How to Protect Your Business with Microsoft 365 Security Tools
 Businesses of all sizes are more and more adopting cloud-based platforms like Microsoft 365 to streamline operations, improve collaboration, and increase productivity. However, this newfound reliance on such software solutions makes these businesses prime targets for cybercriminals.
Businesses of all sizes are more and more adopting cloud-based platforms like Microsoft 365 to streamline operations, improve collaboration, and increase productivity. However, this newfound reliance on such software solutions makes these businesses prime targets for cybercriminals.
With sensitive data stored and shared across the suite, securing your Microsoft 365 environment is essential to protect your business from potential threats.
Fortunately, Microsoft 365 comes with a robust set of built-in security tools designed to safeguard your organization from cyberattacks, data breaches, and other security incidents.
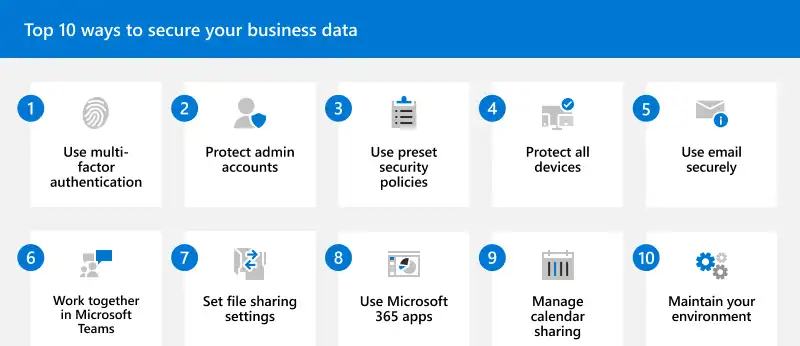
But despite that, we cannot ignore the importance of third-party Microsoft 365 total protection solutions. Without going too much into detail, these solutions enhance the already powerful native security features. But what are these features?
In this article, we’ll explore the key Microsoft 365 security tools you can use to protect your business.
Key Topics:
- Key Microsoft 365 Security Tools
- Best Practices for Leveraging Microsoft 365 Security Tools
- Conclusion
Related Articles:
- Boost Your Microsoft 365 Security with Expert Guidance and Proven Best Practices
- Empowering Users with Cyber Security Awareness Training
Key Microsoft 365 Security Tools to Protect Your Business
Microsoft Defender for Office 365
 One of the most critical security solutions within the Microsoft 365 ecosystem is Microsoft Defender for Office 365. This tool is specifically designed to protect against email-based threats such as phishing, malware, and ransomware, which are common attack vectors targeting businesses.
One of the most critical security solutions within the Microsoft 365 ecosystem is Microsoft Defender for Office 365. This tool is specifically designed to protect against email-based threats such as phishing, malware, and ransomware, which are common attack vectors targeting businesses.
Defender for Office 365 leverages real-time threat intelligence to detect and block malicious activity before it reaches your users.
Key features include:
- Safe Links: Scans and rewrites URLs in emails and documents to prevent users from clicking on malicious links.
- Safe Attachments: Blocks harmful attachments by scanning and analyzing them in real time.
- Anti-phishing: Identifies and neutralizes phishing attempts by analyzing email content and sender behavior.
By configuring these features, businesses can significantly reduce the risk of falling victim to email-based attacks, which remain one of the most common cybersecurity threats today.
Multi-Factor Authentication (MFA)
 One of the most effective ways to prevent unauthorized access to your Microsoft 365 accounts is by implementing Multi-Factor Authentication (MFA). MFA adds an extra layer of security by requiring users to verify their identity through two or more authentication methods, such as a password and a one-time code sent to their mobile device.
One of the most effective ways to prevent unauthorized access to your Microsoft 365 accounts is by implementing Multi-Factor Authentication (MFA). MFA adds an extra layer of security by requiring users to verify their identity through two or more authentication methods, such as a password and a one-time code sent to their mobile device.
Why MFA is critical:
- Even if an attacker steals a user’s password, they won’t be able to access the account without the second form of verification.
- MFA drastically reduces the risk of account compromise, especially in the case of phishing or brute-force attacks.
Steps to implement MFA in Microsoft 365:
- Enable MFA for all admin and high-privilege accounts.
- Encourage all users to enable MFA, ideally using an authenticator app instead of SMS for added security.
Conditional Access
Microsoft 365’s Conditional Access policies provide a flexible way to control who can access your organization’s data based on specific conditions, such as user location, device, and risk level. This dynamic approach ensures that only trusted users and devices can access sensitive business resources.
Best practices for Conditional Access:
- Implement policies to block access from untrusted or unknown locations.
- Use conditional access to enforce Multi-Factor Authentication for high-risk sign-ins.
- Restrict access to corporate data on non-compliant or jailbroken devices.
These policies allow businesses to protect their data without hindering productivity, ensuring that users can access the tools they need securely.
Azure Information Protection (AIP)
 Azure Information Protection (AIP) is a powerful tool that helps classify, label, and protect sensitive data based on its confidentiality level. By tagging documents and emails with labels such as "Confidential" or "Internal Use Only", businesses can control how sensitive data is handled and shared.
Azure Information Protection (AIP) is a powerful tool that helps classify, label, and protect sensitive data based on its confidentiality level. By tagging documents and emails with labels such as "Confidential" or "Internal Use Only", businesses can control how sensitive data is handled and shared.
How AIP helps:
- Automatically encrypts and restricts access to sensitive files.
- Allows administrators to track document access and revoke permissions if necessary.
- Works seamlessly with Microsoft 365 to enforce consistent data protection policies.
By integrating AIP with your Microsoft 365 environment, you can ensure that sensitive information is protected at all times, whether it’s being shared internally or externally.
Data Loss Prevention (DLP)
 Data Loss Prevention (DLP) is another essential tool for protecting sensitive business data in Microsoft 365. DLP policies monitor and prevent the unauthorized sharing of sensitive information, such as credit card numbers, personally identifiable information (PII), or intellectual property.
Data Loss Prevention (DLP) is another essential tool for protecting sensitive business data in Microsoft 365. DLP policies monitor and prevent the unauthorized sharing of sensitive information, such as credit card numbers, personally identifiable information (PII), or intellectual property.
Key DLP features:
- Monitor and block sensitive data from being shared via email, OneDrive, SharePoint, or Teams.
- Set up alerts for administrators when DLP policies are triggered.
- Customize DLP policies to fit regulatory requirements or specific business needs.
By implementing DLP, businesses can reduce the risk of accidental data leaks and ensure that sensitive information stays within the organization.
Microsoft 365 Security and Compliance Center
The Microsoft 365 Security and Compliance Center serves as a centralized platform for managing your organization’s security settings and monitoring potential threats. It offers a comprehensive dashboard where administrators can track suspicious activity, manage alerts, and enforce compliance policies.
Key features:
- Threat management: Monitor and respond to potential threats in real time.
- Compliance management: Ensure that your organization adheres to industry regulations and data protection laws.
- Audit logs: Track changes made to security configurations and user activity across your Microsoft 365 environment.
Using the Security and Compliance Center, businesses can maintain a high level of visibility into their security posture and ensure that potential threats are addressed quickly.
Mobile Device Management (MDM)
In today’s mobile-first world, employees often access business data on their smartphones and tablets. Mobile Device Management (MDM) within Microsoft 365 allows businesses to secure mobile access and enforce policies that protect corporate data on personal or company-issued devices.
MDM capabilities include:
- Enforcing encryption and password policies on all mobile devices accessing company data.
- Remotely wiping data from lost or stolen devices.
- Restricting access to corporate resources based on device compliance and security settings.
By implementing MDM, businesses can safeguard sensitive information and ensure that only secure devices are used to access Microsoft 365 resources.
Best Practices for Leveraging Microsoft 365 Security Tools
Regular Audits and Monitoring
While Microsoft 365’s built-in security tools provide robust protection, regular audits and monitoring are essential to ensure that your environment remains secure. By conducting security reviews, you can detect vulnerabilities, identify suspicious activity, and ensure that security policies are being enforced effectively.
Key actions:
- Set up automated alerts for potential security incidents, such as unauthorized access attempts or unusual login activity.
- Regularly review audit logs to track changes to security settings and monitor user behavior.
Employee Training on Security Awareness
Even with advanced security tools in place, employees play a key role in protecting your business. Security awareness training helps employees recognize and avoid common threats such as phishing, malware, and social engineering attacks.
Best practices for training:
- Conduct regular phishing simulations to test employees’ ability to recognize suspicious emails.
- Educate staff on the importance of strong passwords, MFA, and safe browsing habits.
- Provide ongoing training to keep employees informed about the latest cybersecurity threats and best practices.
By fostering a culture of security awareness, businesses can significantly reduce the risk of human error leading to security breaches.
Conclusion
Protecting your business with Microsoft 365 security tools is crucial in today’s threat landscape. With these features and tools, you can significantly reduce the risk of cyberattacks and data breaches. Regularly auditing your security settings and providing employees with security awareness training will further bolster your defenses.
With a proactive approach to security, businesses can fully embrace the benefits of Microsoft 365 while keeping their sensitive data safe and secure.
Your IP address:
3.19.75.187
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!















