Detecting Windows Server Security Threats with Advanced Event Log Analyzers
 Windows Servers stand as prime targets for hackers and malicious actors due to their widespread usage and historical vulnerabilities. These systems often serve as the backbone for critical business operations, housing sensitive data and facilitating essential services. However, their prevalence also makes them vulnerable to cyber threats, including ransomware attacks, distributed denial-of-service (DDoS) assaults and more.
Windows Servers stand as prime targets for hackers and malicious actors due to their widespread usage and historical vulnerabilities. These systems often serve as the backbone for critical business operations, housing sensitive data and facilitating essential services. However, their prevalence also makes them vulnerable to cyber threats, including ransomware attacks, distributed denial-of-service (DDoS) assaults and more.
Windows Servers have a documented history of vulnerabilities and exploits, which further intensifies their attractiveness to attackers seeking to exploit weaknesses for unauthorized access or data theft. Consequently, it is paramount for organizations to prioritize mitigating these risks and safeguarding the integrity and continuity of operations within Windows Server environments.
Fortunately, tools like EventLog Analyzer offer robust capabilities for automatically identifying and countering such threats, uplifting the security posture of Windows Server setups. To effectively leverage these defenses, it's imperative to understand the nature of common Windows server threats and how they manifest. In this document, we delve into several prevalent threats targeting Windows servers and outline strategies for their detection and mitigation.
Furthermore, implementing robust security measures, such as regular patching, network segmentation, intrusion detection systems, and data encryption, Windows VM Backups, is essential to fortify Windows Servers against potential threats and ensure the resilience of critical business functions.
Key Topics:
- Common Windows Server Threats
- Ransomware
- Denial of Service Attacks
- Insider Threats
- Malware Infections
- Phishing Attacks
- Brute Force Attacks
- Vulnerability Exploitation
- Data Breaches
- Web Application Attacks
- Misconfiguration Errors
- Using Advanced Event Log Analyzers to Detect Server Threats
- EventLog Analyzer: Ransomware Detection
- EventLog Analyzer: DoS Attack Detection
- EventLog Analyzer: Insider Threat Detection
- Moving Forward with Robust Log Management Solutions
- Summary
Common Windows Server Threats
 There are many wide known Windows server threats that exist in the landscape, but in this document, we'll be discussing the following:
There are many wide known Windows server threats that exist in the landscape, but in this document, we'll be discussing the following:
- Ransomware: Malicious software that encrypts data on the server, demanding payment for decryption.
- Denial of Service (DoS) Attacks: Floods the server with excessive traffic, overwhelming its resources and causing it to become inaccessible to legitimate users.
- Insider Threats: Malicious actions or negligence by employees or authorized users, leading to unauthorized access, data theft, or system sabotage.
- Malware Infections: Viruses, worms, or trojans that infect the server, compromising its functionality and potentially spreading to other systems.
- Phishing Attacks: Deceptive emails or messages aimed at tricking server users into revealing sensitive information or installing malicious software.
- Brute Force Attacks: Attempts to gain unauthorized access to the server by systematically trying various username/password combinations until successful.
- Vulnerability Exploitation: Exploiting known security vulnerabilities in Windows Server software or configurations to gain unauthorized access or execute malicious code.
- Data Breaches: Unauthorized access or disclosure of sensitive data stored on the server, often resulting in reputational damage and regulatory penalties.
- Web Application Attacks: Exploiting vulnerabilities in web applications hosted on the server to gain unauthorized access, inject malicious code, or steal data.
- Misconfiguration Errors: Incorrect server configurations or settings that inadvertently expose vulnerabilities or weaken security defenses.
Let's dive in and explore how these threaten Windows servers.
Ransomware
Ransomware poses a significant threat to Windows Servers, encrypting critical files and demanding ransom payments for their release. This malicious software can cripple operations, disrupt business continuity, and lead to financial losses if not promptly addressed.
Denial of Service (DoS)
DoS attacks target Windows Servers by flooding them with an overwhelming amount of traffic, rendering them inaccessible to legitimate users. These attacks can disrupt services, degrade performance, and compromise the availability of critical resources.
Insider Threat
Insider threats emanate from within the organization, where employees or insiders misuse their privileges to steal sensitive data, sabotage systems, or compromise security. These threats can be challenging to detect and mitigate due to their intimate knowledge of organizational systems and processes.
Malware Infections
Malware infections pose a significant threat to Windows servers, jeopardizing their security and functionality in several ways. Once infiltrated, malware can compromise the confidentiality, integrity, and availability of data and services hosted on the server. It may execute unauthorized commands, manipulate or destroy critical files, or even install additional malicious software, exacerbating the damage.
Phishing Attacks
Through deceptive emails, messages, or websites, attackers trick server users into divulging sensitive information such as usernames, passwords, or financial data. Once obtained, these credentials can be leveraged to gain unauthorized access to the server or other network resources. Moreover, phishing emails often contain malicious attachments or links that, when clicked, can install malware onto the server, further compromising its security.
Brute Force Attacks
Brute force attacks present a significant threat to the security of Windows servers by exploiting weaknesses in authentication systems. In these attacks, malicious actors systematically attempt to guess usernames and passwords until they gain unauthorized access to the server. Because Windows servers often utilize usernames and passwords for authentication, they are particularly vulnerable to this type of assault. Once an attacker successfully breaches the server's defenses, they can potentially gain unrestricted access to sensitive data, compromise critical systems, or even disrupt essential services.
Vulnerability Exploitation
Vulnerability exploitation represents a significant threat to the security of Windows servers, as attackers leverage known weaknesses in server software or configurations to gain unauthorized access or execute malicious code. These vulnerabilities can stem from various sources, including outdated software versions, misconfigurations, or unpatched security flaws. Once an attacker identifies and exploits a vulnerability in a Windows server, they can potentially execute arbitrary commands, escalate privileges, or exfiltrate sensitive data.
Data Breaches
Data breaches pose a substantial threat to the integrity and security of Windows servers, potentially resulting in severe consequences for organizations. When attackers successfully breach the defenses of a Windows server, they gain unauthorized access to sensitive data stored within the system.
This can include personally identifiable information, financial records, intellectual property, and other confidential data crucial to the organization's operations. Once compromised, this data can be exploited for various nefarious purposes, including identity theft, financial fraud, espionage, or extortion.
Web Application Attacks
Web application attacks pose a significant threat to the security of Windows servers by exploiting vulnerabilities in the web applications hosted on these servers. Attackers target weaknesses such as input validation flaws, SQL injection, cross-site scripting (XSS), and authentication bypass to gain unauthorized access or manipulate the application's functionality. Once compromised, attackers can steal sensitive data, modify content, or even gain control over the server itself.
Misconfiguration Errors
Misconfiguration errors represent a significant threat to the security and stability of Windows servers, as they can inadvertently expose vulnerabilities and weaken the server's defenses. Common misconfigurations include improperly configured access controls, insecure network settings, outdated software versions, and inadequate security policies. These errors can create openings for attackers to exploit, allowing them to gain unauthorized access, manipulate server resources, or compromise sensitive data.

Using Advanced Event Log Analyzers to Detect Server Threats
In the subsequent sections, we will exemplify how EventLog Analyzer effectively identifies the aforementioned threats, thereby aiding network security engineers, system administrators, and other IT personnel in managing these risks. Simultaneously, such capabilities substantially elevate the organization's security stance. Recognizing and addressing potential threats at an early stage is imperative for promptly intercepting and mitigating hacker activities.
EventLog Analyzer: Ransomware Detection
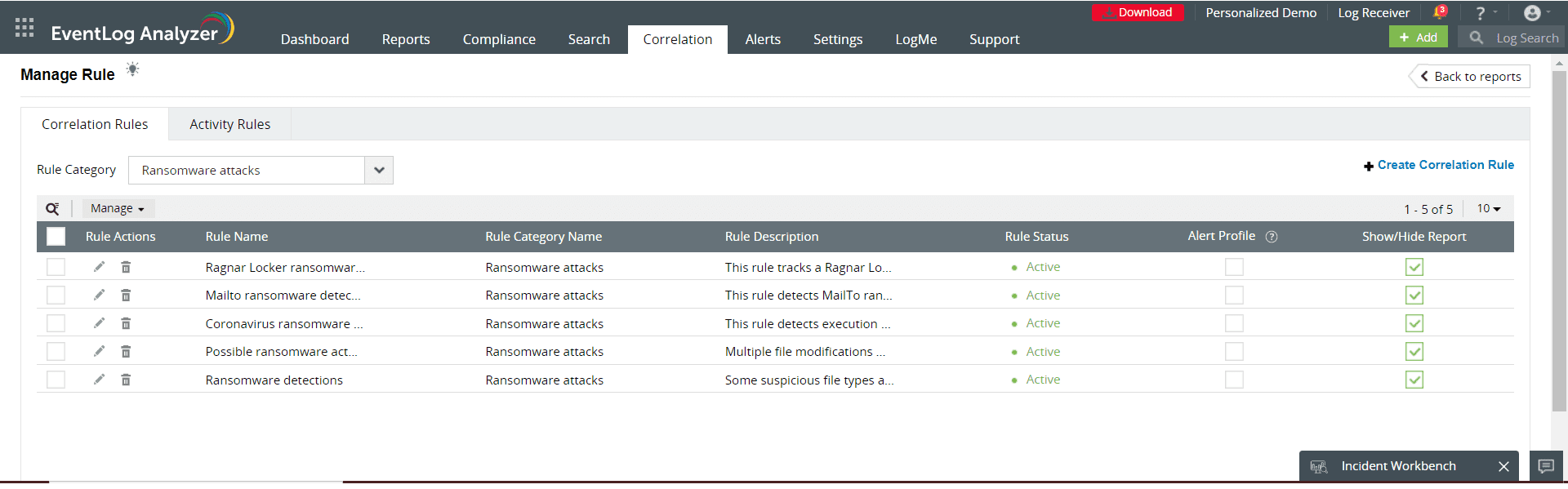
EventLog Analyzer utilizes advanced threat detection algorithms to identify ransomware activity within Windows Server environments. By monitoring file modification and deletion patterns, detecting abnormal encryption behaviors, and leveraging out-of-the-box pre-define correlation rules for ransomware detection, EventLog Analyzer can swiftly alert administrators to potential ransomware incidents. The below image shows the pre-defined correlation rule categories that EventLog Analyzer provides for ransomware.
EventLog Analyzer: DoS Attack Detection
EventLog Analyzer employ network traffic analysis and advanced log monitoring techniques to recognize DoS attack patterns targeting Windows Servers. By utilizing network device auditing providing insights into routers, switches, firewalls, and more, EventLog Analyzer can detect and mitigate DoS attacks in real-time, ensuring uninterrupted service availability. EventLog Analyzer provides pre-defined reports for detecting DoS activity and granular activity such as the Firewall Ping of Death. EventLog Analyzer also provides the capability to design correlation rules with actions to detect DoS activity.
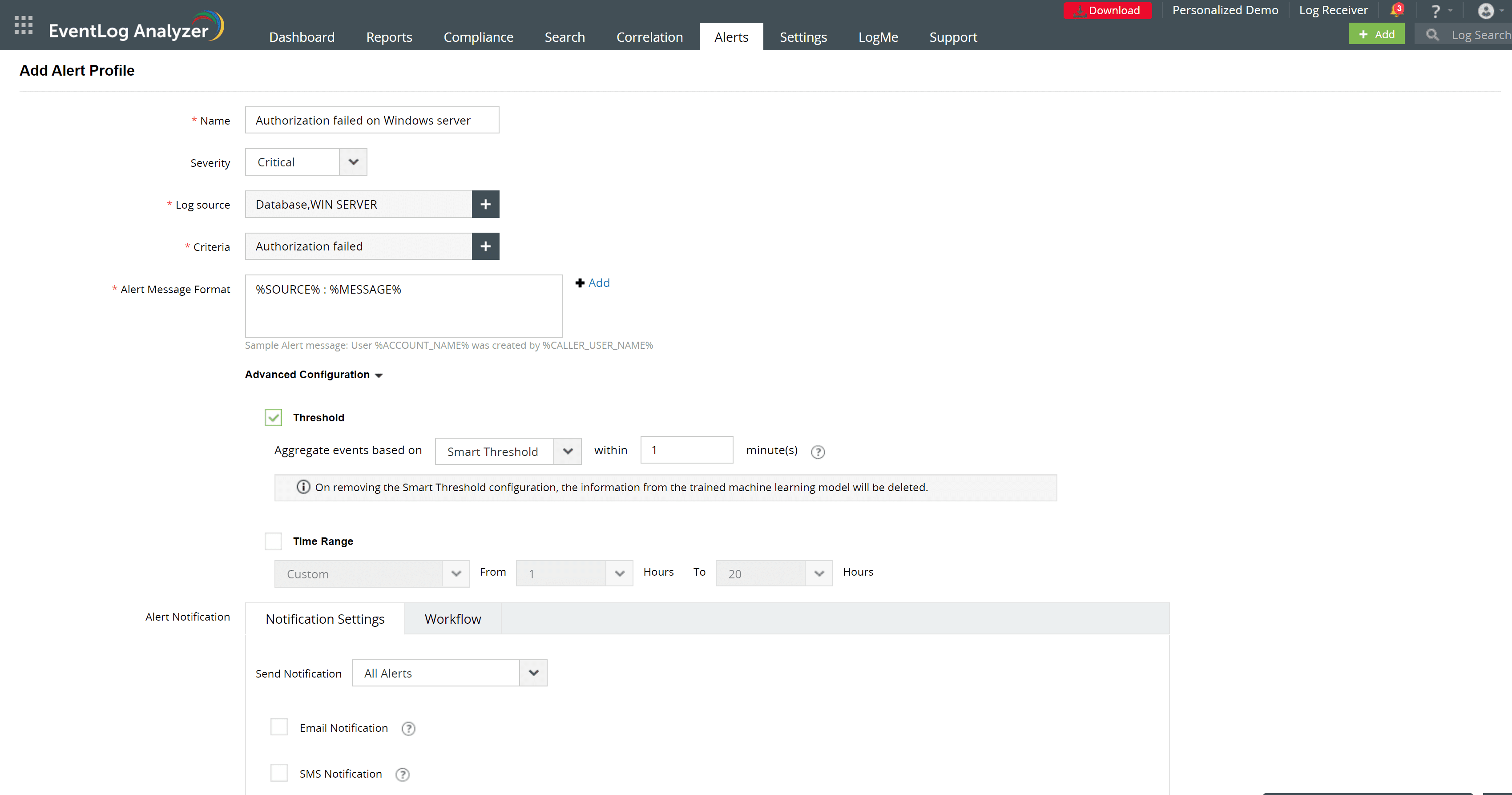
EventLog Analyzer: Insider Threat Detection
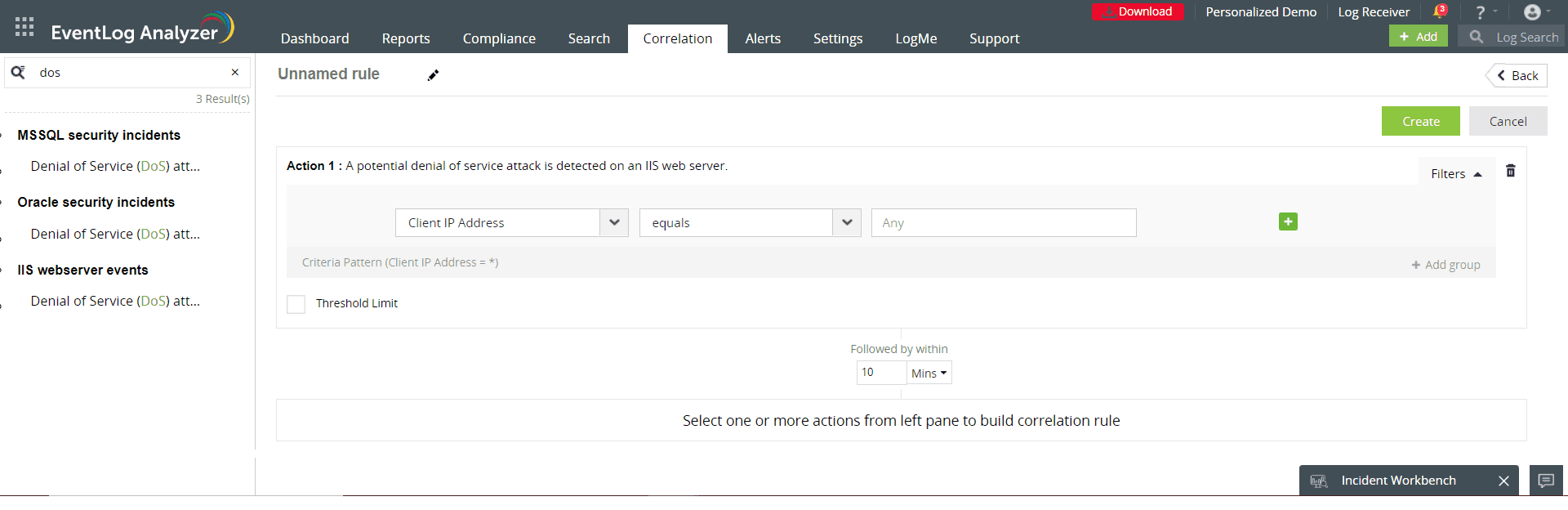
EventLog Analyzer play a crucial role in identifying insider threats by analyzing user behavior, access patterns, and system interactions. By monitoring privileged user activities, flagging suspicious behavior deviations using capabilities such as smart threshold, and correlating events across multiple data sources, EventLog Analyzer can detect insider threats early and mitigate potential risks to Windows Server security. The below image shows an alert profile set-up that can detect potential insider threat activity leveraging smart thresholds. Smart threshold leverages machine learning to automatically create threshold baselines and reduce false positive alerts.
Moving Forward with Robust Log Management Solutions
In conclusion, while the landscape of Windows Server threats continues to evolve, organizations can mitigate risks and bolster their security posture by leveraging robust log management solutions. By aggregating and analyzing log data from various sources, including system events, network activity, and user actions, organizations can proactively detect and respond to threats such as ransomware, denial of service attacks, and insider threats. With the insights provided by a comprehensive log management solution, organizations can strengthen their defenses, safeguard critical assets, and maintain the integrity and availability of their Windows Server environments in the face of evolving cybersecurity challenges.
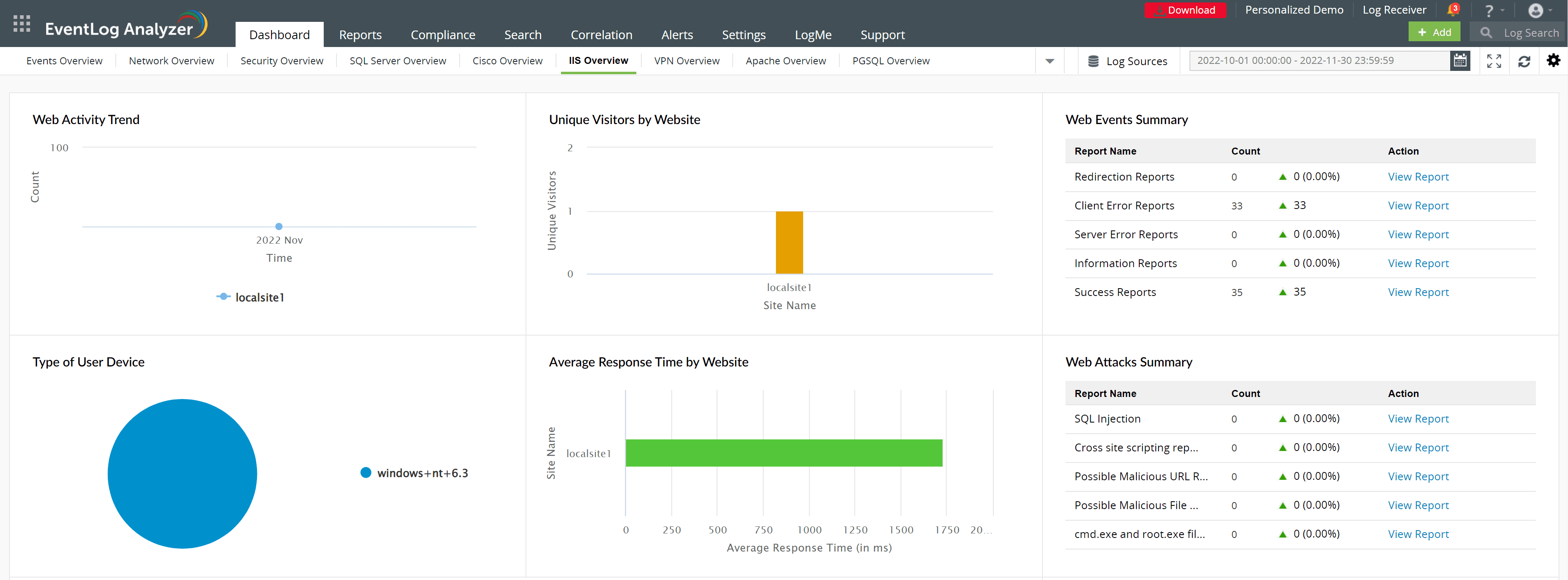
The image below shows EventLog Analyzer's IIS server visualization capabilities. The widgets can be customized based on the organization's contextual needs.
ManageEngine EventLog Analyzer is a log management, auditing, and IT compliance tool that can elevate your team's capabilities. With features such as cross-platform auditing and threat analytics, EventLog Analyzer can help in the detection of complex attacker tactics and techniques.
Summary
This article clarified the inherent vulnerabilities of Windows servers and the reasons behind their appeal to hackers and malicious actors. It underscored the criticality of safeguarding Windows server environments against a plethora of threats, encompassing ransomware, DoS attacks, malware infections, phishing assaults, brute force intrusions, vulnerability exploitation, and beyond. Moreover, it delved into the pivotal role of advanced solutions like EventLog Analyzer, not only in swiftly detecting threats and attacks but also in effectively mitigating them.
Your IP address:
3.142.212.2
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!