Configuring A SASE Unified Network: Data centers, Remote Sites, VPN Users, and more
 This article explores the need for Secure Access Service Edge (SASE) in today’s organizations. We show how one of the most advanced SASE platforms available, combines VPN and VPN and SD-WAN capabilities with cloud-native security functions to quickly and securely connect On-premises data centers, cloud data centers, branch offices, and remote users.
This article explores the need for Secure Access Service Edge (SASE) in today’s organizations. We show how one of the most advanced SASE platforms available, combines VPN and VPN and SD-WAN capabilities with cloud-native security functions to quickly and securely connect On-premises data centers, cloud data centers, branch offices, and remote users.
Before we dive any further, let’s take a look at what’s covered:
- SASE: The Architecture for a Secure Cloud and Mobile World
- Defining SASE
- The Four Pillars of SASE Architecture
- SASE Showcase: Connecting & Managing All Locations Together
- The SASE Unified Network
- Summary
Related Articles
- Complete Guide to SD-WAN. Technology Benefits, SD-WAN Security, Management, Mobility, VPNs, Architecture & Comparison with Traditional WANs. SD-WAN Providers Feature Checklist
- SD-WAN is the Emerging, Evolving Solution for the Branch Office
- Understanding Secure Access Service Edge (SASE) and how it integrates with SD-WAN
- SASE and VPNs: Reconsidering your Mobile Remote Access and Site-to-Site VPN strategy
SASE: The Architecture for a Secure Cloud and Mobile World
IT and security managers are constantly concerned by the different entities which connect to their networks. Keeping track of who is connecting, using which edge device type, what they’re connecting to, and which permissions they should have can be a messy and dangerous business.
An enterprise’s network is composed of several types of edges. An edge can be any location or endpoint which needs to connect to any other resource or service available inside or outside the network. This includes the enterprise’s on-premises headquarters, branch offices, data centers, mobile users connecting remotely (e.g. their home), public cloud data centers (e.g. AWS and Azure), 3rd party SaaS applications (e.g. Office365 and Salesforce), and virtually any website across the WWW.
To enable connectivity and secure access for all edges, enterprises are forced to adopt different solutions to manage different edge types. For example VPN for remote users, on-prem Next Generation Firewalls (NGFWs) for the physical locations, cloud-based NGFW for cloud-based applications, Cloud Access Security Brokers (CASB) for SaaS and Secure Web Gateways (SWG) for web access. This large number of different products introduced unwanted complexity, inefficiency, and potential security loopholes to enterprises. But perhaps there is a better way to enable secure access to any service from any edge? In fact, there is, and it’s called, surprisingly enough, Secure Access Service Edge (SASE).
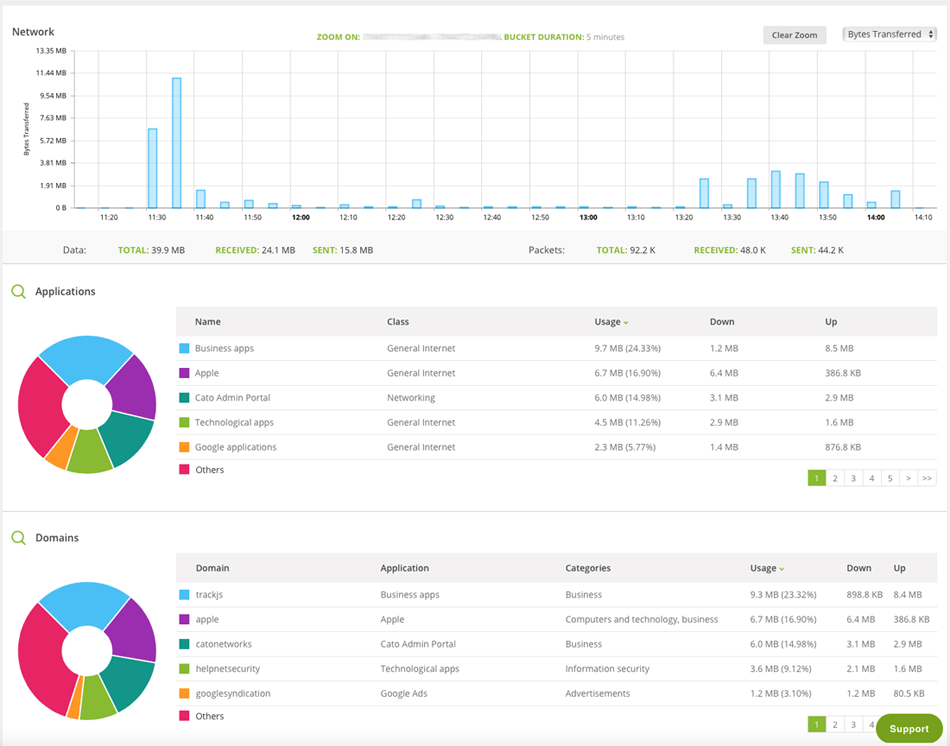
Cloud-based SASE Traffic Analysis Dashboard
Defining SASE
SASE is a new architecture that converges networking and security into a holistic, unified cloud service. It is a concept defined by Gartner in late 2019 to simplify enterprise networking and security. At the heart of the SASE premise lays the understanding that network and security cannot be addressed separately, using different products and services. The inter-dependency between the two is fundamental, and their convergence is critical for addressing the needs of the modern digital enterprise.
Click here to learn more about SASE and how it differs from SD-WAN.
The Four Pillars of SASE Architecture:
Four main principles lay at the heart of the SASE architecture:
- All edges. A true SASE solution should be able to service all enterprise edge types.
- Converged. SASE’s networking and security services should be delivered from one software stack, not discrete appliances integrated together, and all must be managed via a single pane of glass.
- Cloud-native. A SASE solution should be built using cloud-native technologies and should support elasticity, auto-scaling and high-availability.
- Global. An effective SASE solution should have an extensive global footprint of Points of Presence (PoPs) covering all major locations worldwide.
SASE Showcase: Connecting & Managing All Locations Together
One of SASE’s main goals is to simplify connectivity, access, and management of the enterprise. This is achieved by unifying all the required functionality into a single solution.
For example, in Cato Network’s SASE Cloud platform, all edges connect to the closest Cato PoP and are managed from Cato’s management console. All traffic to and from these edges undergo the same networking optimizations and security inspections to detect and mitigate threats in real-time.
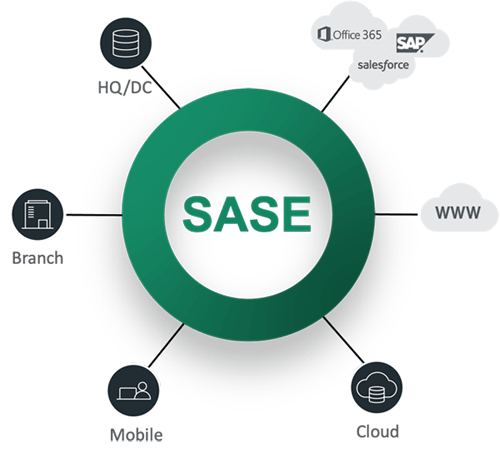
The Cato Network SASE platform provides complete connectivity & management of all endpoints
Connecting physical locations such as the headquarters, branch offices, and data centers, is the simplest scenario. They are controlled by the enterprise and enable an easy deployment of an SD-WAN appliance such as the X1500 (left) and X1700 (right) Cato Socket models shown below:

The Cato Socket can manage multiple connections, preferably from multiple ISPs, in active/active mode and continuously monitors them to determine the best performing link to send traffic over:
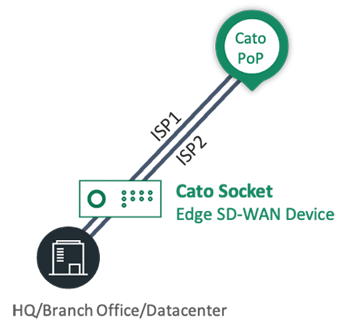
On-Premises Edge
Furthermore, the Cato Socket can make user- and application-aware decisions for implementing the defined QoS policies.
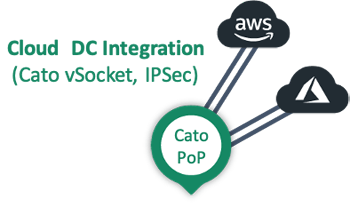
In addition to connecting the enterprise’s on-premises data centers, we also need to connect cloud-based applications at public clouds (AWS and Azure). For these environments, we will use Cato’s virtual socket (vSocket) as shown below:
Defining network connectivity to any of these locations is done quickly and easily via Cato’s Management console. By clicking the Configuration drop-down menu and selecting Sites you are taken to the site configuration screen:
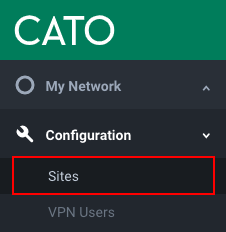
Site Configuration
Then by opening the Add site dialog screen, we can configure a new site. We start by naming the new site e.g Best Site Ever:
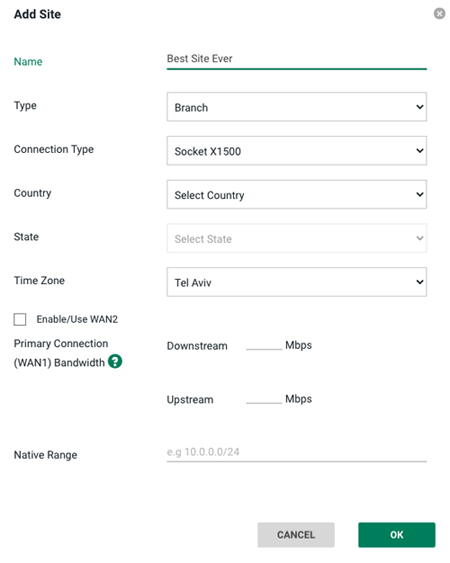
New Site Configuration
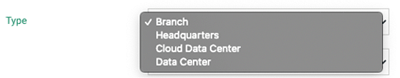
We then open the site Type drop-down menu and select the site type. Available options include Branch, Headquarters, Cloud Data Center or Data Center (on-premises):
Next, we open the “Connection Type” drop-down menu (see figure below) and select the type of Cato Socket connector we wish to use for our site:
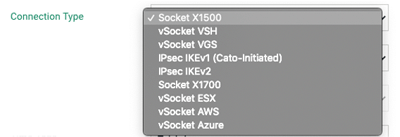
Socket Type Selection
Physical locations typically use the X1500 or X1700 Cato Sockets, while cloud data center locations typically use one of the Cato virtual sockets (vSocket), depending on the cloud being accessed. As can be seen from the list of connections types, there is also an option to connect both physical and cloud sites using an IPsec tunnel.
The additional configurations are pretty straightforward. In addition to country and time zone, we need to define the uplink/downlink bandwidth limitations for the site and the local subnet used to allocate IP addresses to local hosts. And that’s it. Our site is ready go.
Adding remote users is also a breeze. In the configuration section below, select VPN Users:
We then click on the “+” icon and the new user dialog is shown:
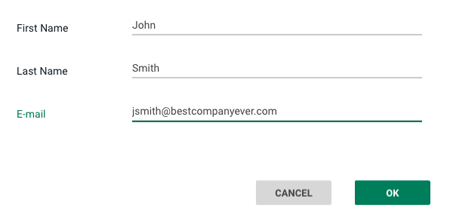
New User Configuration
We fill in the user’s full name and email address, and the new user is defined. We then add the user’s phone number and a link for downloading and configuring the Cato client.
Once the Cato Client is installed and launched on the user’s device, it will automatically search for the nearest PoP and establish a secure connection with it:
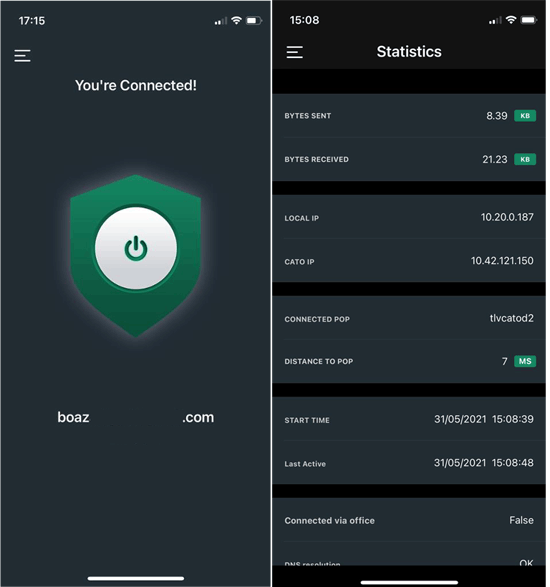
The Cato SDP VPN Client
All traffic sent to and from the device is encrypted. The Cato SDP client provides a wide range of statistics, including traffic usage, PoP information, and more.
The SASE Unified Network
Once we’re done configuring all our different edges, we can easily view our entire network topology by selecting My Network > Topology:
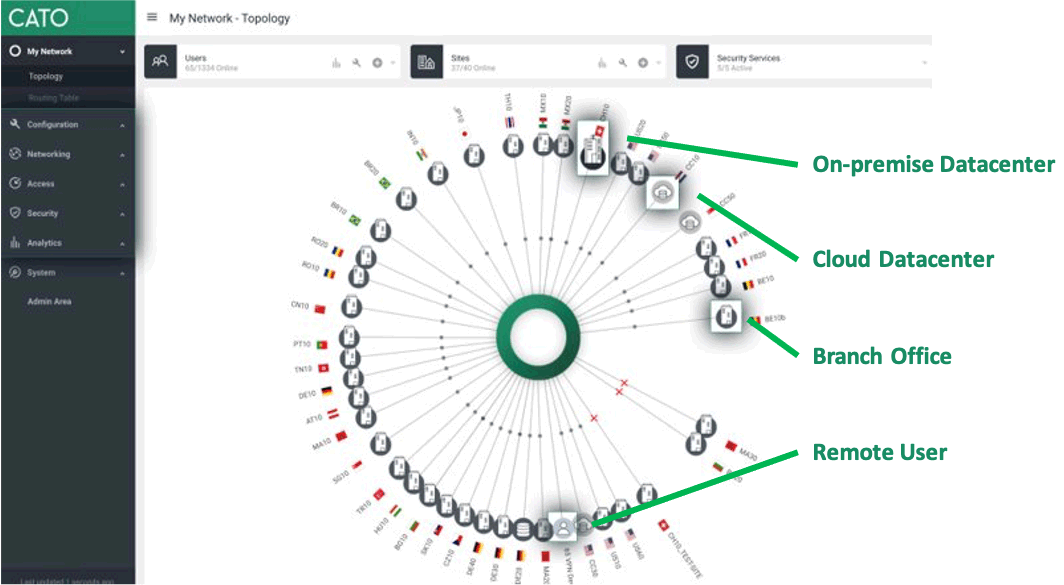
Network Topology
We can see all the edges we have defined: On-premises data centers, cloud data centers, HQ/branch offices, and remote users. We can see its status for each defined edge and take a deeper dive to view extensive analytics covering networking, security, and access metrics.
A true SASE solution should enable access and optimize and secure traffic for all network edges. It should make adding new sites and users easy and fast, and it should provide a unified view of your entire network topology.
Summary
In this article, we briefly covered the purpose of SASE and showed how a SASE solution could be used to connect all edge points within an organization, regardless of their location or size. Catonetwork’s SASE platform was used as an example to show how easily a SASE solution can be deployed to provide fast and secure access to users and offices around the world. We examined the four pillars of SASE architecture and saw what a SASE unified network looks like.
More information on SD-WAN and SASE can be found in our dedicated SASE and SD-WAN section.
Your IP address:
3.131.13.161
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!















