- Posts: 3
- Thank you received: 0
ASA 5505 VLAN Routing...
to VLAN2(outside).
I have a smartnet agreement but the folks at Cisco can't seem to figure out what is going on.
note: the ip address to my outside connection was modified for safety reasons
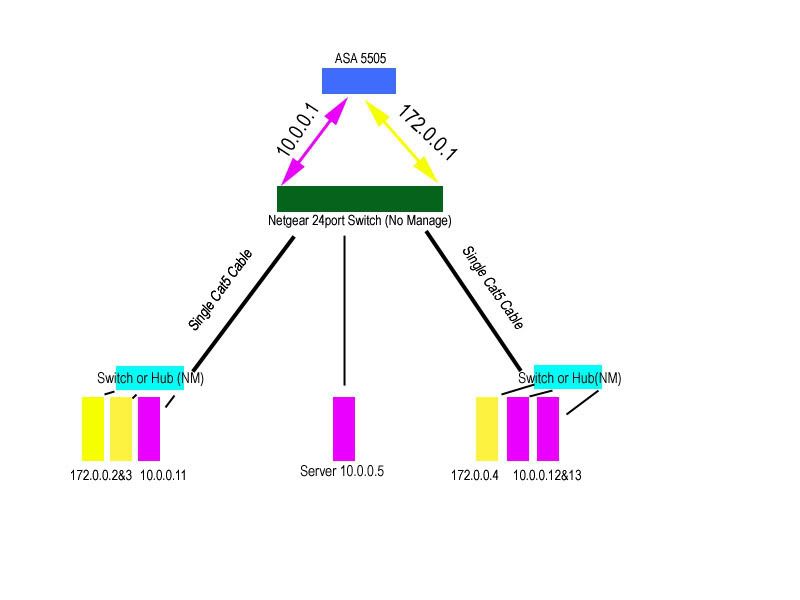
Here's how my network is laid out right now
internet
|
ASA 5505
|
Netgear 24port Switch (NOT MANAGED)
|
workstations
When currently everything works until I hook up Eth0/2 (VLAN3) to the netgear switch (where VLAN1 also connects). It causes my inside network to collapse and nothing works.. causing my users to lose connectivity to the MSSQL database.
Here is my show run
[code:1]
Result of the command: "sh run"
: Saved
:
ASA Version 8.0(3)5
!
hostname ciscoasa
domain-name domain.local
enable password d7N4t5BlrAyLd8cs encrypted
names
!
interface Vlan1
nameif inside
security-level 100
ip address 10.0.0.1 255.255.255.0
!
interface Vlan2
nameif outside
security-level 0
ip address 74.x.x.x 255.255.255.248
!
interface Vlan3
no forward interface Vlan2
nameif dmz
security-level 50
ip address 172.16.0.1 255.255.0.0
!
interface Ethernet0/0
switchport access vlan 2
!
interface Ethernet0/1
!
interface Ethernet0/2
switchport access vlan 3
!
interface Ethernet0/3
!
interface Ethernet0/4
!
interface Ethernet0/5
!
interface Ethernet0/6
!
interface Ethernet0/7
!
passwd d7N4t5BlrAyLd8cs encrypted
boot system disk0:/asa803-5-k8.bin
ftp mode passive
clock timezone CST -6
clock summer-time CDT recurring
dns domain-lookup inside
dns server-group DefaultDNS
name-server 10.0.0.5
domain-name domain.local
access-list VPN_splitTunnelAcl standard permit 10.0.0.0 255.255.255.0
access-list inside_nat0_outbound extended permit ip any 192.168.100.0 255.255.255.240
access-list inside_access_in extended permit ip any any
access-list inbound extended permit tcp any 74.x.x.x 255.255.255.248 eq https
access-list inbound extended permit tcp any 74.x.x.x 255.255.255.248 eq 444
access-list inbound extended permit tcp any 74.x.x.x 255.255.255.248 eq 4125
access-list inbound extended permit tcp 66.18.18.0 255.255.254.0 74.x.x.x 255.255.255.248 eq smtp
access-list inbound extended permit tcp any 74.x.x.x 255.255.255.248 eq www inactive
access-list inbound extended permit icmp any 74.x.x.x 255.255.255.248 echo-reply
access-list dmz_inside extended permit ip any any
pager lines 24
logging enable
logging timestamp
mtu inside 1500
mtu outside 1500
mtu dmz 1500
ip local pool vpn_pool 192.168.100.1-192.168.100.10 mask 255.255.255.0
icmp unreachable rate-limit 1 burst-size 1
icmp deny any outside
asdm image disk0:/asdm-611.bin
no asdm history enable
arp timeout 14400
global (outside) 1 interface
nat (inside) 0 access-list inside_nat0_outbound
nat (inside) 1 0.0.0.0 0.0.0.0
static (inside,outside) tcp interface https 10.0.0.5 https netmask 255.255.255.255
static (inside,outside) tcp interface smtp 10.0.0.5 smtp netmask 255.255.255.255
static (inside,outside) tcp interface 444 10.0.0.5 444 netmask 255.255.255.255
static (inside,outside) tcp interface 4125 10.0.0.5 4125 netmask 255.255.255.255
static (inside,outside) tcp interface www 10.0.0.5 www netmask 255.255.255.255
static (inside,dmz) 10.0.0.0 10.0.0.0 netmask 255.255.255.0
access-group inbound in interface outside
access-group dmz_inside in interface dmz
route outside 0.0.0.0 0.0.0.0 74.x.x.x 1
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
dynamic-access-policy-record DfltAccessPolicy
http server enable
http 0.0.0.0 0.0.0.0 inside
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart
crypto ipsec transform-set ESP-3DES-SHA esp-3des esp-sha-hmac
crypto dynamic-map outside_dyn_map 20 set pfs
crypto dynamic-map outside_dyn_map 20 set transform-set ESP-3DES-SHA
crypto isakmp policy 10
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 86400
crypto isakmp nat-traversal 30
no vpn-addr-assign aaa
no vpn-addr-assign dhcp
vpn-addr-assign local reuse-delay 5
telnet 10.0.0.0 255.255.255.0 inside
telnet timeout 5
ssh 0.0.0.0 0.0.0.0 inside
ssh timeout 60
console timeout 5
management-access inside
threat-detection basic-threat
threat-detection scanning-threat shun except ip-address 10.0.0.0 255.255.255.0
no threat-detection statistics access-list
webvpn
csd image disk0:/securedesktop-asa-3.2.1.118-k9.pkg
svc image disk0:/sslclient-win-1.1.4.177.pkg 1 regex "Windows NT"
group-policy DfltGrpPolicy attributes
vpn-tunnel-protocol IPSec l2tp-ipsec
group-policy VPN internal
group-policy VPN attributes
banner none
wins-server value 10.0.0.5
dns-server value 10.0.0.5
vpn-idle-timeout 15
vpn-tunnel-protocol IPSec
split-tunnel-policy tunnelspecified
split-tunnel-network-list value VPN_splitTunnelAcl
default-domain value domain.local
username dupont password OjS8FBaCgk.begt2 encrypted
username dupont attributes
vpn-group-policy VPN
service-type remote-access
username dluu password DyFC5OurFNi0sR/M encrypted
username dluu attributes
vpn-group-policy VPN
service-type remote-access
username Sherri password /HO7xE8y7KG65PnQ encrypted
username Sherri attributes
vpn-group-policy VPN
service-type remote-access
username Ryan password A9xIwcNgAeJ9htI1 encrypted
username Ryan attributes
vpn-group-policy VPN
tunnel-group VPN type remote-access
tunnel-group VPN general-attributes
address-pool vpn_pool
default-group-policy VPN
password-management
tunnel-group VPN ipsec-attributes
pre-shared-key *
isakmp keepalive threshold 120 retry 2
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum 512
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect sqlnet
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
inspect skinny
!
service-policy global_policy global
prompt hostname context
Cryptochecksum:6aaaa8e12793e03c75135459645b3a6b
: end
[/code:1][/b]
static (inside,dmz) 10.0.0.0 10.0.0.0 netmask 255.255.255.0
Ok, a little precursor. I want to set up a 3rd VLAN for some instruments in our office. I want the 3rd VLAN to talk ONLY to the inside interface (VLAN1). There is no need for this network to talk
to VLAN2(outside).
I have a smartnet agreement but the folks at Cisco can't seem to figure out what is going on.
note: the ip address to my outside connection was modified for safety reasons
Here's how my network is laid out right now
internet
|
ASA 5505
|
Netgear 24port Switch (NOT MANAGED)
|
workstations
When currently everything works until I hook up Eth0/2 (VLAN3) to the netgear switch (where VLAN1 also connects). It causes my inside network to collapse and nothing works.. causing my users to lose connectivity to the MSSQL database.
Here is my show run
[code:1]
Result of the command: "sh run"
: Saved
:
ASA Version 8.0(3)5
!
hostname ciscoasa
domain-name domain.local
enable password d7N4t5BlrAyLd8cs encrypted
names
!
interface Vlan1
nameif inside
security-level 100
ip address 10.0.0.1 255.255.255.0
!
interface Vlan2
nameif outside
security-level 0
ip address 74.x.x.x 255.255.255.248
!
interface Vlan3
no forward interface Vlan2
nameif dmz
security-level 50
ip address 172.16.0.1 255.255.0.0
!
interface Ethernet0/0
switchport access vlan 2
!
interface Ethernet0/1
!
interface Ethernet0/2
switchport access vlan 3
!
interface Ethernet0/3
!
interface Ethernet0/4
!
interface Ethernet0/5
!
interface Ethernet0/6
!
interface Ethernet0/7
!
passwd d7N4t5BlrAyLd8cs encrypted
boot system disk0:/asa803-5-k8.bin
ftp mode passive
clock timezone CST -6
clock summer-time CDT recurring
dns domain-lookup inside
dns server-group DefaultDNS
name-server 10.0.0.5
domain-name domain.local
access-list VPN_splitTunnelAcl standard permit 10.0.0.0 255.255.255.0
access-list inside_nat0_outbound extended permit ip any 192.168.100.0 255.255.255.240
access-list inside_access_in extended permit ip any any
access-list inbound extended permit tcp any 74.x.x.x 255.255.255.248 eq https
access-list inbound extended permit tcp any 74.x.x.x 255.255.255.248 eq 444
access-list inbound extended permit tcp any 74.x.x.x 255.255.255.248 eq 4125
access-list inbound extended permit tcp 66.18.18.0 255.255.254.0 74.x.x.x 255.255.255.248 eq smtp
access-list inbound extended permit tcp any 74.x.x.x 255.255.255.248 eq www inactive
access-list inbound extended permit icmp any 74.x.x.x 255.255.255.248 echo-reply
access-list dmz_inside extended permit ip any any
pager lines 24
logging enable
logging timestamp
mtu inside 1500
mtu outside 1500
mtu dmz 1500
ip local pool vpn_pool 192.168.100.1-192.168.100.10 mask 255.255.255.0
icmp unreachable rate-limit 1 burst-size 1
icmp deny any outside
asdm image disk0:/asdm-611.bin
no asdm history enable
arp timeout 14400
global (outside) 1 interface
nat (inside) 0 access-list inside_nat0_outbound
nat (inside) 1 0.0.0.0 0.0.0.0
static (inside,outside) tcp interface https 10.0.0.5 https netmask 255.255.255.255
static (inside,outside) tcp interface smtp 10.0.0.5 smtp netmask 255.255.255.255
static (inside,outside) tcp interface 444 10.0.0.5 444 netmask 255.255.255.255
static (inside,outside) tcp interface 4125 10.0.0.5 4125 netmask 255.255.255.255
static (inside,outside) tcp interface www 10.0.0.5 www netmask 255.255.255.255
static (inside,dmz) 10.0.0.0 10.0.0.0 netmask 255.255.255.0
access-group inbound in interface outside
access-group dmz_inside in interface dmz
route outside 0.0.0.0 0.0.0.0 74.x.x.x 1
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
dynamic-access-policy-record DfltAccessPolicy
http server enable
http 0.0.0.0 0.0.0.0 inside
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart
crypto ipsec transform-set ESP-3DES-SHA esp-3des esp-sha-hmac
crypto dynamic-map outside_dyn_map 20 set pfs
crypto dynamic-map outside_dyn_map 20 set transform-set ESP-3DES-SHA
crypto isakmp policy 10
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 86400
crypto isakmp nat-traversal 30
no vpn-addr-assign aaa
no vpn-addr-assign dhcp
vpn-addr-assign local reuse-delay 5
telnet 10.0.0.0 255.255.255.0 inside
telnet timeout 5
ssh 0.0.0.0 0.0.0.0 inside
ssh timeout 60
console timeout 5
management-access inside
threat-detection basic-threat
threat-detection scanning-threat shun except ip-address 10.0.0.0 255.255.255.0
no threat-detection statistics access-list
webvpn
csd image disk0:/securedesktop-asa-3.2.1.118-k9.pkg
svc image disk0:/sslclient-win-1.1.4.177.pkg 1 regex "Windows NT"
group-policy DfltGrpPolicy attributes
vpn-tunnel-protocol IPSec l2tp-ipsec
group-policy VPN internal
group-policy VPN attributes
banner none
wins-server value 10.0.0.5
dns-server value 10.0.0.5
vpn-idle-timeout 15
vpn-tunnel-protocol IPSec
split-tunnel-policy tunnelspecified
split-tunnel-network-list value VPN_splitTunnelAcl
default-domain value domain.local
username dupont password OjS8FBaCgk.begt2 encrypted
username dupont attributes
vpn-group-policy VPN
service-type remote-access
username dluu password DyFC5OurFNi0sR/M encrypted
username dluu attributes
vpn-group-policy VPN
service-type remote-access
username Sherri password /HO7xE8y7KG65PnQ encrypted
username Sherri attributes
vpn-group-policy VPN
service-type remote-access
username Ryan password A9xIwcNgAeJ9htI1 encrypted
username Ryan attributes
vpn-group-policy VPN
tunnel-group VPN type remote-access
tunnel-group VPN general-attributes
address-pool vpn_pool
default-group-policy VPN
password-management
tunnel-group VPN ipsec-attributes
pre-shared-key *
isakmp keepalive threshold 120 retry 2
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum 512
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect sqlnet
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
inspect skinny
!
service-policy global_policy global
prompt hostname context
Cryptochecksum:6aaaa8e12793e03c75135459645b3a6b
: end
[/code:1][/b]
Lets start with correcting this statement:
static (inside,dmz) 10.0.0.0 10.0.0.0 netmask 255.255.255.0
Correct it how? This is what Cisco TAC told me to put there. What you typed (quoted) is what's already in my 5505? Did I miss something?
Oops. Also note that the subnet mask for the 172.x address is really 255.255.255.0. I changed it to 255.255.0.0 to test if a different subnet mask helped (it didn't).. so the vlan3 should be 172.16.0.x/255.255.255.0
Here is a 'proper' show run for the config I want.
[code:1]
Result of the command: "sh run"
: Saved
:
ASA Version 8.0(3)5
!
hostname ciscoasa
domain-name domain.local
enable password d7N4t5BlrAyLd8cs encrypted
names
!
interface Vlan1
nameif inside
security-level 100
ip address 10.0.0.1 255.255.255.0
!
interface Vlan2
nameif outside
security-level 0
ip address 74.x.x.x 255.255.255.248
!
interface Vlan3
no forward interface Vlan2
nameif dmz
security-level 50
ip address 172.0.0.1 255.255.255.0
!
interface Ethernet0/0
switchport access vlan 2
!
interface Ethernet0/1
!
interface Ethernet0/2
switchport access vlan 3
!
interface Ethernet0/3
!
interface Ethernet0/4
!
interface Ethernet0/5
!
interface Ethernet0/6
!
interface Ethernet0/7
!
passwd d7N4t5BlrAyLd8cs encrypted
boot system disk0:/asa803-5-k8.bin
ftp mode passive
clock timezone CST -6
clock summer-time CDT recurring
dns domain-lookup inside
dns server-group DefaultDNS
name-server 10.0.0.5
domain-name domain.local
access-list VPN_splitTunnelAcl standard permit 10.0.0.0 255.255.255.0
access-list inside_nat0_outbound extended permit ip any 192.168.100.0 255.255.255.240
access-list inside_access_in extended permit ip any any
access-list inbound extended permit tcp any 74.x.x.x 255.255.255.248 eq https
access-list inbound extended permit tcp any 74.x.x.x 255.255.255.248 eq 444
access-list inbound extended permit tcp any 74.x.x.x 255.255.255.248 eq 4125
access-list inbound extended permit tcp 66.18.18.0 255.255.254.0 74.x.x.x 255.255.255.248 eq smtp
access-list inbound extended permit tcp any 74.x.x.x 255.255.255.248 eq www inactive
access-list inbound extended permit icmp any 74.x.x.x 255.255.255.248 echo-reply
access-list dmz_inside extended permit ip any any
pager lines 24
logging enable
logging timestamp
mtu inside 1500
mtu outside 1500
mtu dmz 1500
ip local pool vpn_pool 192.168.100.1-192.168.100.10 mask 255.255.255.0
icmp unreachable rate-limit 1 burst-size 1
icmp deny any outside
asdm image disk0:/asdm-611.bin
no asdm history enable
arp timeout 14400
global (outside) 1 interface
nat (inside) 0 access-list inside_nat0_outbound
nat (inside) 1 0.0.0.0 0.0.0.0
static (inside,outside) tcp interface https 10.0.0.5 https netmask 255.255.255.255
static (inside,outside) tcp interface smtp 10.0.0.5 smtp netmask 255.255.255.255
static (inside,outside) tcp interface 444 10.0.0.5 444 netmask 255.255.255.255
static (inside,outside) tcp interface 4125 10.0.0.5 4125 netmask 255.255.255.255
static (inside,outside) tcp interface www 10.0.0.5 www netmask 255.255.255.255
static (inside,dmz) 10.0.0.0 10.0.0.0 netmask 255.255.255.0
access-group inbound in interface outside
access-group dmz_inside in interface dmz
route outside 0.0.0.0 0.0.0.0 74.x.x.x 1
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
dynamic-access-policy-record DfltAccessPolicy
http server enable
http 0.0.0.0 0.0.0.0 inside
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart
crypto ipsec transform-set ESP-3DES-SHA esp-3des esp-sha-hmac
crypto dynamic-map outside_dyn_map 20 set pfs
crypto dynamic-map outside_dyn_map 20 set transform-set ESP-3DES-SHA
crypto isakmp policy 10
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 86400
crypto isakmp nat-traversal 30
no vpn-addr-assign aaa
no vpn-addr-assign dhcp
vpn-addr-assign local reuse-delay 5
telnet 10.0.0.0 255.255.255.0 inside
telnet timeout 5
ssh 0.0.0.0 0.0.0.0 inside
ssh timeout 60
console timeout 5
management-access inside
threat-detection basic-threat
threat-detection scanning-threat shun except ip-address 10.0.0.0 255.255.255.0
no threat-detection statistics access-list
webvpn
csd image disk0:/securedesktop-asa-3.2.1.118-k9.pkg
svc image disk0:/sslclient-win-1.1.4.177.pkg 1 regex "Windows NT"
group-policy DfltGrpPolicy attributes
vpn-tunnel-protocol IPSec l2tp-ipsec
group-policy VPN internal
group-policy VPN attributes
banner none
wins-server value 10.0.0.5
dns-server value 10.0.0.5
vpn-idle-timeout 15
vpn-tunnel-protocol IPSec
split-tunnel-policy tunnelspecified
split-tunnel-network-list value VPN_splitTunnelAcl
default-domain value domain.local
username dupont password OjS8FBaCgk.begt2 encrypted
username dupont attributes
vpn-group-policy VPN
service-type remote-access
username dluu password DyFC5OurFNi0sR/M encrypted
username dluu attributes
vpn-group-policy VPN
service-type remote-access
username Sherri password /HO7xE8y7KG65PnQ encrypted
username Sherri attributes
vpn-group-policy VPN
service-type remote-access
username Ryan password A9xIwcNgAeJ9htI1 encrypted
username Ryan attributes
vpn-group-policy VPN
tunnel-group VPN type remote-access
tunnel-group VPN general-attributes
address-pool vpn_pool
default-group-policy VPN
password-management
tunnel-group VPN ipsec-attributes
pre-shared-key *
isakmp keepalive threshold 120 retry 2
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum 512
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect sqlnet
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
inspect skinny
!
service-policy global_policy global
prompt hostname context
Cryptochecksum:6aaaa8e12793e03c75135459645b3a6b
: end[/code:1]