Articles
To read the articles in this section, simply click on the article title or read button on the far right (if visible).
Use the below filters to customise the number of articles displayed or search for specific title topics/keywords.
| Articles | |
|---|---|
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
|
Articles:
UDP Protocol - Header
| Read |
Suggested Articles:
Network Address Translation - NAT
Network Address Translation (NAT) Overload - Pa...
NAT Overload is the most common NAT method used throughout all networks that connect to the Internet. This is because of the way it functions and t...
TCP - UDP Protocol Analysis
TCP Header Anaylsis - Section 6: TCP Options
The TCP Options (MSS, Window Scaling, Selective Acknowledgements, Timestamps, Nop) are located at the end of the TCP Header which is also why they ...
TCP - UDP Protocol Analysis
Transmission Control Protocol - Part 3: The TCP...
This article shows the TCP Header and Segment. We explain where the TCP Header and Segment are located in an Ethernet frame and also briefly view t...
Network Address Translation - NAT
Dynamic NAT - Part 2
Our previous article, Dynamic NAT - Part 1, covered the basic idea of Dynamic Network Address Translation. We are now going to take a closer look a...
Featured Subcategories:
Netflow Articles:
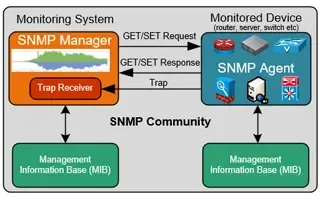
Netflow vs SNMP. Two Different Approaches to Ne...
SNMP (Simple Network Management Protocol) and Netflow are both popular protocols with admins, prized for their ability to give visibility over the ...
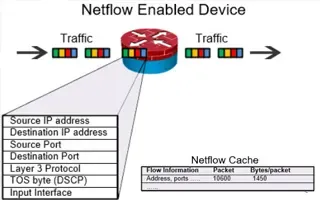
Complete Guide to Netflow: How Netflow & its Co...
This article will cover the basics of Netflow, including its use cases, Netflow supported devices, Netflow history, and variants. We’ll also dive i...

Netflow: Monitor Bandwidth & Network Utilizatio...
Monitoring network traffic & bandwidth usage via Netflow is mandatory for any type and size network. Gaining visibility into user traffic, appl...
NetFlow Analyzer: Free Download, Step-by-Step I...
In our previous article we explained how a Netflow Analyzer can help you gain visibility into your user traffic, application traffic and data flows...
Your IP address:
3.141.29.119
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!

VLAN Networks
InterVLAN Routing - Routing between VLAN Networks
This article deals with the popular topic of InterVLAN routing, which is used to allow routing & communication between VLAN networks. Our article an...

VLAN Networks
Dynamic VLANs
Dynamic VLANs were introduced to grant the flexibility and complexity(!) that Static VLANs did not provide. Dynamic VLANs are quite rare because of thei...

VLAN Networks
VTP Pruning
VTP (VLAN Trunking Protocol) pruning is a feature that is used in Cisco switches to reduce unnecessary traffic in VLAN (Virtual Local Area Network) trun...

VLAN Networks
Comparing Traditional Flat & VLAN Networks
Designing and building a network is not a simple job. VLANs are no exception to this rule, in fact they require a more sophisticated approach because of...
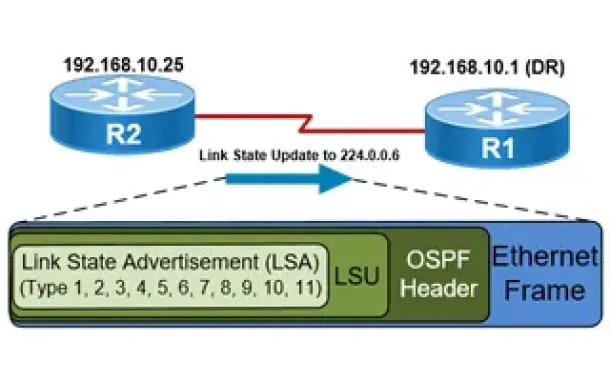
Routing
OSPF - Part 5: Analysis of OSPF Link State Update (L...
This article explains how OSPF uses Link State Advertisement (LSA) to exchange information about the network topology between routers. When a router rec...
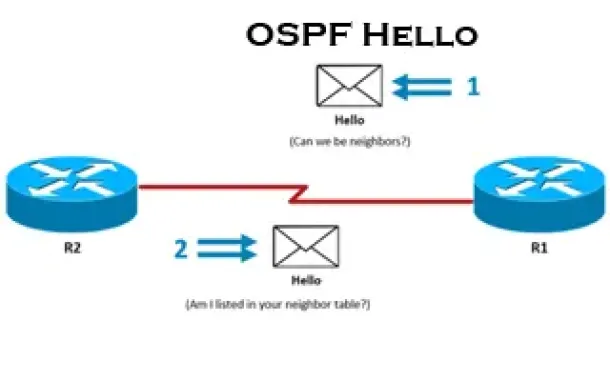
Routing
OSPF - Part 3: OSPF Adjacency & Neighbor Forming Pro...
This is the thrid article of our 6-part OSPF series (see below) that describes how OSPF routers perform neighbor relationship and adjacency. We’ll exami...
Routing
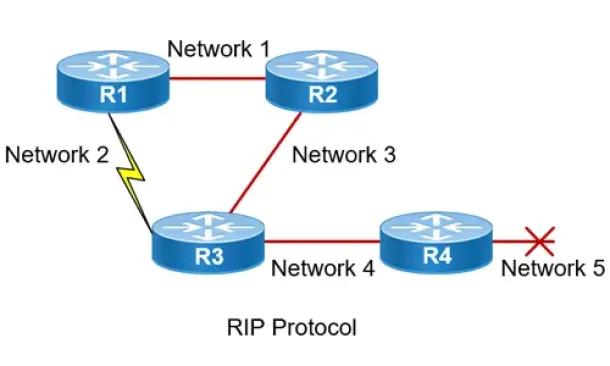
Routing Information Protocol - RIP
Routing Information Protocol (RIP) is a distance-vector routing protocol that is commonly used in small to medium-sized networks. It is one of the...
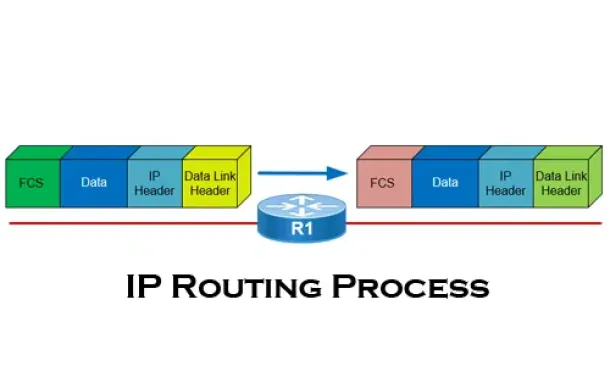
Routing
The IP Routing Process - Step-by-Step Analysis
We are going to analyse what happens when routing occurs on a network (IP routing process). When I was new to the networking area, I thought that all yo...
Windows Servers
Windows 2012 Server Foundation, Essential, Standard ...
FREE Hyper-V & VMware Virtualization Backup: FREE for Firewall.cx readers for a Limited Time! Download Now!
Windows Server 2012 Editio...
Cisco Switches
Cisco Catalyst Err-disabled Port State, Enable & Dis...
Errdisable is a feature that automatically disables a port on a Cisco Catalyst switch. When a port is error disabled, it is effectively shut down a...
SASE & SD-WAN Networks
Key Features of a True Cloud-Native SASE Service. Se...
Secure Access Service Edge (SASE) is an architecture widely regarded as the future of enterprise networking and security. In previous articles we talked...
Windows Servers
How to Enable ‘Web Server’ Certificate Template Opti...
In this article we will show you how to enable the ‘Web Server’ certificate template option on a Windows Certification Authority (Windows CA) Server.&nb...


















