Challenges & Solutions to Managing Firewall Rules in Complex Network Environments
 In today's interconnected digital landscape, where businesses rely heavily on networked systems and the internet for their operations, the importance of cybersecurity cannot be overstated. Among the essential tools in a cybersecurity arsenal, firewalls stand as a frontline defense against cyber threats and malicious actors.
In today's interconnected digital landscape, where businesses rely heavily on networked systems and the internet for their operations, the importance of cybersecurity cannot be overstated. Among the essential tools in a cybersecurity arsenal, firewalls stand as a frontline defense against cyber threats and malicious actors.
One of the primary functions of a firewall is to filter traffic, which entails scrutinizing packets of data to determine whether they meet the criteria set by the organization's security policies. This process involves examining various attributes of the data packets, such as source and destination IP addresses, port numbers, and protocols. By enforcing these rules, firewalls can thwart a wide range of cyber threats, including unauthorized access attempts, malware infections, denial-of-service attacks and more.
Enforcing and managing firewall rules effectively can be a daunting task, particularly in complex network environments with numerous rules, policies and configurations. While solutions like ManageEngine Firewall Analyzer step in, to offer a comprehensive way to streamline firewall rule management and enhance security posture, it’s worthwhile take a look at the real challenges firewall rule management present across all known platforms such as Cisco (FTD, Firepower, ASA), Palo AltoPalo Alto Next-Gen firewalls, Checkpoint, Fortinet, Juniper and more.
Key Topics:
- Challenges in Firewall Rule Management
- How to Simplify Firewall Rules
- The Benefits of Effective Firewall Rule Management
- Summary
Challenges with Firewall Rule Management
Traditional firewall rule management is a labor-intensive process. Manually adding, editing, and deleting rules is prone to errors, potentially leaving security gaps or inadvertently blocking legitimate traffic. Additionally, tracking complex rule interactions and identifying redundant or unused rules can be a daunting task. The complexity and sophistication of managing firewall rules only increases as the network scales. Here are some of the common issues encountered when managing firewall rules in a growing network:
Rule Proliferation
One of the primary challenges in firewall security appliance policy management is rule proliferation. As networks grow in complexity and scale, the number of firewall rules tends to increase exponentially, leading to a tangled web of policies that are difficult to manage and maintain. This proliferation often occurs as a result of ad-hoc rule creation to address specific security incidents or business requirements without proper documentation or governance. As a consequence, administrators may struggle to identify redundant or conflicting rules, leading to rule sprawl that hampers firewall performance and effectiveness. Moreover, the lack of visibility into rule dependencies and the dynamic nature of network traffic exacerbate the challenge, making it harder to enforce consistent policies and ensure compliance with security best practices.
Firewall rule proliferation poses a significant challenge, particularly when policies need to be created across multiple firewalls within an organization's network infrastructure. As the number of firewalls increases to accommodate various network segments, geographical locations, or security zones, the management complexity grows exponentially.
To mitigate rule proliferation, organizations must adopt a structured approach to policy management, including regular audits, rule optimization, and the implementation of automated tools to streamline rule creation, analysis, and documentation processes.
Rule Conflicts
Inconsistent or conflicting firewall rules can be likened to cracks in the armor of an organization's cybersecurity defense, rendering it susceptible to exploitation by malicious actors. These inconsistencies can accidently permit unauthorized access, compromise data integrity, or disrupt critical services, thereby exposing the organization to a myriad of cyber threats and potential breaches.
The complexity of modern network environments amplifies the challenge, as disparate rule sets across multiple firewalls increase the likelihood of conflicting directives that undermine the intended security posture. Identifying and resolving these conflicts demands a rigorous approach that entails thorough analysis and validation processes. Security teams must carefully scrutinize rule sets, examining factors such as rule precedence, overlapping conditions, and contradictory directives.
This time-consuming process involves tracing the path of network traffic through the firewall infrastructure, simulating various scenarios, and conducting real-world testing to assess the impact of rule changes. The ability to visualize rules across multiple firewalls, regardless the firewall vendor, is a significant game changer in this situation.
Finally, organizations must establish clear guidelines and governance frameworks to govern the creation, modification, and enforcement of firewall rules, fostering consistency and coherence across the entire network architecture, which brings us to our next challenge: Compliance requirements.
Compliance Requirements
Regulatory mandates and industry standards mandate strict adherence to security policies and access controls, placing significant pressure on organizations to ensure compliance across their firewall rules.
Achieving this alignment demands a complex approach that goes beyond mere rule creation. Continuous monitoring and enforcement mechanisms must be established to verify that firewall configurations meet the stringent requirements outlined by various compliance frameworks. This includes regularly assessing whether firewall rules adequately restrict access to sensitive data, comply with encryption standards, and adhere to segmentation requirements.
Unfortunately, the dynamic nature of compliance regulations, coupled with the complexity of modern network environments, intensifies the challenge.
How to Simplify Firewall Rule (Security Policy) Management
ManageEngine Firewall Analyzer offers a comprehensive set of features designed to simplify firewall rule management and optimize network security policies. Here is how Firewall Analyzer addresses the key challenges associated with firewall rule management:
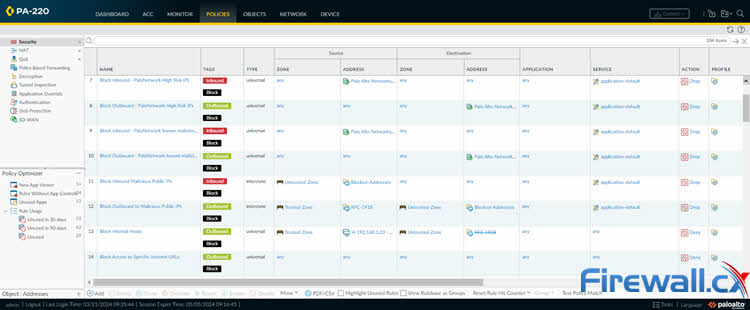
Rule Visualization
Firewall Analyzer provides a visual representation of firewall rules, allowing administrators to analyze rule sets, identify relationships, and visualize traffic flows. This intuitive interface simplifies rule management and facilitates rule optimization efforts:
By presenting firewall configurations in a graphical format, administrators can quickly analyze rule sets, identify relationships between rules, and visualize traffic flows within the network infrastructure. This visual depiction offers clarity and insight into the complexities of firewall policies, enabling administrators to discern patterns, pinpoint redundancies, and detect potential rule conflicts more efficiently than manual inspection of textual rule lists.
Moreover, graphical representations facilitate communication and collaboration among teams responsible for firewall management, as complex concepts can be conveyed in a clear and intuitive manner. By leveraging visualization tools, administrators can gain deeper insights into the behavior of network traffic, enhance the effectiveness of rule optimization efforts, and make informed decisions to strengthen overall security posture.
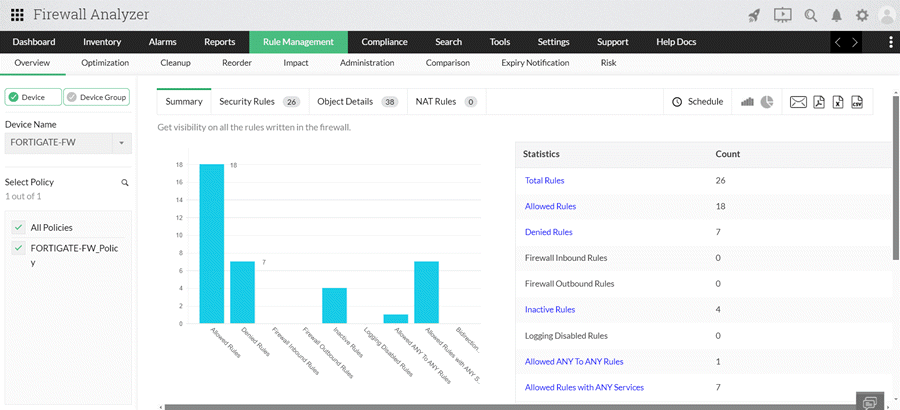
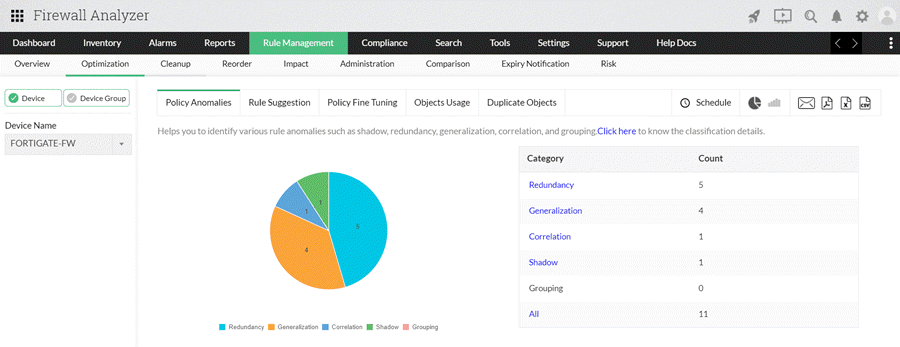
Rule Analysis and Optimization
Firewall Analyzer conducts rule analysis to identify shadowed, redundant, correlated, or unused rules within firewall configurations. By conducting in-depth analysis, Firewall Analyzer can identify poorly constructed or redundant rules that may introduce vulnerabilities or impair network performance. This feature evaluates rule sets based on various factors such as rule complexity, usage statistics, and compliance with best practices and industry standards.
By flagging inefficient or risky rules, administrators can prioritize optimization efforts to streamline rule sets and enhance overall security posture. By optimizing rule sets, organizations can improve firewall performance, reduce rule sprawl, and enhance security posture.
Furthermore, the risk analysis feature empowers administrators to make data-driven decisions regarding rule management, ensuring that firewall configurations align with the organization's security objectives and regulatory requirements.
Rule Change Tracking
The rule change tracking feature of Firewall Analyzer provides administrators with a comprehensive solution for monitoring and auditing firewall rule modifications. By maintaining a detailed log of all changes made to firewall rules, this feature enables administrators to track every change, whether it's a modification, addition, or deletion.
This level of visibility allows administrators to quickly identify unauthorized changes or suspicious activities that may compromise network security. In the event of a security incident or compliance violation, administrators can leverage the rule change tracking functionality to trace back to the root cause and take corrective actions promptly.
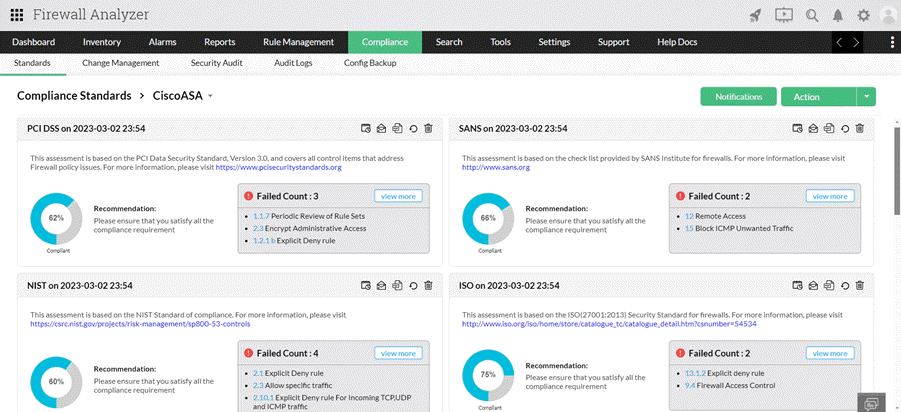
Rule Compliance Checks
Firewall Analyzer offers significant benefits through its rule compliance check feature, which plays a crucial role in ensuring adherence to regulatory standards and industry best practices. By conducting compliance checks against predefined benchmarks such as PCI DSS, NIST, ISO 27001, SANS, and others, the Firewall Analyzer provides organizations with a comprehensive assessment of their firewall rule sets.
This capability enables administrators to identify non-compliant rules that deviate from established security standards and regulatory requirements. By flagging these discrepancies, the Firewall Analyzer facilitates proactive risk management and regulatory compliance efforts.
Furthermore, the tool goes beyond merely identifying non-compliant rules by offering recommendations for remediation actions. These actionable insights empower administrators to address compliance gaps promptly, implement necessary adjustments to firewall configurations, and bolster the organization's security posture. With ManageEngine's Firewall Analyzer, organizations can streamline compliance management processes, mitigate regulatory risks, and uphold the integrity and confidentiality of their network environments.
Policy Documentation and Reporting
Generating comprehensive documentation and reports is essential for documenting firewall policies, demonstrating compliance, and facilitating audits. Firewall Analyzer automates the process of generating policy documentation and compliance reports, saving time and effort for IT teams.
The Benefits of Effective Firewall Rule Management
By leveraging ManageEngine Firewall Analyzer, you gain a multitude of benefits:
- Enhanced security: Optimized firewall rules minimize the risk of human error and ensure comprehensive network protection.
- Improved performance: Streamlined policies with fewer redundant rules lead to improved firewall performance and reduced processing overhead.
- Simplified compliance: Clear audit trails and efficient rule management make compliance audits a breeze.
- Reduced costs: Automation and proactive anomaly detection save time and resources, minimizing the need for manual intervention.
Summary
This article delved into the complexities of managing firewall rules. We thoroughly examined various hurdles such as the proliferation of rules, conflicts between them, compliance demands, and explored methods to streamline this process through the utilization of Firewall Analyzer's advanced functionalities. By leveraging its capabilities for rule visualization, analysis, change tracking, compliance checks, and reporting, organizations can efficiently oversee firewall rules and minimize the potential for security breaches.
Your IP address:
18.189.188.15
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!