Comparing DMVPN Single Tier and Dual Tier Headend Architectures - IPSec VPN & mGRE Termination
This article extends our DMVPN article series by answering common questions regarding the differences between Single Tier Headend and Dual Tier Headend architectures.
When hearing the DMVPN terms single tier or dual tier it can be difficult to understand exactly their meanings. While the difference between the two might seem clear when looking at a DMVPN with single or dual tier headend setup, what really goes on is usually not revealed or analysed in great depth, until now…
While there are plenty of diagrams online illustrating Single Tier and Dual Tier Headend architectures, we found none that would analyse the differences on a packet/protocol level. This is usually the level of analysis many engineers require to truly understand how each model works.
We always assume the DMVPN network (mGRE tunnel) is protected using the IPSecurity protocol.
Single Tier Headend
Single Tier Headend involves a DMVPN setup with one single Hub router responsible for all DMVPN services. Practically, this means both Crypto IPSec and mGRE tunnel terminate on the same router, the Hub.
This is illustrated in our detailed diagram below:

In Single Tier Headend IPSec runs in Tunnel Model, encrypting the whole GRE tunnel and Data carried within. This ensures true confidentiality of our GRE tunnel and provides great flexibility in terms of VPN network design.
Engineers and Administrators who would like to learn more about protecting GRE using IPSec (both Tunnel and Transport Mode) can read our popular GRE over IPSec - Selecting and Configuring GRE IPSec Tunnel or Transport Mode article. We high recommend the above article as it contains extremely useful information, not found easily!
As expected, a Single Tier Headend setup means that all processing is performed by one single device. The burden of encrypting, decrypting, encapsulating, decapsulating and maintaining the NHRP database falls on a single Hub. As a rule of thumb, the faster the Internet connection speed on the Hub router the bigger the burden will be on its CPU as it needs to process VPN data at a much faster rate. DMVPN scalability issues is a topic that will be covered on Firewall.cx.
DMVPN deployments based on Single Tier Headend architecture also support spoke-to-spoke VPN tunnels, allowing remote offices to dynamically build VPN tunnels between each other. Remote offices (spokes) are also configured with mGRE tunnels (like the Hub), allowing them to create the dynamic spoke-to-spoke tunnels.
Dual Tier Headend
Dual Tier Headend is a more popular approach to DMVPN, especially when it comes to VPN redundancy. Cisco usually uses this method when analysing DMVPN networks, however, this does not mean the Single Tier is not an acceptable solution.
With Dual Tier Headend Crypto IPSec terminates on a router positioned in front of the Hub, while the mGRE tunnel terminates on the Hub. This is illustrated in our detailed diagram below:
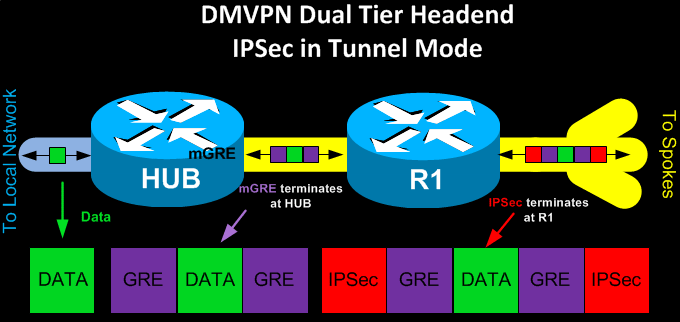
In Dual Tier Headend IPSec runs in Tunnel Model, encrypting the whole GRE tunnel and Data carried within. IPSec decryption occurs on R2, the Frontend router, and the mGRE tunnel is passed to the Hub where it terminates.
DMVPN deployments based on Dual Tier Headend architecture do not support spoke-to-spoke VPN tunnels. This limitation should be seriously considered if planning for this type of DMVPN deployment. This also explains why spoke routers in this deployment method are configured with single GRE tunnels (not mGRE).
Links To GRE - DMVPN - IPSec VPN Articles
Firewall.cx hosts a number of popular articles for those requiring additional information on DMVPN networks and IPSec VPNs. Below are a few hand-picked links to articles we are sure will be useful:
Your IP address:
3.147.47.202
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!













