MPLS vs. SD-WAN vs. Internet vs. Cloud Network. Connectivity, Optimization and Security Options for the ‘Next Generation WAN’
 The Wide Area Network (WAN) is the backbone of the business. It ties together the remote locations, headquarters and data centers into an integrated network. Yet, the role of the WAN has evolved in recent years. Beyond physical locations, we now need to provide optimized and secure access to Cloud-based resources for a global and mobile workforce. The existing WAN optimization and security solutions, designed for physical locations and point-to-point architectures, are stretched to support this transformation.
The Wide Area Network (WAN) is the backbone of the business. It ties together the remote locations, headquarters and data centers into an integrated network. Yet, the role of the WAN has evolved in recent years. Beyond physical locations, we now need to provide optimized and secure access to Cloud-based resources for a global and mobile workforce. The existing WAN optimization and security solutions, designed for physical locations and point-to-point architectures, are stretched to support this transformation.
This article discusses the different connectivity, optimization and security options for the ‘Next Generation WAN’ (NG-WAN). The NG-WAN calls for a new architecture to extend the WAN to incorporate the dynamics of cloud and mobility, where the traditional network perimeter is all but gone.
The Wide Area Network (WAN) connects all business locations into a single operating network. Traditionally, WAN design had to consider the secure connectivity of remote offices to a headquarters or a data center which hosted the enterprise applications and databases.
Without further delay, let's take a look at the topics cover in this article:
- First-generation: Legacy WAN Connectivity
- 1: MPLS - SLA Backed Service at Premium Price
- 2: Internet - Best-Effort Service at Discounted Price
- Second Generation: Appliance-based SD-WAN
- SD-WAN Augmenting MPLS with Internet Links
- Third Generation: A Cloud-based, Secure SD-WAN
- Summary
Let’s look at evolution of the WAN.
First Generation: Legacy WAN Connectivity
Currently, there are 2 WAN connectivity options which offer a basic tradeoff between cost, availability and latency:
Option 1: MPLS - SLA-Backed Service at Premium Price
With MPLS, a telecommunication provider provisions two or more business locations with a managed connection and routes traffic between these locations over their private backbone. In theory, since the traffic does not traverse the internet, encryption is optional. Because the connection is managed by the telco, end to end, it can commit to availability and latency SLAs. This commitment is expensive and is priced by bandwidth. Enterprises choose MPLS if they need to support applications with stringent up-time requirements and minimal quality of service (such as Voice over IP (VOIP).
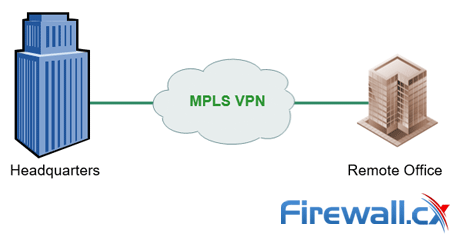
Headquarters connecting to remote offices via MPLS Premium service
To maximize the usage of MPLS links, WAN optimization equipment is deployed at each end of the line, to prioritize and reduce different types of application traffic. The effectiveness of such optimizations is protocol and application specific (for example, compressed streams benefit less from WAN optimization).
Positives:
- Latency: Low
- Availability: High
Concerns:
- Price: High
Option 2: Internet - Best Effort Service at a Discounted Price
Internet connection procured from the ISP, typically offers nearly unlimited last mile capacity for a low monthly price. An unmanaged internet connection doesn’t have the high availability and low-latency benefits of MPLS but it is inexpensive and quick to deploy. IT establishes an encrypted VPN tunnel between the branch office firewall and the headquarters/data center firewall. The connection itself is going through the internet, with no guarantee of service levels because it is not possible to control the number of carriers or the number of hops a packet has to cross. This can cause unpredictable application behavior due to increased latency and packet loss.
Internet-based connectivity forces customers to deploy and manage branch office security equipment.
Positives:
- Price: Low
Concerns:
Latency: Unknown
Availability: Low
Second Generation: Appliance-Based SD-WAN
The cost/performance tradeoff between internet and MPLS, gave rise to SD-WAN. SD-WAN is using both MPLS and internet links to handle WAN traffic. Latency sensitive apps are using the MPLS links, while the rest of the traffic is using the internet link. The challenge customers face is to dynamically assign application traffic to the appropriate link.
Readers interested in SD-WANs should read our Complete Guide to SD-WAN article.
Related articles:
- Complete Guide to SD-WAN. Technology Benefits, SD-WAN Security, Management, Mobility, VPNs, Architecture and more
- The Need for a Converged SASE Platform. Converging Network & Security Services with Catonetworks SASE Platform
- How To Secure Your SD-WAN. Comparing DIY, Managed SD-WAN and SD-WAN Cloud Services
- SASE and VPNs: Reconsidering your Mobile Remote Access and Site-to-Site VPN strategy
- Converged SASE Backbone – How Leading SASE Provider, Cato Networks, Reduced Jitter/Latency and Packet Loss by a Factor of 13!
- Key Features of a True Cloud-Native SASE Service. Setting the Right Expectations
SD-WAN: Augmenting MPLS with Internet Links
SD-WAN solutions offer the management capabilities to direct the relevant traffic according to its required class of service, offloading MPLS links and delaying the need to upgrade capacity.
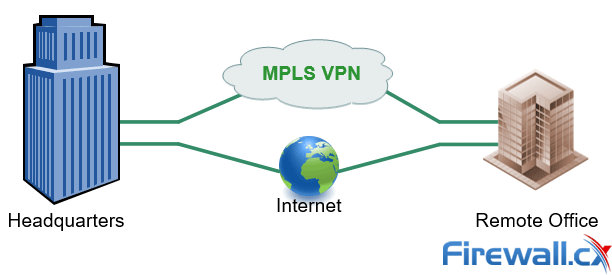
SD-WAN solutions, however, are limited in a few key aspects:
SD-WAN Footprint
Similar to WAN optimization equipment, SD-WAN solutions must have a box deployed at each side of the link.
Connectivity
SD-WAN can’t replace the MPLS link because its internet “leg” is exposed to the unpredictable nature of an unmanaged internet connection (namely, its unpredictable latency, packet drops and availability).
Deployment
SD-WAN, like the other WAN connectivity options, is agnostic to the increased role of internet, Cloud and mobility within the enterprise network. It focuses, for the most part on optimizing the legacy, physical WAN.
Third Generation: A Cloud-based, Secure SD-WAN
With the rapid migration to Cloud applications (e.g., Office 365), Cloud infrastructure (e.g. Amazon AWS) and a mobile workforce, the classic WAN architecture is severely challenged. It is no longer sufficient to think in terms of physical locations being the heart of the business, and a new cloud-based SD-WAN solution was born. Here is why:
Limited end to end link control for the Cloud
With public cloud applications outside the control of IT, organizations can’t rely on optimizations that require a box at both ends of each link. In addition, Cloud infrastructure (servers and storage), introduces a new production environment that has its own connectivity and security requirements. Existing WAN and Security solutions don’t naturally extend to the new Cloud-based environments.
Limited service and control to mobile users
Securely accessing corporate resources requires, mobile users to connect to a branch or HQ firewall VPN which could be very far from their location. This causes user experience issues, and encourages compliance violations (for example, direct access to Cloud services that bypasses corporate security policy). Ultimately, the mobile workforce is not effectively covered by the WAN.
The Cloud-based, Secure SD-WAN is aiming to address these challenges. It is based on the following principles:
The Perimeter Moves to the Cloud
The notorious dissolving perimeter is re-established in the Cloud. The Cloud delivers a managed WAN backbone with reduced latency and optimal routing. This ensures the required quality of service for both internal and Cloud-based applications.
The Cloud-Βased WAN is “Democratic” and All-Inclusive
All network elements plug into the Cloud WAN with secure tunnels including physical locations, Cloud resources and mobile users. This ensures all business elements are integral part of the network instead of being bolted on top of a legacy architecture.
Security is Ιntegrated into the Νetwork
Beyond securing the backbone itself, it is possible to directly secure all traffic (WAN and internet) that crosses the perimeter - without deploying distributed firewalls.
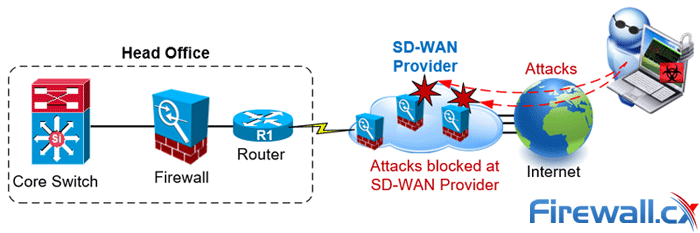
As shown in the example above, the SD-WAN provider acts as a gateway to the internet for the business. Any attempts to gain access to the business network or attacks must pass through the SD-WAN provider's secure network. This not only provides increased levels of security but also off-loads attacks directly to the SD-WAN provider, saving the business considerable bandwidth and resources needed to repel attacks.
Summary
This article compared SD-WAN solutions with Service Provider MPLS, Internet and Cloud Networks. We examined the positive and negative offerings of MPLS services (guaranteed SLAs), Internet-based WAN solutions (best-effort service), augmenting MPLS with Internet links and Cloud networks. For more information on SD-WAN, refer to our Complete Guide to SD-WAN networks.
Your IP address:
3.142.194.159
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!













