The Importance of Monitoring and Controlling Web Traffic in Enterprise & SMB Networks - Protecting from Malicious Websites - Part 1
 This article expands on our popular security articles (Part 1 & Part 2) that covered the importance of patching enterprise and SMB network systems to protect them from hijacking, hacking attempts, unauthorized access to sensitive data and more. While patching systems is essential, another equally important step is the monitoring of Web traffic to control user activity on the web and prevent users from accessing dangerous sites and Internet resources that could jeopardize the company’s security.
This article expands on our popular security articles (Part 1 & Part 2) that covered the importance of patching enterprise and SMB network systems to protect them from hijacking, hacking attempts, unauthorized access to sensitive data and more. While patching systems is essential, another equally important step is the monitoring of Web traffic to control user activity on the web and prevent users from accessing dangerous sites and Internet resources that could jeopardize the company’s security.
The ancient maxim – prevention is better than cure – holds good in cyberspace as well, and it is prudent to detect beforehand signs of trouble, which if allowed to continue, might snowball into something uncontrollable. One of the best means of such prevention is through monitoring web traffic and to locate potential sources of trouble.
Even if attackers are unable to gain access to your network, they can still hold you to ransom by launching a Distributed Denial of Service or DDoS attack, wherein they choke the bandwidth of your network. Regular customers will not be able to gain access to your servers. Generally downtime for any company these days translates to loss of income and damage to the company’s reputation. Attackers these days might also refuse to relent until a ransom amount is paid up. Sounds a bit too far-fetched? Not really.
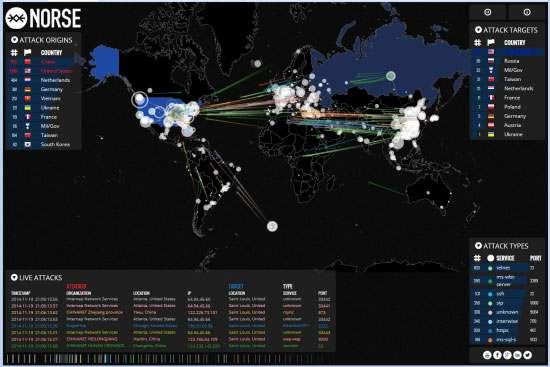
Live Attacks & Hacking Attempts On The Internet
It’s hard to image what really is happening right now on the Internet: How many attacks are taking place, the magnitude of these attacks, the services used to launch attacks, attack origins, attack targets and much more. Hopefully we’ll be able to help change than for you right now…
The screenshot below was taken after monitoring the Norse network which collects and analyzes live threat intelligence from darknets in hundreds of locations in over 40 countries. The attacks are taken from a small subset of live flows against the Norse honeypot infrastructure and represent actual worldwide cyber-attacks:
In around 15 minutes of monitoring attacks, we saw more than 5000 different origins launching attacks to over 5800 targets, of which 99% of the targets are located in the United States and 50% of the attack origins were from China.
The sad truth is that the majority of these attacks are initiated from compromised computer systems & servers, with unrestricted web access. All it takes today is for one system to visit an infected site and that could be enough to bring down the whole enterprise network infrastructure while at the same time launch a massive attack against Internet targets.
 In June 2014, Evernote and Feedly, working largely in tandem, went down with a DDoS attack within two days of each other. Evernote recovered the same day, but Feedly had to suffer more. Although there were two more DDoS attacks on Feedly that caused it to lose business for another two days, normalcy was finally restored. According to the CEO of Feedly, they refused to give in to the demands of ransom in exchange for ending the attack and were successful in neutralizing the threat.
In June 2014, Evernote and Feedly, working largely in tandem, went down with a DDoS attack within two days of each other. Evernote recovered the same day, but Feedly had to suffer more. Although there were two more DDoS attacks on Feedly that caused it to lose business for another two days, normalcy was finally restored. According to the CEO of Feedly, they refused to give in to the demands of ransom in exchange for ending the attack and were successful in neutralizing the threat.
 Domino's Pizza had over 600,000 Belgian and French customer records stolen by the hacking group Rex Mundi. The attackers demanded $40,000 from the fast food chain in exchange for not publishing the data online. It is not clear whether Domino's complied with the ransom demands. However, they reassured their customers that although the attackers did have their names, addresses and phone numbers, they however, were unsuccessful in stealing their financial and banking information. The Twitter account of the hacking group was suspended, and they never released the information.
Domino's Pizza had over 600,000 Belgian and French customer records stolen by the hacking group Rex Mundi. The attackers demanded $40,000 from the fast food chain in exchange for not publishing the data online. It is not clear whether Domino's complied with the ransom demands. However, they reassured their customers that although the attackers did have their names, addresses and phone numbers, they however, were unsuccessful in stealing their financial and banking information. The Twitter account of the hacking group was suspended, and they never released the information.
Apart from external attacks, misbehavior from employees can cause equal if not greater damage. Employees viewing pornographic material in the workspace can lead to a huge number of issues. Not only is porn one of the biggest time wasters, it chokes up the network bandwidth with non-productive downloads, including bringing in unwanted virus, malware and Trojans. Co-workers unwillingly exposed to offensive images can find the workplace uncomfortable and this may further lead to charges of sexual harassment, dismissal and lawsuits, all expensive and disruptive.
Another major problem is data leakage via e-mail or webmail – intended or by accident. Client data, unreleased financial data and confidential plans leaked through emails may cause devastating impact to the business including loss of client confidence.
Web monitoring provides answers to several of these problems. This type of monitoring need not be very intrusive or onerous, but with the right policies and training, employees easily learn to differentiate between appropriate and inappropriate use.
Few Of The Biggest Web Problems
To monitor the web, you must know the issues that you need to focus on. Although organizations differ in their values, policies and culture, there are some common major issues on the Web that cause the biggest headaches:
- Torrents And Peer-To-Peer Networks offer free software, chat, music and video, which can be easily downloaded. However, this can hog the bandwidth causing disruptions in operation such as for video conferencing and VoIP. Moreover, such sites also contain pirated software, bootlegged movies and inappropriate content that are mostly tainted with various types of virus and Trojans.
- Gaming sites are notorious for hogging bandwidth and wasting productive time. Employees often find these sites hard to resist and download games. Most of the games carry lethal payloads of virus and other malware, with hackers finding them a common way for SEO poisoning. Even when safe, games disrupt productivity and clog the network.
- Fun sites, although providing a harmless means of relieving stress, may be offensive and inappropriate to coworkers. Whether your policies allow such humor sites, they can contain SEO poisoned links and Trojans, often clogging networks with their video components.
- Online Shopping may relate to purchase of work-appropriate items as well as personal. Although the actual purchase may not take up much time, surfing for the right product is a huge time waster, especially for personal items. Individual policies may either limit the access to certain hours of the day or block these sites altogether.
- Non-Productive Surfing can be a huge productivity killer for any organization. Employees may be obsessed with tracking shares, sports news or deals on commercial sites such as Craigslist and eBay. Company policies can block access to such sites entirely, or limit the time spent on such sites to only during lunchtime.
According to a survey involving over 3,000 employees, Salary.com found over 60% involved in visiting sites unrelated to their work every day. More than 20% spent above five hours a week on non-work related sites. Nearly half of those surveyed looked for a new job using office computers in their work time.
In the next part of our article, we will examine the importance of placing a company security policy to help avoid users visiting sites they shouldn't, stop waisting valuable time and resources on activities that can compromise the enterprise's network security and more. We also take an in-depth look on how to effectively monitor and control traffic activity on the Web in real-time, plus much more.
Your IP address:
18.221.236.28
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!