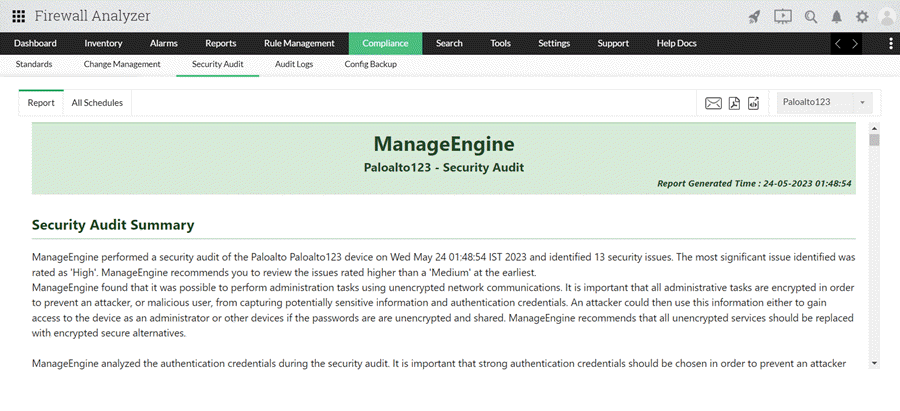
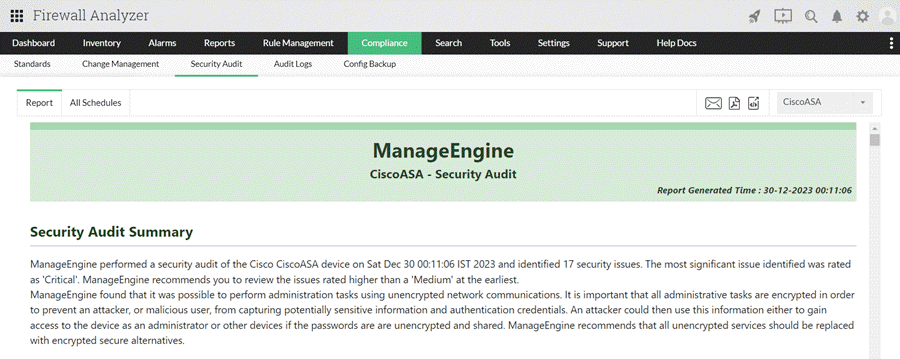
The below screenshot provide an example of a security audit performed on a Cisco ASA firewall:
Conducting a Security Audit with Firewall Analyzer
ManageEngine Firewall Analyzer is a powerful tool that aims to streamline and improve the process of security auditing. It offers a wide range of features to facilitate security audits, such as:
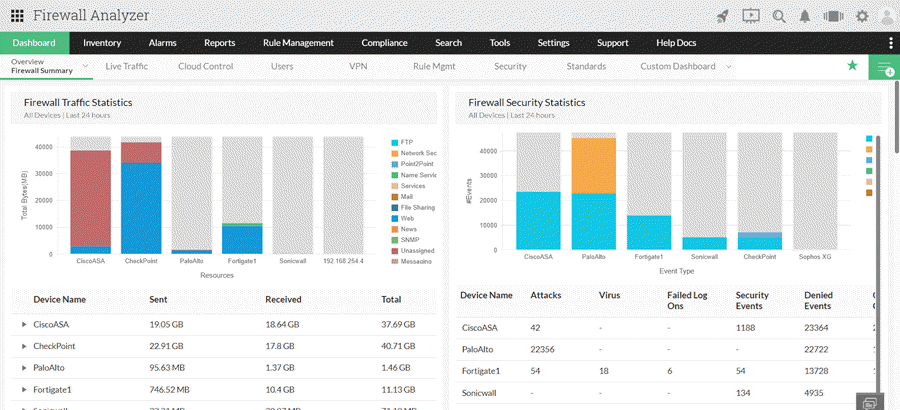
- Log analysis: ManageEngine Firewall Analyzer provides comprehensive log analysis for firewalls, routers, IDSs, and IPSs. It offers valuable insights into network traffic patterns, user behavior, and security incidents. The analysis of these logs is crucial for promptly identifying potential security risks or anomalies.
- Compliance auditing: The tool provides pre-built compliance reports for regulatory standards such as GDPR, SOX, HIPAA, and more. These reports offer updated information on an organization's adherence to industry-specific security requirements.
- Real-time alerts: Firewall Analyzer produces immediate alerts for breaches in security policies or security incidents. This enables organizations to take proactive measures in response to potential threats. These alert notifications can be personalized, ensuring prompt action is taken before threats escalate.
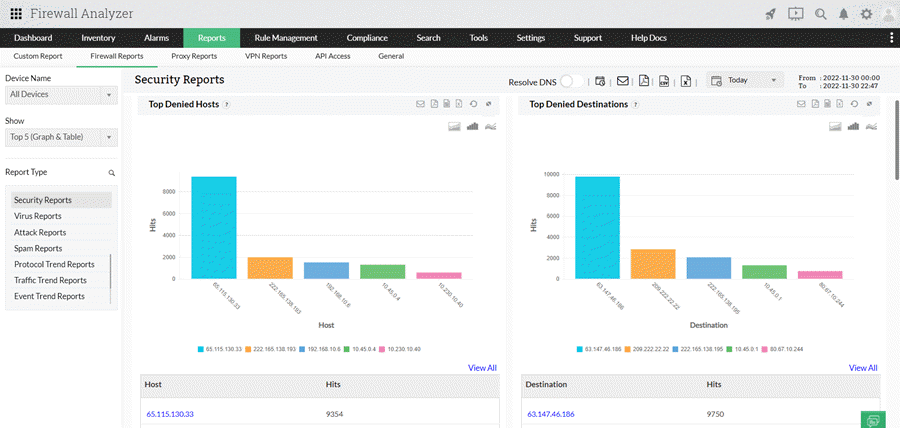
- Traffic analysis: Firewall Analyzer offers comprehensive graphs on traffic usage, bandwidth consumption, application usage, and similar trends. This valuable data assists organizations in enhancing network performance, capacity planning, and identifying possible security weaknesses.
- Historical and forensic analysis: This software provides forensic analysis capabilities and the ability to store historical log data. These functionalities are useful for investigating security incidents and identifying the underlying cause. By utilizing this tool, you can effectively implement preventive measures based on the insights gained from the analysis.
- User activity monitoring: Firewall Analyzer assists in monitoring user activity by tracking web application usage, login and logout times (including through VPN), identifying abnormal behavior, and preventing unauthorized actions.
Summary
Investing in a tool like Firewall Analyzer is no longer just a suggestion but a requirement in the current security landscape filled with threats. Carrying out security audits regularly can help detect vulnerabilities, enhance defenses, and uphold a robust network security stance for your organization. If you are interested, consider utilizing Firewall Analyzer by ManageEngine. You can sign up for a personalized demo or download Firewall Analyzer today for a free, 30-day trial.
Your IP address:
3.22.216.158
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!