Cisco Aironet 1242AG /1240 - Multiple SSID & 802.1q Trunk VLAN Link Configuration
This article explains how the Cisco 1240 series access point can be setup to provide support for multiple SSID, each SSID assigned to a separate VLAN. This type of configuration is ideal for supporting different wireless networks, each one with its own characteristics.
Frequently used setup of Cisco access points involve at least one wireless network (SSID) for accessing the local network (VLAN1) and another SSID for Internet access (Guest VLAN).
It is important to note that this guide is also valid for the following Cisco Access Points: Cisco Aironet 1240 Series, Cisco Aironet 1040 series, Cisco Aironet 1130 AG Series, Cisco Aironet 1140 Series, Cisco Aironet 1200 Series, Cisco Aironet 1250 Series and Cisco Aironet 1260 Series. Configuration of multiple SSIDs with Trunk links is almost identical, with minor differences in the interfaces (where we have more than one radio) and channels, depending if there is support for 802.11a/b/g/n.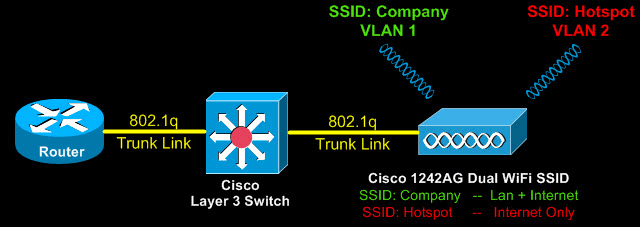
Cisco Access Point Multiple SSID Configuration
Configuring multiple SSIDs on a Cisco access point is a straight-forward process, however it does contain a few details we will analyse as we progress.
We need to now create the two SSIDs by defining their name, which will be broadcasted so users can find them, encryption method plus keys and VLAN assignment.
AP (config-ssid)# vlan 1
AP (config-ssid)# authentication open
AP (config-ssid)# authentication key-management wpa
AP (config-ssid)# guest-mode
AP (config-ssid)# mbssid guest-mode
AP (config-ssid)# infrastructure-ssid optional
AP (config-ssid)# wpa-psk ascii 0 firewall.cx
AP (config-ssid)# exit
AP (config)# dot11 ssid Hotspot
AP (config-ssid)# vlan 2
AP (config-ssid)# authentication open
AP (config-ssid)# authentication key-management wpa
AP (config-ssid)# mbssid guest-mode
AP (config-ssid)# wpa-psk ascii 0 free-access
AP (config-ssid)# exit
AP (config)# dot11 vlan-name vlan1 vlan1
AP (config)# dot11 vlan-name vlan2 vlan2
The above configuration is quite different from setups with one SSID. Reason being the multiple SSID and VLAN configuration required to ensure each SSID is assigned to the correct vlan. The 'Company' wireless network is assigned to VLAN 1 and the 'Hotspot' wireless network to VLAN 2.
Notice that when using multiple SSIDs on a Cisco aironet access point, it is imperative to use the mbssid guest-mode command otherwise the SSID name of the wireless network will not be broadcasted correctly.
The 'dot11 <vlan-name>' command ensures the correct mapping of vlans and their respective VLAN names. In our example, the VLAN names follow the actual VLANs. So, VLAN 1 has been named 'vlan1'. This helps keep track of them.
Next, we must ensure the integrated routing and bridging (IRB) feature is enabled to allow the routing of our protocols (IP) between routed interfaces and bridge groups. This command is most likely already present in the configuration, but let's play safe and enter it:
Configuring The Dot11Radio0 Interface
Configuring the Dot11Radio0 interface is our next step. Dot11Radio0 is the actual radio interface of the integrated Cisco access point. We will need to assign the SSIDs configured previously to this interface, along with the encryption methods and a few more parameters.
AP (config-if)# encryption vlan1 mode ciphers tkip
AP (config-if)# encryption vlan2 mode ciphers tkip
AP (config-if)# ssid Company
AP (config-if)# ssid Hotspot
AP (config-if)# mbssid
AP (config-if)# station-role root
AP (config-if)# speed basic-1.0 2.0 5.5 11.0 6.0 9.0 12.0 18.0 24.0 36.0 48.0 54.0
AP (config-if)# channel 2462
Most commands are self-explanatory. We will however explain the basic and important ones:
The Encryption VLAN commands set the encryption mode for each VLAN and, therefore, each SSID.
The SSID command assigns the SSIDs to this interface.
The mbssid command ensures both SSIDs are broadcast and are viewable to our wireless clients.
The station-role root is a default command and makes the access point act as a root station, in other words as an autonomous access point.
Note the speed basic command. This as well is a default command that sets the supported speeds. The first portion, 1.0 to 54.0 refers to the 802.11 b/g protocol. If you have a dual radio on your access point you can configure the Dot11Radio1 (Second radio) interface accordingly.
Configuring The Dot11Radio0 Sub-interfaces
At this point we are required to configure sub-interfaces on Dot11Radio0, assigning each sub-interface to a VLAN.
AP (config-subif)# encapsulation dot1Q 1 native
AP (config-subif)# no ip route-cache
AP (config-subif)# bridge-group 1
AP (config-subif)# bridge-group 1 subscriber-loop-control
AP (config-subif)# bridge-group 1 block-unknown-source
AP (config-subif)# no bridge-group 1 source-learning
AP (config-subif)# no bridge-group 1 unicast-flooding
AP (config-subif)# bridge-group 1 spanning-disabled
AP (config)# exit
AP (config)# interface Dot11Radio0.2
AP (config-subif)# encapsulation dot1Q 2
AP (config-subif)# no ip route-cache
AP (config-subif)# bridge-group 2
AP (config-subif)# bridge-group 2 block-unknown-source
AP (config-subif)# no bridge-group 2 source-learning
AP (config-subif)# no bridge-group 2 unicast-flooding
AP (config-subif)# bridge-group 2 spanning-disabled
When creating the subinterfaces, we always use easy-to-identify methods of mapping. Thus, interface Dot11Radio0.1 means this interface will be mapped to VLAN 1, while interface Dot11Radio0.2 will map to VLAN 2.
The encapsulation dot1Q 1 native command surves two purposes. It maps VLAN 1 to sub-interface Dot11Radio0.1 and tells the ap that this VLAN (1) is the native vlan. This means that untagged VLAN traffic belongs to VLAN 1. More information on VLAN is available in our VLAN Section - be sure to visit it.
Similarly, under interface Dot11Radio0.2, the encapsulation dotQ 2 command maps VLAN 2 traffic to this sub-interface.
The bridge-group command assigns each sub-interface to a bridge group. Each sub-interface is assigned to its own bridge-group. The bridge group essentially connects the wireless sub-interfaces with the Fast Ethernet interface this access point has. This is analysed below.
Configuring Cisco 1242AG / 1240 Access Point Fast Ethernet0, Sub-Interfaces & BVI interface
As with all Cisco Aironet access points, you'll find a Fast Ethernet0 interface that is used to connect the access point to our LAN switch. On Cisco Aironet models that support 802.11n technology e.g Cisco Aironet 1140, this interface is replaced with a Gigabit Ethernet interace, desinged to handle the increased capacity and throughput of the access point.
Following is the configuration required to create the necessary GigabitEthernet sub-interfaces and map the Dot11Radio0.X interfaces previously created, with them:
AP (config-if)# no ip address
AP (config-if)# no ip route-cache
AP (config-if)# exit
AP (config)# interface FastEthernet0.1
AP (config-if)# encapsulation dot1Q 1 native
AP (config-if)# no ip route-cache
AP (config-if)# bridge-group 1
AP (config-if)# no bridge-group 1 source-learning
AP (config-if)# bridge-group 1 spanning-disabled
AP (config-if)# exit
AP (config)# interface FastEthernet0.2
AP (config-if)# encapsulation dot1Q 2
AP (config-if)# no ip route-cache
AP (config-if)# bridge-group 2
AP (config-if)# no bridge-group 2 source-learning
AP (config-if)# bridge-group 2 spanning-disabled
AP (config-if)# exit
AP (config)# interface BVI1
AP (config-if)# ip address 192.168.30.5 255.255.255.0
AP (config-if)# no ip route-cache
The FastEthernet interface and sub-interface configuration follows the same logic as the Dot11Radio0 interface. Notice that each FastEthernet sub-interface is mapped to the same VLAN and bridge-group as the Dot11Radio0 sub-interfaces.
Next, we create the one and only BVI1 interface and assign it an IP Address. This is basically the IP Address of our access point and is reachable from our LAN network, so it's best to assign it an IP Address from your LAN network (VLAN 1).
It is important to note that only one bridge-interface (BVI Interface) is configured with an IP Address. The rest of the bridge groups are not required to have a BVI interface as all traffic is trunked through the BVI1 Interface. This is per Cisco design.
Finally, we must enable ip routing for bridge 1:
AP (config)# bridge 1 route ip
Configuring DHCP Service For Both VLAN Interfaces
First step is to define the DHCP service and ip address pools for our two Vlans, and therefore SSID's.
If you prefer to configure the DHCP service on your Cisco router, detailed instructionscan be found at our Cisco Router DHCP Server Configuration article.
To help make it easy, we are providing the necessary commands for our example:
AP(config)# ip dhcp excluded-address 192.168.40.1 192.168.40.20
AP(config)# ip dhcp pool Company
AP(dhcp-config)# network 192.168.30.0 255.255.255.0
AP(dhcp-config)# dns-server 192.168.30.1
AP(dhcp-config)# default-router 192.168.30.1
AP(config)# ip dhcp pool Hotspot
AP(dhcp-config)# network 192.168.40.0 255.255.255.0
AP(dhcp-config)# default-router 192.168.40.1
AP(dhcp-config)# dns-server 192.168.40.1
This configuration assumes that your router has two VLAN interfaces configured with the appropriate Internet access and Firewall configuration.
On another note, NAT Overload is required in most cases to ensure both VLAN networks have Internet access.. This is covered extensively in our Cisco Router NAT Overload article.
Summary
This article provided an in-depth coverage on how to configure a Cisco Aironet 1242AG / 1240 series access point to support multiple SSID wireless networks and connect via 802.1q Trunk link to a local switch. The information provided not only covers the basic commands, but also analyses the background theory and logic, to ensure the reader fully understands why this configuration method is used.
Your IP address:
18.225.10.66
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!