Installation and Configuration of Fine-Grained Password Policy for Windows Server 2012
 Microsoft introduced Fine-Grained Password Policy for the first time in Windows Server 2008 and the policy has been part of every Windows Server since then. Fine-Grained Password Policy allows overcoming the limitations of only one password policy for a single domain. A brief example is that we apply different password and account lockout policies to different users in a domain with the help of Fine-Grained Password Policies.
Microsoft introduced Fine-Grained Password Policy for the first time in Windows Server 2008 and the policy has been part of every Windows Server since then. Fine-Grained Password Policy allows overcoming the limitations of only one password policy for a single domain. A brief example is that we apply different password and account lockout policies to different users in a domain with the help of Fine-Grained Password Policies.
This article discusses the Fine-Grained Password Policy as applicable to Windows Server 2012, and the different ways of configuring this policy. Windows Server 2012 allows two methods of configuring the Fine-Grained Password Policy:
1. Using the Windows PowerShell
2. Using the Active Directory Administrative Center or ADAC
In earlier Windows Server editions, it was possible to configure Fine-Grained Password Policy only through the command line interface (CLI). However with Windows Server 2012 a graphical user interface has been added, allowing the configuration of the Fine-Grained Password Policy via the Active Directory Administrative Center. We will discuss both the methods.
Before you begin to implement the Fine-Grained Password Policy, you must make sure the domain functional level must be Windows Server 2008 or higher. Refer to relevant Windows 2012 articles on our website Firewall.cx.
Backup your Windows Server 2012 R2 host using Altaro’s Free Hyper-V & VMware Backup solution. Download Now!
Configuring Fine-Grained Password Policy From Windows PowerShell
Use your administrative credentials to login to your Windows Server 2012 domain controller. Invoke the PowerShell console by Right clicking on the third icon from the left in the taskbar on the Windows Server desktop and then clicking on Run as Administrator.
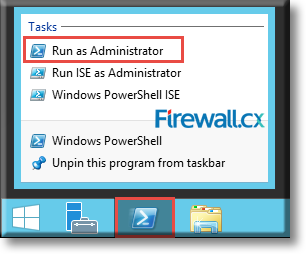
Figure 1. Executing Windows PowerShell as Administrator
Clicking on Yes to the UAC confirmation will open up an Administrator: Windows PowerShell console.
Within the PowerShell console, type the following command in order to begin the creation of a new fine grained password policy and press Enter:
C:\Windows\system32> New-ADFineGrainedPasswordPolicy
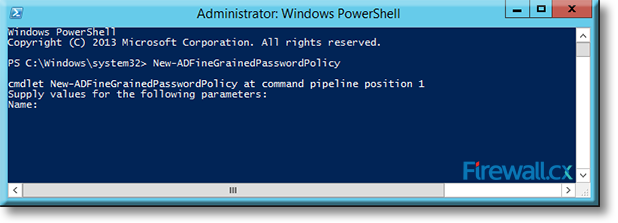
Figure 2. Creating a new Fine Grained Password Policy via PowerShell
Type a name for the new policy at the Name: prompt and press Enter. In our example, we named our policy FGPP:
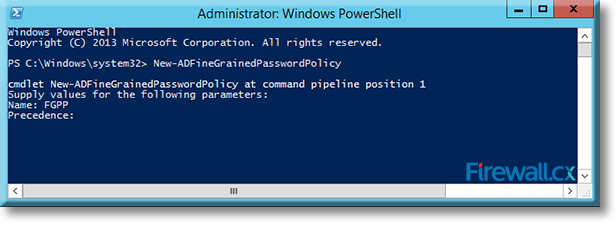
Figure 3. Naming our Fine Grained Password Policy
Type a precedence index number at the Precedence: prompt and press Enter. Note that policies that have a lower precedence number have a higher priority over those with higher precedence numbers. We’ve set our new policy with a precedence of 15: 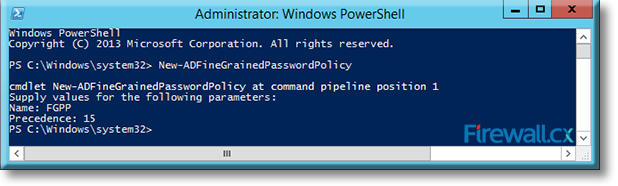
Figure 4. Setting the Precedence index number of our Fine Grained Password Policy
Now the policy is configured, but has all default values. If there is need to add specific parameters to the policy, you can do that by typing the following at the Windows PowerShell command prompt and press Enter:
C:\Windows\system32> New-ADFineGrainedPasswordPolicy -Name FGPP -DisplayName FGPP -Precedence 15 -ComplexityEnabled $true -ReversibleEncryptionEnabled $false -PasswordHistoryCount 20 -MinPasswordLength 10 -MinPasswordAge 3.00:30:00 -MaxPasswordAge 30.00:30:00 -LockoutThreshold 4 -LockoutObservationWindow 0.00:30:00 -LockoutDuration 0.00:45:00
In the above command, replace the name FGPP with the name of your password policy, which in our example is FGPP.
The parameters used in the above are mandatory and pretty much self-explanatory:
Attributes for Password Settings above include:
- Enforce password history
- Maximum password age
- Minimum password age
- Minimum password length
- Passwords must meet complexity requirements
- Store passwords using reversible encryption
Attributes involving account lockout settings include:
- Account lockout duration
- Account lockout threshold
- Reset account lockout after
To apply the policy to a user/group or users/groups, use the following command at the PowerShell command prompt:
For confirming whether the policy has indeed been applied to the groups/users correctly, type the following command at the PowerShell command prompt and press Enter:
Remember, it is necessary to replace FGPP in the above with the name of your password policy. Also replace Chris_Partsenidis with the name of the group or user to whom you want to apply the policy.
The screenshot below shows the execution of the commands and output:
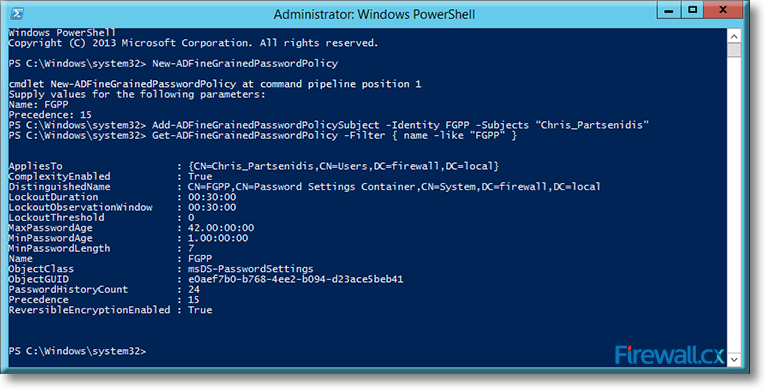
Figure 5. Applying and verifying a Fine Grained Password Policy to a User or Group
Check the AppliesTo section from the output to verify if the policy is applied to the intended user or group.
Configuring Fine-Grained Password Policy Using The Active Directory Administrative Center (ADAC)
Use your administrative credentials to login to your Windows Server 2012 domain controller. Invoke the Server Manager Dashboard by left-clicking on the second icon in the taskbar on the Windows Server desktop:

Figure 6. Opening Server Manager Dashboard
In the Server Manager Dashboard, go to the top right hand corner, click on Tools and then click on Active Directory Administrative Center:
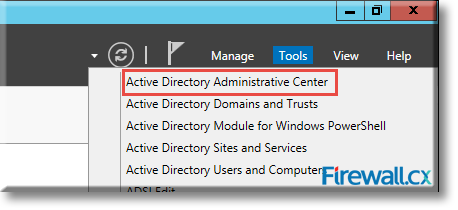
Figure 7. Launching Active Directory Administrative Center
Once the Active Directory Administrative Center screen is open, from the left panel, select the Active Directory (local) to expand.
In our example, the active directory is firewall (local). Locate Systems, expand it and click on Password Settings Container:
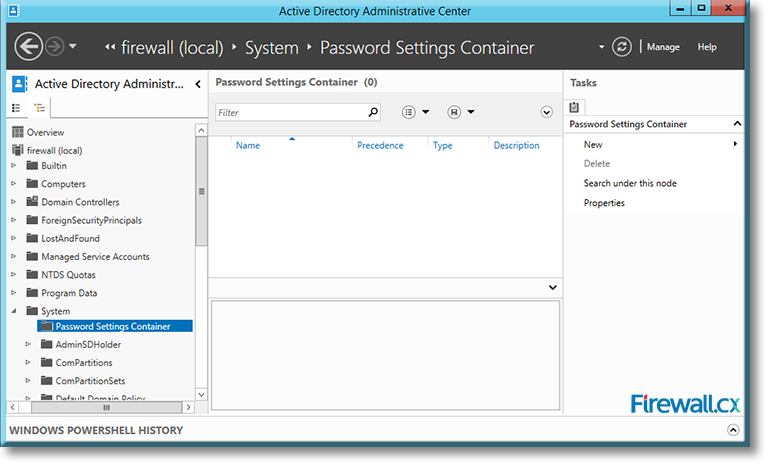
Figure 8. Locating the Password Settings Container
On the right panel, under Tasks and Password Settings Container, click on New:
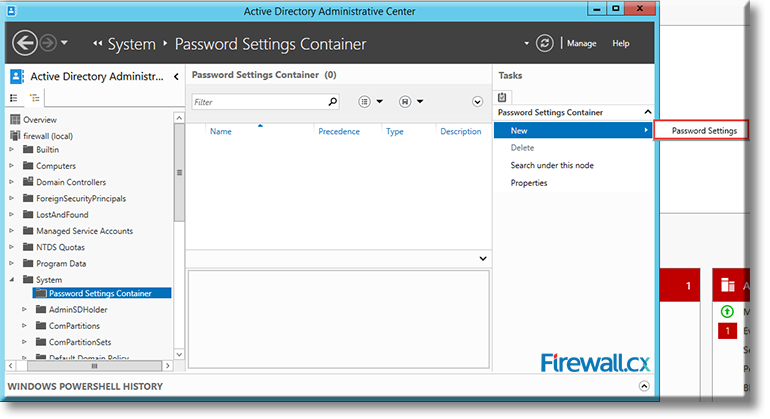
Figure 9. Accessing Password Settings Container
Now click on Settings, which will open up the Create Password Settings screen. Enter a name for the Fine-Grained Password Policy and a number for its precedence.
For our example, we are using the name FGPP or Firewall Group Password Policy with a precedence index of 15. Also, configure the remainder of the policy settings as required:
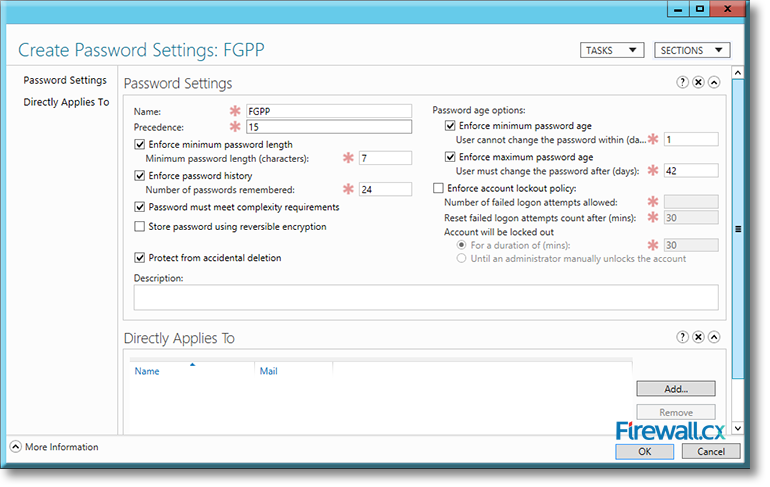
Figure 10. Configuring settings for our FGPP Policy
Once satisfied with the settings, click on Add at the bottom right hand corner. This will open up the Select Users or Groups dialog.
Click on Object Types to select either Users or Groups or both. Click on Locations to select the domain, which in our case is firewall.local.
Under the object names to select, type the name of the group or user on whom you want to apply the password policy. In our example, this is Chris_Partsenidis as shown below:
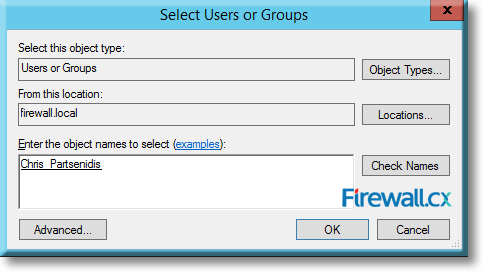
Figure 11. Selecting the Active Directory object to which the Fine Grained Password Policy will be applied to
Click on OK, and you will return to the Create Password Settings screen, which will now have the new name FGPP on top and the name of the user (to whom the policy will apply) at the bottom:
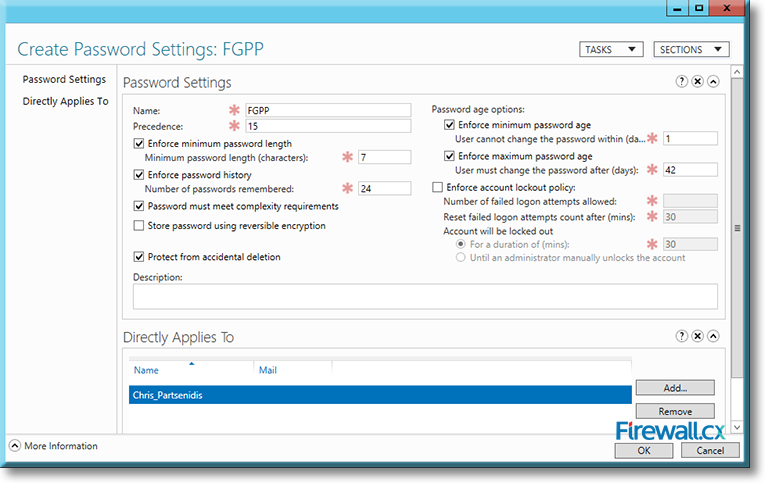
Figure 12. Our Fine Grained Password Policy
Click on OK to complete the process and go back to the Active Directory Administrative Center, which will now show the new Password Settings Container with the name FGPP and the precedence index in the center panel:
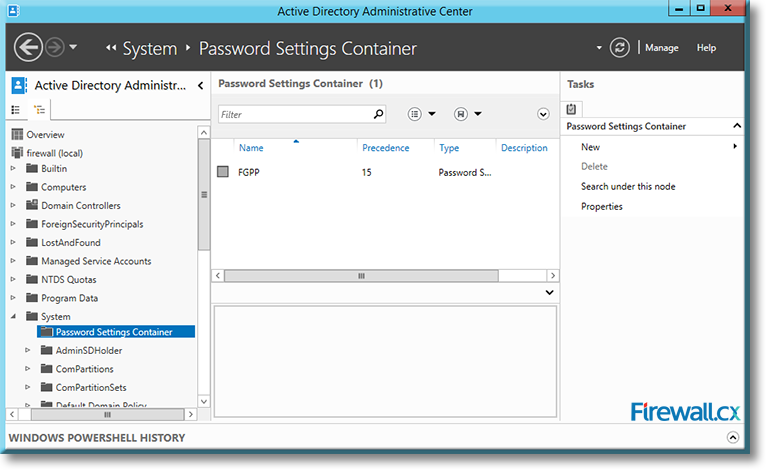
Figure 13. Our Fine Grained Password Policy appearing in the Password Settings Container
To modify any parameter, double click on the Password Settings Container in the central panel. Finally, when you are done, close the Active Directory Administrative Center window.
This article covered the installation and configuration of Fine-Grained Password Policies for Windows Server 2012. We explained how Fine-Grained Password Policies can be installed via PowerShell and the Active Directory Administrative Center. Our step-by-step guide shows all the necessary details to ensure a successful installation and configuration. More high-quality articles can be found in visit our Windows 2012 Section.
Your IP address:
3.23.102.52
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!













