Converting Cisco Firepower from Platform mode to Appliance mode. Full ASA Backup with ASDM
 This article explains how to configure a Cisco Firepower 2100 series device to operate in Appliance mode. We’ll show you how to switch from Platform mode to Appliance mode and how the device will automatically convert and retain your ASA configuration.
This article explains how to configure a Cisco Firepower 2100 series device to operate in Appliance mode. We’ll show you how to switch from Platform mode to Appliance mode and how the device will automatically convert and retain your ASA configuration.
Before performing the conversion, its important to obtain a full backup of the Firepower system and therefore also cover how to backup your Cisco Firepower appliance configuration, certificates, VPN configuration (including pre-shared keys), VPN profiles and more, using the Cisco Adaptive Security Device Manager (ASDM).
Key Topics:
- Cisco Firepower Platform and Appliance Mode
- How to Backup Cisco ASA using ASDM
- Converting Firepower from Platform to Appliance Mode
- Summary
More in-depth technical articles can be found in our Cisco Firewall section.
Cisco Firepower Platform and Appliance Mode
The Cisco Firepower 2100 series operates on an underlying system called FXOS. You can run the Firepower 2100 for ASA in two modes:
- Platform Mode: In this mode, you need to configure basic operating parameters and hardware interface settings within FXOS. This includes tasks like enabling interfaces, setting up EtherChannels, managing NTP, and handling image management. You can use either the chassis manager web interface or the FXOS CLI for these configurations. Afterward, you can set up your security policy in the ASA operating system using ASDM or the ASA CLI.
- Appliance Mode (Default): This mode allows you to configure all settings directly in the ASA. Only advanced troubleshooting commands are available through the FXOS CLI in this mode. Appliance mode is similar to how the old ASA Firewalls (5500 series) ran when the FXOS didn’t exist.
The Management 1/1 interface is used to manage the Firepower device. The interface is configured with two IP addresses, one for the FXOS and one for the ASA. When changing to Appliance mode, the FXOS IP address is lost and will need to be reconfigured, however you can connect to the FXOS directly from the ASA software using the following command:
Configuring session.
.
Connecting to FXOS.
...
Connected to FXOS. Escape character sequence is 'CTRL-^X'.
NOTICE: You have connected to the FXOS CLI with admin privileges.
Config commands and commit-buffer are not supported in appliance mode.
<output omitted>
Firepower2120#
How to Backup Cisco ASA using ASDM
Using ASDM to perform a fully back of the ASA appliance, is the easiest and less painful method. With the help of ASDM you can backup configuration (startup & running configuration), security images, certificates, VPN Pre-shared keys, VPN profiles, SSL VPN configuration and more.
To begin the backup procedure, Launch ASDM and select Tools > Backup Configuration: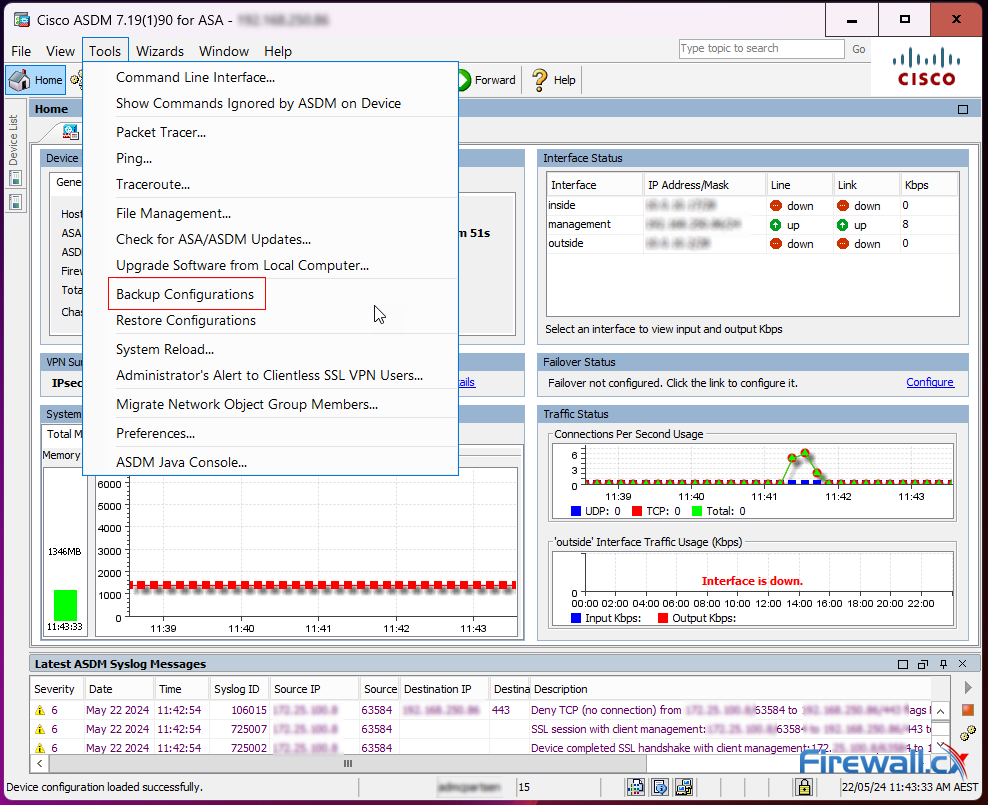
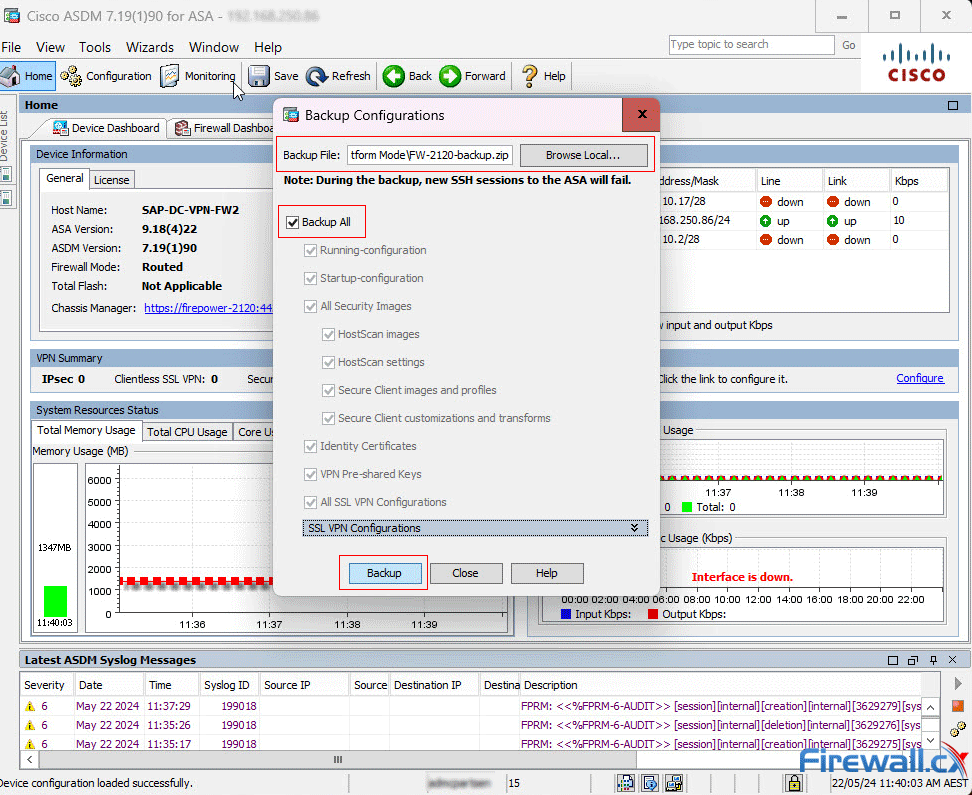
Next, select the backup file name:
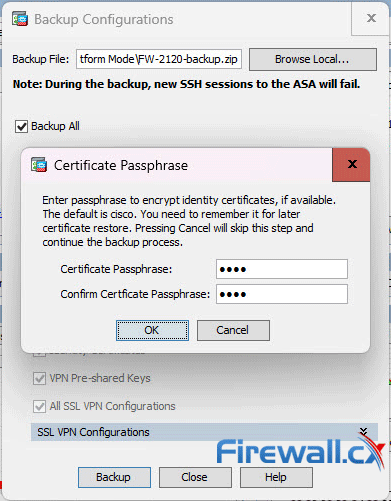
Next, select the passphrase to encrypt identity certificates:
The backup process with then continue and a progress bar provides a visual indication of the procedure’s overall progress:
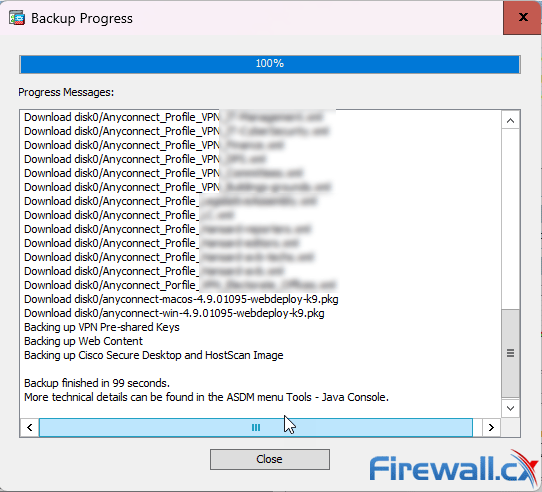
The ASDM backup is now complete and we are ready to proceed with the conversion to Appliance mode.
Converting Firepower from Platform to Appliance Mode
The conversion to Appliance mode is a straight-forward process. First, log into the Cisco ASA Firepower appliance and issue the show fxos mode command to verify the current mode:
Mode is currently set to platform
Next, enter global configuration mode and issue the fxos mode appliance command. This will set the device to appliance mode, however you’ll need to save the running-configuration and reload the device for the changes to take effect:
Firewall.cx-FW1# configure terminal
Firewall.cx-FW1 (config)# fxos mode appliance
Mode set to appliance mode
WARNING: The running-config must be saved and the system must
be rebooted for this command to take effect. Upon reboot, the current
configuration will be erased, and the default configuration for
appliance mode will be applied.
Firewall.cx-FW1(config)# reload
System config has been modified. Save? [Y]es/[N]o: Y
Cryptochecksum: e40316ab e2484b35 7258dfcd 255f6178
81545 bytes copied in 0.940 secs
WARNING: Mode change detected. Upon reboot,
current configuration will be cleared and the default
configuration for appliance mode will be applied.
Proceed with reload? [confirm]
Firewall.cx-FW1(config)#
Firewall.cx-FW1(config)# reload
WARNING: Mode change detected. Upon reboot,
current configuration will be cleared and the default
configuration for appliance mode will be applied.
Proceed with reload? [confirm]
***
*** --- START GRACEFUL SHUTDOWN ---
Shutting down Application Agent
Shutting down isakmp
Shutting down webvpn
Shutting down fover_reload
Shutting down sw-module
Shutting down License Controller
Shutting down File system
***
*** --- SHUTDOWN NOW ---
At this point the firepower appliance will reboot and go into appliance mode. When we executed this process, we noticed that the firewall’s original ASA configuration was retained and a restore was not required. As this feature might depend on the firmware version run by the appliance, its highly recommend you plan for a full restore:
Cisco ASA: CMD=-bootup, CSP-ID=cisco-asa.9.18.4.22__asa_001_JMX2747Y0GDCGJZBI3, FLAG=''
Cisco ASA booting up ...
INFO:-MspCheck: Configuration Xml found is /opt/cisco/csp/applications/configs/cspCfg_cisco-asa.9.18.4.22__asa_001_JMX2747Y0GDCGJZBI3.xml
INFO:-MspCheck: CSPI
firepower-2120 login: admin (automatic login)
Last login: Wed May 22 11:37:28 AEST 2024 on ttyS0
Successful login attempts for user 'admin' : 1
INFO: System Disks /dev/sda is present. Status: Operable. /dev/sdb is present. Status: Inoperable.
Waiting for Application infrastructure to be ready...
Verifying the signature of the Application image...
Please wait for Cisco ASA to come online...1...
<output omitted>
Reading from flash...
!!!!!!!!!!!!!!!!...........WARNING: interface Ethernet1/6 security level is 99.
*** Output from config line 447, "logging host inside 172...."
............................
Cryptochecksum (unchanged): e40316ab e2484b35 7258dfcd 255f6178
INFO: File /mnt/disk0/.private/dynamic-config.json not opened; errno 2
INFO: Network Service reload not performed.
INFO: Power-On Self-Test in process.
......................................
INFO: Power-On Self-Test complete.
INFO: Starting SW-DRBG health test...
INFO: SW-DRBG health test passed.
<output omitted>
User enable_1 logged in to Firewall.cx-FW1
Logins over the last 1 days: 1.
Failed logins since the last login: 0.
Attaching to ASA CLI ... Press 'Ctrl+a then d' to detach.
Type help or '?' for a list of available commands.
Firewall.cx-FW1> en
Username: admin
Password: *******
Firewall.cx-FW1# sh run
: Saved
:
: Serial Number: JAD22159EL1
: Hardware: FPR-2120, 6589 MB RAM, CPU MIPS 1200 MHz, 1 CPU (8 cores)
:
ASA Version 9.18(4)22
!
hostname Firewall.cx-FW1
domain-name firewall.cx
<output omitted>
Summary
In this article we showed how to configure/convert a Cisco Firepower 2100 series appliance from Platform mode to Appliance mode. We also explained how to create a full backup of the ASA configuration, including images, certificates, VPN Pre-shared keys, VPN profiles, SSL VPN configuration and more, with the help of Cisco’s ASDM application.
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!














