The VLAN Concept - Introduction to VLANs
 We hear about them everywhere, vendors around the world are constantly trying to push them into every type of network and as a result, the Local Area Network (LAN) we once knew starts to take a different shape. And yet, for some of us, the concept of what VLANs are and how they work might still be a bit blurry.
We hear about them everywhere, vendors around the world are constantly trying to push them into every type of network and as a result, the Local Area Network (LAN) we once knew starts to take a different shape. And yet, for some of us, the concept of what VLANs are and how they work might still be a bit blurry.
To help start clearing things up we will define the VLAN concept not only through words, but through the use of our cool diagrams and at the same time, compare VLANs to our standard flat switched network.
We will start by taking a quick look at a normal switched network, pointing out it's main characteristics and then move on to VLANs.
The Traditional Switched Network
Almost every network today has a switch interconnecting all network nodes, providing a fast and reliable way for the nodes to communicate. Switches today are what hubs were a while back - the most common and necessary equipment in our network, and there is certainly no doubt about that.
While switches might be adequate for most type of networks, they prove inadequate for mid to large sized networks where things are not as simple as plugging a switch into the power outlet and hanging a few Pc's from it!
For those of you who have already read our "switches and bridges" section, you will be well aware that switches are layer 2 devices which create a flat network:
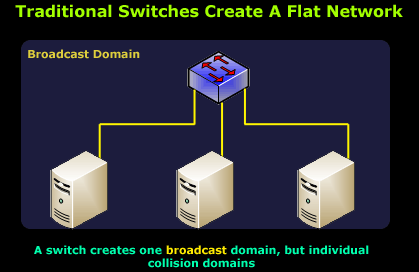
The above network diagram illustrates a switch with 3 workstations connected. These workstations are able to communicate with each other and are part of the same broadcast domain, meaning that if one workstation were to send a broadcast, the rest will receive it.
In a small network multiple broadcast might not be too much of a problem, but as the size of the network increases, so will the broadcasts, up to the point where they start to become a big problem, flooding the network with garbage (most of the times!) and consuming valuable bandwidth.
To visually understand the problem, but also the idea of a large flat network, observe the diagram below:
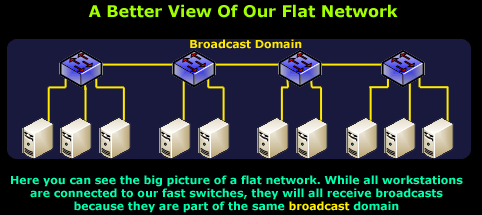
The problem here starts to become evident as we populate the network with more switches and workstations. Since most workstations tend to be loaded with the Windows operating system, this will result in unavoidable broadcasts being sent occasionaly on the network wire - something we certainly want to avoid.
Another major concern is security. In the above network, all users are able to see all devices. In a much larger network containing critical file servers, databases and other confidential information, this would mean that everyone would have network access to these servers and naturally, they would be more susceptible to an attack.
To effectively protect such systems from your network you would need to restrict access at the network level by segmenting the exisiting network or simply placing a firewall in front of each critical system, but the cost and complexity will surely make most administrators think twice about it. Thankfully there is a solution ..... simply keep reading.
Introducing VLANs
Welcome to the wonderful world of VLANs!
All the above problems, and a lot more, can be forgotten with the creation of VLANs...well, to some extent at least.
As most of you are already aware, in order to create (and work with) VLANs, you need a layer 2 switch that supports them. A lot of people new to the networking field bring the misconception that it's a matter of simply installing additional software on the clients or switch, in order to "enable" VLANs throughout the network - this is totally incorrect!
Because VLANs involve millions of mathematical calculations, they require special hardware which is built into the switch and your switch must therefore support VLANs at the time of purchase, otherwise you will not be able to create VLANs on it!
Each VLAN created on a switch is a separate network. This means that a separate broadcast domain is created for each VLAN that exists. Network broadcasts, by default, are filtered from all ports on a switch that are not members of the same VLAN and this is why VLANs are very common in today's large network as they help isolate network segments between each other.
To help create the visual picture on how VLANs differentiate from switches, consider the following diagram:
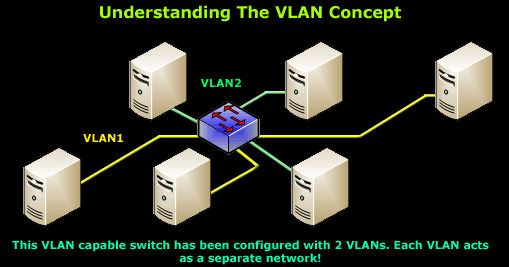
What we have here is a small network with 6 workstations attached to a VLAN capable switch. The switch has been programmed with 2 VLANs, VLAN1 and VLAN2 respectfully, and 3 workstations have been assigned to each VLAN.
VLAN Configuration for Cisco Layer 3 switches is covered at the following article: Basic & Advanced Catalyst Layer 3 Switch Configuration: Creating VLANs, InterVLAN Routing (SVI), VLAN Security – VLAN Hopping, VTP Configuration, Trunk Links, NTP. IOS License Requirements for SVI Routing.
VLANs = Separate Broadcast Domains
With the creation of our VLANs, we have also created 2 broadcast domains. This mean that if any workstation in either VLAN sends a broadcast, it will propagate out the ports which belong to the same VLAN as the workstation that generated the broadcast:
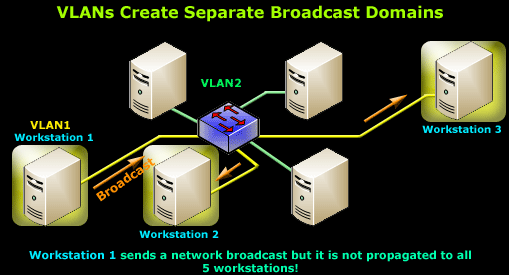
This is clearly illustrated in the diagram above where Workstation 1, belonging to VLAN1, sends a network broadcast (FF:FF:FF:FF:FF:FF). The switch receives this broadcast and forwards it to Workstation 2 and 3, just as it would happen if these three workstations were connected to a normal switch, while the workstations belonging to VLAN2 are totally unaware of the broadcast sent in VLAN1 as they do not receive any packets flowing in that network.
To help clear any questions or doubts on how the above setup works, the diagram below shows the logical equivalent setup of our example network:
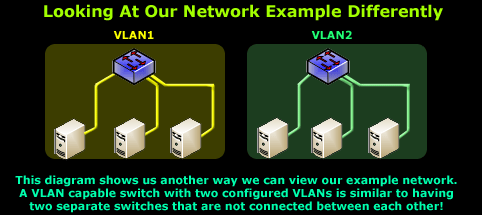
By this stage, you should begin seeing the clear advantages offered by the use of VLANs within your network. Security, cost and network traffic are reduced as more hosts are added to the network and the number of VLANs are increased.
VLANs Help Reduce Networking Costs
To briefly touch upon the financial side of things, let's take an example to see exactly how we are saving money by using VLANs.
Consider you're the network administrator for a large company and you have been asked to split the existing network infrastructure into 12 seperate networks, but without the possibility of these new networks to communicate between each other. Since the cabling is already in place, we need to simply group the ports of each network we create to one physical switch and for the 12 network, a total of 12 switches will be required.
By using VLANs, the above task would be possible with one or more VLAN capable switches that will cover the number of hosts we need to connect to them, and the cost would surely be a lot less than that compared to 12 switches.
During the implementation of the above task, you would connect all workstations to the switch and then assign the appropriate workstations/nodes to their respectful VLAN, creating a total of 12 VLANs. It is worth noting here that most entry level VLAN switches e.g Cisco 2900 series, are capable of handling up to 64 VLANs, so if we were to use these switches, we would still have plently of room to create more.
| Switch Model | Maximum VLANs Supported | VLAN Trunking Supported |
|---|---|---|
| Catalyst 2912 XL, Catalyst 2924 XL & Catalyst 2924C XL |
64
|
yes
|
| Catalyst 2900 LRE XL |
250
|
yes
|
| Catalyst 2912M and Catalyst 2924M modular |
250
|
yes
|
| Catalyst 3500 XL, 3550, 3560, 3750, 4500, 6500 |
250
|
yes
|
There are a lot more examples one can use to show how these new generation switches are able to solve complex network designs, security issues and at the same time, keep the budget low. Lastly, the best example is one that is able to solve your own requirements, so take a minute to think about it and you will surely agree.
Summary
This page introduced the concept of VLANs and indicated the differences existing between them and normal switched networks. We also briefly examined their efficiency in terms of cost, security and implementation.
The information here serves as an introduction to the VLAN technology and we will now start diving deeper into the topic, analysing it in greater detail. Having said that, our next page deals with the design of VLANs, showing different logical and physical configurations of VLANs within networks. So, make yourself comfortable and let's continue cause there is still so much to cover!
Next - VLANs - Access & Trunk Links or Back to VLAN Networks Section
Your IP address:
3.129.68.127
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!


















