Articles
To read the articles in this section, simply click on the article title or read button on the far right (if visible).
Use the below filters to customise the number of articles displayed or search for specific title topics/keywords.
| Articles | |
|---|---|
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
|
Articles:
Introduction to Routing Protocols
| Read |
| Read | |
|
Articles:
Interior Gateway Protocol - IGRP
| Read |
| Read | |
|
Articles:
Routing Information Protocol - RIP
| Read |
| Read | |
|
Articles:
Link State Routing Protocols
| Read |
|
Articles:
Distance Vector Routing Protocols
| Read |
| Read | |
|
Articles:
Routed Protocols
| Read |
Suggested Articles:
Network Cabling
Important Direct Cable Connection Notes
This page was designed to provide some notes on Direct Cable Connection (File-transfer) of Win9x/ME/2000 with LAPLINK (Printer port) Cable or Null-...
Ethernet Protocol, CSMA/CD, Collisions
Troubleshooting techniques for Fast Ethernet
This page will primarily discuss problems unique to Fast Ethernet.
The Collision Domain
Incompatible Ethernet Jabber
Auto-negotiation Prioriti...
IP Protocol
IP Protocol - Part 2: The Internet Protocol (IP...
This article examines the Internet Protocol (IP) and its position within the OSI Model. We take a look at the IP Header and all fields contained wi...
Ethernet Protocol, CSMA/CD, Collisions
Early Ethernet Collisions
In this example, we will refer to an imaginary Ethernet network consisting of Stations A and B and any number of other stations. The status of the ...
Featured Subcategories:
Netflow Articles:
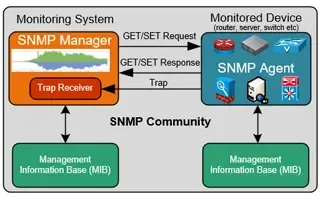
Netflow vs SNMP. Two Different Approaches to Ne...
SNMP (Simple Network Management Protocol) and Netflow are both popular protocols with admins, prized for their ability to give visibility over the ...

Netflow: Monitor Bandwidth & Network Utilizatio...
Monitoring network traffic & bandwidth usage via Netflow is mandatory for any type and size network. Gaining visibility into user traffic, appl...
NetFlow Analyzer: Free Download, Step-by-Step I...
In our previous article we explained how a Netflow Analyzer can help you gain visibility into your user traffic, application traffic and data flows...
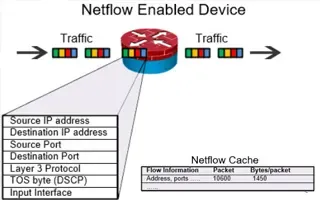
Complete Guide to Netflow: How Netflow & its Co...
This article will cover the basics of Netflow, including its use cases, Netflow supported devices, Netflow history, and variants. We’ll also dive i...
Your IP address:
18.117.151.234
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!

VLAN Networks
VTP Protocol - In-Depth Analysis
The previous article introduced the VTP protocol, we examined how it can be used within a network, to help manage VLANs and ease the administrative over...

VLAN Networks
The VLAN Concept - Introduction to VLANs
We hear about them everywhere, vendors around the world are constantly trying to push them into every type of network and as a result, the Local Area Ne...

VLAN Networks
VLAN Security - Making the Most of VLANs
It's easy to see why virtual LANs have become extremely popular on networks of all sizes. In practical terms, multiple VLANs are pretty much the same as...

VLAN Networks
VTP Pruning
VTP (VLAN Trunking Protocol) pruning is a feature that is used in Cisco switches to reduce unnecessary traffic in VLAN (Virtual Local Area Network) trun...
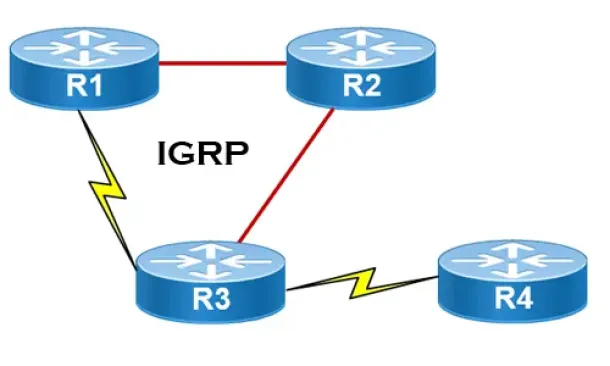
Routing
Interior Gateway Protocol - IGRP
IGRP (Interior Gateway Routing Protocol) is a Cisco proprietary distance-vector routing protocol used in enterprise networks to exchange routing informa...
Routing
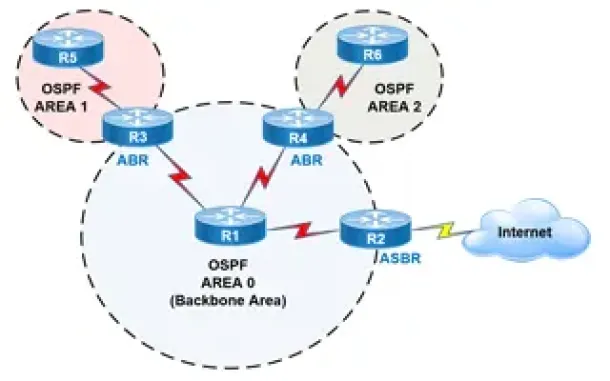
OSPF - Part 2: How OSPF Protocol Works & Basic Conce...
This article covers basic OSPF concepts and operation. We explain how OSPF works, how OSPF tables are built on an OSPF-enabled router and their purpose ...
Routing
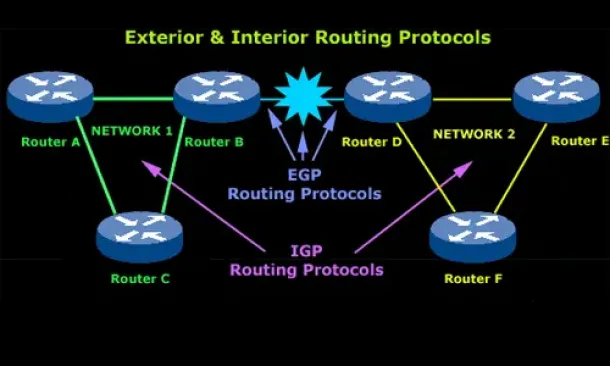
Introduction to Routing Protocols
Distance Vector, Link State RIP, IGRP, EIGRP, OSPF
Routing protocols were created for routers. These protocols have been designed to allow the exchan...
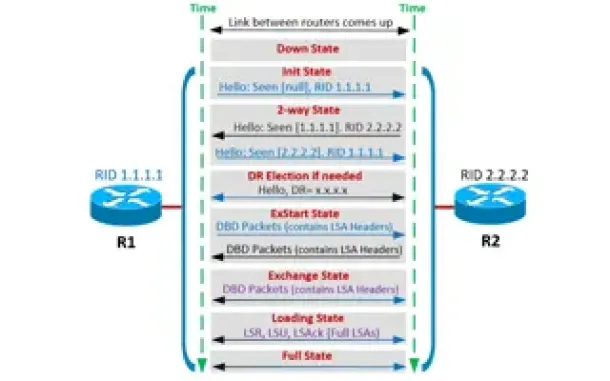
Routing
OSPF - Part 4: OSPF Neighbor States – OSPF Neighbor ...
This is the third article of our OSPF series which analyzes the different OSPF States routers go through during the OSPF discovery and neighbor forming ...
Windows Servers
Windows 2003 DHCP Server Installation & Configuration
DHCP (Dynamic Host Configuration Protocol) is a protocol that allows clients on a network to request network configuration settings from a server runnin...
Network Protocol Analyzers
How to Perform TCP SYN Flood DoS Attack & Detect it ...
This article will help you understand TCP SYN Flood Attacks, show how to perform a SYN Flood Attack (DoS attack) using Kali Linux & hping3 and corre...
Windows Servers
Configuring Windows Server Roaming Profiles
Windows roaming profiles allow the mobile users of a company to always work with their personal settings from any network computer in a domain. Roaming ...
Cisco Wireless
Introduction To Cisco Wireless Controllers (WLC) - B...
The Cisco Wireless Controller (WLC) series devices provide a single solution to configure, manage and support corporate wireless networks, regardless of...


















