How and Why You Should Verify IOS Images On Cisco Routers & Catalyst Switches. Identify Corrupt & Tampered Images using SHA2 or MD5 Verification
 Chances are we’ve all needed to upgrade our Cisco’s device IOS software at some point. While upgrading the IOS software on a Cisco device is considered to be a fairly simple process, it can turn out to be a very stressful and destructive process if something goes wrong, especially if the upgrade is being performed on a remote Cisco device. Uploading a corrupt IOS image or having it become corrupt during the upload process is a common problem Cisco engineers encounter.
Chances are we’ve all needed to upgrade our Cisco’s device IOS software at some point. While upgrading the IOS software on a Cisco device is considered to be a fairly simple process, it can turn out to be a very stressful and destructive process if something goes wrong, especially if the upgrade is being performed on a remote Cisco device. Uploading a corrupt IOS image or having it become corrupt during the upload process is a common problem Cisco engineers encounter.
If a corrupted IOS image is not identified before the reload/reboot of the device, it’s most likely the device will not boot again unless a special recovery procedure is followed. A corrupt IOS image translates to network downtime, service disruption and possibly financial loss for the company.
Therefore verifying an IOS image that has been uploaded to a Cisco device is a very important step, regardless how experienced one might be. Unfortunately most network engineers skip or are totally unaware of the image verification process and the trouble it can help them avoid.
Here are a few reasons why Cisco IOS image verification should become a mandatory step during any upgrade:
- It helps ensure the IOS image is not corrupt
- It avoids unnecessary surprises after a router/switch reload - especially when it’s at a remote location!
- It verifies the integrity of the software
- Reduces the risk of malicious code being installed on the Cisco IOS device
- TFTP, the method often used to upload files, cannot guarantee error-free transfers
- Helps maintain your professional image and reliability :)
Using The SHA2/MD5 File Verification Feature
The MD5 File Validation feature was added in Cisco IOS Software Releases 12.2(4)T and 12.0(22)S onwards. This feature allows the administrator to calculate the MD5 hash of a Cisco IOS software image previously loaded on a device's flash.
Newer IOS images and ISR routers now make use of the SHA2 algorithm, rather than the older MD5, however we can optionally verify the image using MD5.
Cisco publishes the MD5 hash value (Checksum) for every software image in their download area. This enables the network engineer to easily check and compare the calculated MD5 hash value against Cisco’s site and identify any signs of tampering.
Below is a Cisco 2921 router that has just had an IOS image uploaded (c2900-universalk9-mz.SPA.152-4.M6a.bin):
Directory of flash0:/
1 -rw- 99137584 Dec 7 2022 20:57:20 +03:00 c2900-universalk9-mz.SPA.152-4.M6a.bin
2 -rw- 97114876 Aug 7 2022 21:57:20 +03:00 c2900-universalk9-mz.SPA.154-1.T1.bin
3 -rw- 3064 Aug 7 2022 21:08:32 +03:00 cpconfig-29xx.cfg
4 drw- 0 Aug 7 2022 21:08:54 +03:00 ccpexp
5 -rw- 2464 Aug 7 2022 21:10:36 +03:00 home.shtml
256487424 bytes total (154890240 bytes free)
Before changing the device’s configuration to load the newly uploaded IOS image, we need to verify its integrity first by using the verify command:
Starting image verification
Hash Computation: 100% Done!
Computed Hash SHA2: 8E9A291FD3203FE665F17EC137B01C16
76D997C83ABEDA953379D88D018C8933
B461FE204B503AE7F4D4CAA76C516445
6B81994221B5D4ACEB94860DAFA6EB85
Embedded Hash SHA2: 8E9A291FD3203FE665F17EC137B01C16
76D997C83ABEDA953379D88D018C8933
B461FE204B503AE7F4D4CAA76C516445
6B81994221B5D4ACEB94860DAFA6EB85
CCO Hash MD5 : CEC1428C33BCE462346D77445D5A468D
Digital signature successfully verified in file flash0:c2900-universalk9-mz.SPA.152-4.M6a.bin
When issuing the verify command, the router will compute and automatically verify the image using the SHA2 algorithm and then compare it against the embedded SHA2 hash. This verification ensures that the file is not corrupt and has not been tampered with.
To verify the image using MD5, we can use the verify /md5 command as shown below:
Done! verify /md5 (flash0:c2900-universalk9-mz.SPA.152-4.M6a.bin) = cec1428c33bce462346d77445d5a468d
Verifying The MD5 HASH With Cisco's Site
As noted in our previously, an additional security check is available for those seeking to fully satisfy their security concerns. Cisco makes the MD5 hash available for every image in their download section, allowing the network engineer to compare the embedded and calculated MD5 hash with Cisco.
Using our image c2900-universalk9-mz.SPA.152-4.M6a.bin as an example, we went to Cisco’s download section and located the file. By simply placing our mouse cursor above the filename, a popup window appeared showing the file details where the MD5 Checksum can also be found:
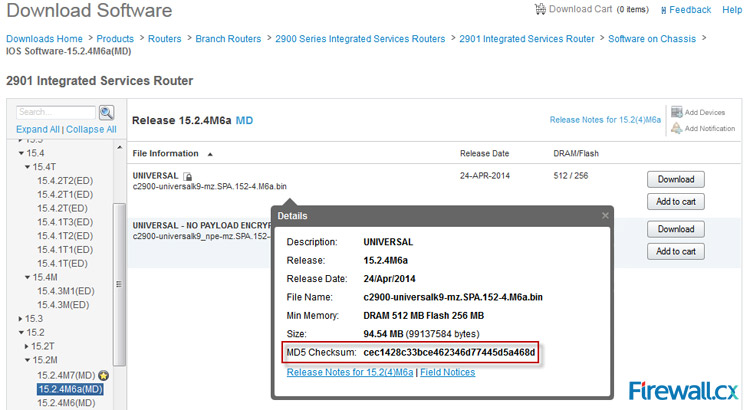
Our calculated MD5 checksum was also cec1428c33bce462346d77445d5a468d, which means we have a Cisco original image that has not been altered or tampered in any way.
This article explained the importance of verifying a Cisco IOS image and the problems this simple step can help avoid. We also explained how to verify the image using the SHA2 or MD5 algorithm and compare it against Cisco’s website.
Your IP address:
3.137.165.75
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!













