Understanding, Creating, Configuring & Applying Windows Server 2012 Active Directory Group Policies
This article explains what Group Policies are and shows how to configure Windows Server 2012 Active Directory Group Policies. Our next article will cover how to properly enforce Group Policies (Group Policy Link Enforcement, Inheritance and Block Inheritance) on computers and users that a part of the company's Active Directory.
FREE Hyper-V & VMware Backup: Easy to use - Powerful features - Just works, no hassle: It's FREE for Firewall.cx readers! Download Now!
Before we dive into Group Policy configuration, let's explain what exactly Group Policies are and how they can help an administrator control its users and computers.
A Group Policy is a computer or user setting that can be configured by administrators to apply various computer specific or user specific registry settings to computers that have joined the domain (active directory). A simple example of a group policy is the user password expiration policy which forces users to change their password on a regular basis. Another example of a group policy would be the enforcement of a specific desktop background picture on every workstation or restricting users from accessing their Local Network Connection properties so they cannot change their IP address.
A Group Policy Object (GPO) contains one or more group policy settings that can be applied to domain computers, users, or both. GPO objects are stored in active directory. You can open and configure GPO objects by using the GPMC (Group Policy Management Console) in Windows Server 2012:
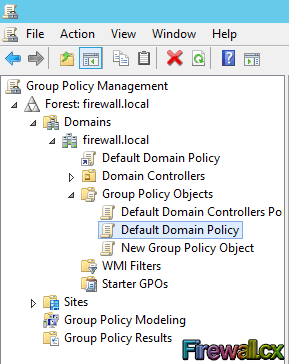 Figure 1. GPO Objects
Figure 1. GPO Objects
Group Policy Settings are the actual configuration settings that can be applied to a domain computer or user. Most of the settings have three states, Enabled, Disabled and Not Configured. Group Policy Management Editor provides access to hundreds of computer and user settings that can be applied to make many system changes to the desktop and server environment.
Group Policy Settings
Group Policy Settings are divided into Computer Settings and User Settings. Computer Settings are applied to computer when the system starts and this modifies the HKEY Local Machine hive of registry. User Settings are applied when the users log in to the computer and this modifies the HKEY Local Machine hive.
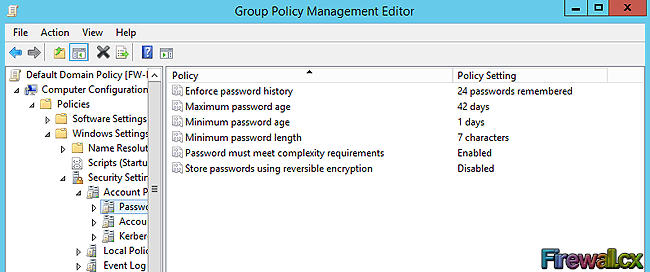 Figure 2. Group Policy Settings
Figure 2. Group Policy Settings
Computer Settings and User Settings both have policies and preferences.
These policies are:
Software Settings: Software can be deployed to users or computer by the administrator. The software deployed to users will be available only to those specific users whereas software deployed to a computer will be available to any user that on the specific computer where the GPO is applied.
Windows Settings: Windows settings can be applied to a user or a computer in order to modify the windows environment. Examples are: password policies, firewall policy, account lockout policy, scripts and so on.
Administrative Templates: Contains a number of user and computer settings that can be applied to control the windows environment of users or computers. For example, specifying the desktop wallpaper, disabling access to non-essential areas of the computers (e.g Network desktop icon, control panel etc), folder redirection and many more.
Preferences are a group policy extension that does the work which would otherwise require scripts. Preferences are used for both users and computers. You can use preferences to map network drives for users, map printers, configure internet options and more.
Next, let’s take a look at how we can create and apply a Group Policy.
FREE Hyper-V & VMware Backup: Easy to use - Powerful features - Just works, no hassle: It's FREE for Firewall.cx readers! Download Now!
Creating & Applying Group Policy Objects
By default, GPOs can be created and applied by Domain Admins, Enterprise Admins and Group Policy Creator Owner user groups. After creating the GPO, you can apply or link the GPOs to sites, domains or Organizational Units (OUs), however you cannot apply GPO to users, groups, or computers. GPOs are processed in following top to bottom order:
- Local Group Policy: Every windows operating system has local group policy installed by default. So this local group policy of the computer is applied at first.
- Site GPO: The GPOs linked to the Site is then processed. By default, there is no site level group policy configured.
- Domain GPO: Next, the GPO configured at domain level is processed. By default, GPO named default domain policy is applied at the domain level. This applies to all the objects of the domain. If there is policy conflict between domain and site level GPOs, then GPO applied to domain level takes the precedence.
- Organizational Unit GPO: - In the end, GPO configured at OU is applied. If there is any conflict between previously applied GPOs, the GPO applied to OU takes the most precedence over Domain, Site and Local Group Policy.
Let’s now take a look at a scenario to apply a group policy to domain joined computers to change the desktop background. We have a domain controller named FW-DC01 and two clients FW-CL1 and FW-CL2 as shown in the diagram below. The goal here is to set the desktop wallpaper for these two clients from a group policy:
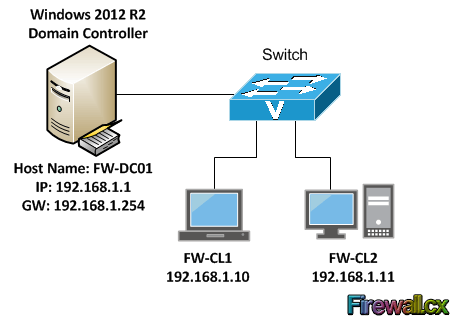 Figure 3. GPO Scenario
Figure 3. GPO Scenario
In our earlier articles we showed how Windows 8 / Windows 8.1 join an Active Directory domain, FW-CL1 and FW-CL2 are workstations that have previously joined our domain – Active Directory. We have two users MJackson and PWall in the FW Users OU.
Open the Group Policy Management Console (GPMC) by going into Server Manager>Tools and select Group Policy Management as shown below:
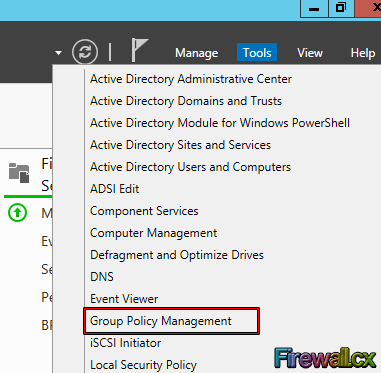 Figure 4. Open GPMC
Figure 4. Open GPMC
As the GPMC opens up, you will see the tree hierarchy of the domain. Now expand the domain, firewall.local in our case, and you will see the FW Users OU which is where our users reside. From here, right-click this OU and select the first option Create a GPO in this domain and Link it here:
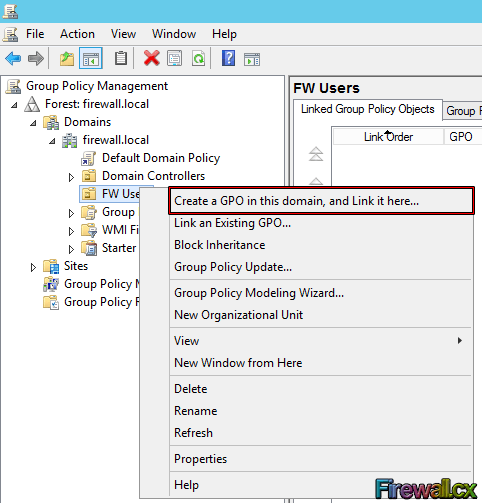 Figure 5. Select FW Users and Create a GPO
Figure 5. Select FW Users and Create a GPO
Now type the Name for this GPO object and click the OK button. We selected WallPaper GPO:
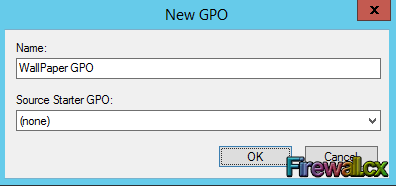 Figure 6. Creating our Wallpaper Group Policy Object
Figure 6. Creating our Wallpaper Group Policy Object
Next, right-click the GPO object and click edit:
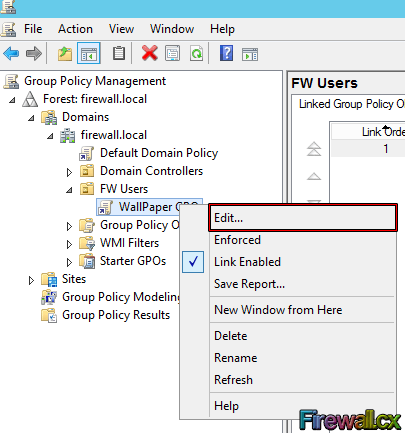 Figure 7. Editing a Group Policy Object
Figure 7. Editing a Group Policy Object
At this point we get to see and configure the policy that deals with the Desktop Wallpaper, however notice the number of different policies that allow us to configure and tweak various aspects of our domain users.
To find the Desktop Wallpaper, go to Expand User Configuration> Policies> Administrative Templates> Desktop> Desktop. At this point we should be able to see the setting in right window. Right-click the Desktop Wallpaper setting and select Edit:
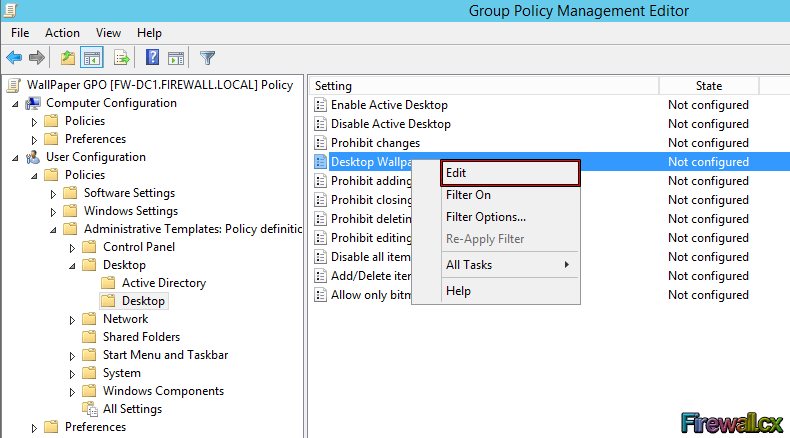 Figure 8. Selecting and editing Desktop Wallpaper policy
Figure 8. Selecting and editing Desktop Wallpaper policy
The settings of Desktop Wallpaper will now open. First we need to activate the policy by selecting the Enabled option on the left. Next, type the UNC path of shared wallpaper. Remember that we must share the folder that contains the wallpaper \\FW-DC1\WallPaper\ and configure the share permission so that users can access it. Notice that we can even select to center our wallpaper (Wallpaper Style). When ready click Apply and then OK:
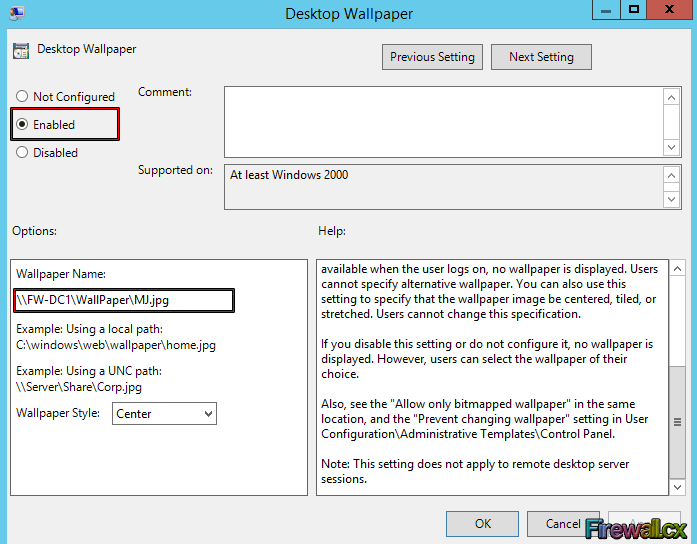 Figure 9. Configure Desktop Wallpaper
Figure 9. Configure Desktop Wallpaper
Now that we’ve configured our GPO, we need to apply it. To do so, we can simply log off and log back in the client computer or type following command in domain controller’s command prompt to apply the settings immediately:
Once our domain user logs in to their computer (FW-CL1), the new wallpaper policy will be applied and loaded on to the computer’s desktop.
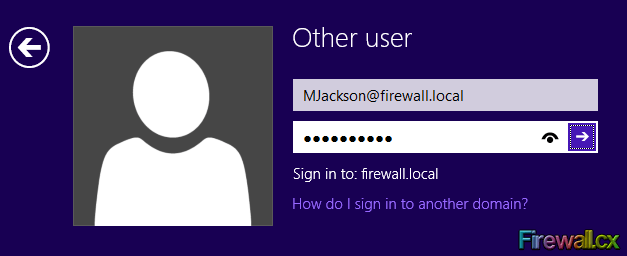 Figure 10. User Login
Figure 10. User Login
As we can see below, our user's desktop now has the background image configured in the group policy we created:
 Figure 11. Computer Desktop Wallpaper Changed
Figure 11. Computer Desktop Wallpaper Changed
This example shows how one small configuration setting can be applied to all computers inside an organization. The power and flexibility of Group Policy Objects is truly unbelievable and as we’ve shown, it’s even easier to configure and apply them with just a few clicks on the domain controller!
FREE Hyper-V & VMware Backup: Easy to use - Powerful features - Just works, no hassle: It's FREE for Firewall.cx readers! Download Now!
This article explained what Group Policies Objects are and showed how to Configure Windows 2012 Active Directory Group Policies to control our Active Directory users and computers. We also highly recommend our article on Group Policy Enforcement, Inheritance throughout the Active Directory structure. More articles on Windows 2012 & Hyper-V can be found at our Windows 2012 Server section.
Your IP address:
18.225.195.162
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!













