Spanning Tree BPDU Guard and Errdisable Interface Automatic Recovery
Running Spanning Tree Protocol (STP) in a large network environment can be a challenging task especially when features/enhancements such as BPDU Filter and BPDU Guard need to be configured to help STP adapt to the network infrastructure requirements.
The key to a successful STP deployment is understanding how each STP feature should be used and implemented.
Understanding & Configuring BPDU Guard
BPDU Guard is an STP enhancement which, when enabled, will place a port in the errdisable mode when it receives any BPDU packet from that port.
BPDU Guard is usually configured on access layer ports where we are not expecting to see any BPDU packets arriving from devices connected to these ports e.g computers, printers, IP phones or other user-end devices.
Ports used as uplinks or downlinks to other switches should not have BPDU Guard enabled as these are more likely to have BPDU packets transmitted and received as switches actively monitor for network loops.
BPDU Guard can be configured either in Global mode or Interface mode.
When configured in Global mode the feature is enabled globally for all switch ports configured with port-fast configuration. Port-Fast is an STP feature configured at each individual port that forces the port to go directly into a forwarding state rather than through the normal STP states (Listening, Learning, Forwarding).
While port-fast is a very handy feature that forces a network port to transition immediately to the forwarding state (similar to an unmanaged switch), it must be used with caution as STP won’t be able to immediately detect a network loop through a Port-Fast enabled port.
To configure BPDU Guard in Global mode use the spanning-tree portfast bpduguard default command in Global Configuration Mode:
SW2(config)# spanning-tree portfast bpduguard default
To configure BPDU Guard in Interface mode use the spanning-tree bpduguard enable command under the interface:
SW2(config-if)# spanning-tree bpduguard enable
Note: It is important to keep in mind that if the interface is configured as an access port, with port-fast enabled, and receives a BPDU packet it will automatically be disabled and placed in an errdisabled state.
To help illustrate how BPDU Guard works, we’ve configured port G1/0/1 on our 3750-X as an access link with port-fast and BPDU Guard enabled:
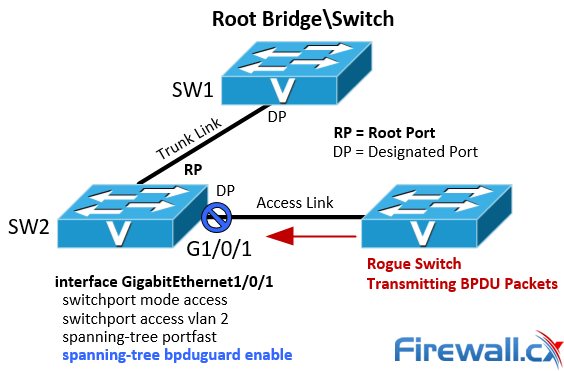
Figure 1. Spanning Tree BPDU Guard configuration and example
Next, we connect another switch (rogue switch) running spanning tree protocol to port G1/0/1 on SW2. As soon as a BPDU packet is received on G1/0/1, here’s how SW2 reacted:
As expected, the port was automatically disabled by the spanning tree protocol.
Note: If interface G1/0/1 was configured as a Trunk Port and received a BPDU packet, it would not be disabled.
Recovery From Disabled Port Due To BPDU Guard
There are many ways to recover from a port that has been placed in the errdisabled state and the most typical way used by engineers today is to issue the shutdown command followed by the no shutdown command directly under the interface’s configuration.
Automatic recovery of the errdisabled port can also be configured on the Cisco Catalyst switch. This handy feature will prevent the port from being permanently disabled, however, it means that if the unwanted condition of the port receiving a BPDU packet is continuously met, the port will flap between the up and errdisabled state.
For this reason, it is advised to use the automatic errdisable recovery feature only when absolutely necessary e.g for a remote switch that is difficult to visit.
SW2(config)# errdisable recovery interval 30
The above global configuration will recover an errdisabled port, due to bpduguard, automatically every 30 seconds.
Summary
A number of enhancements have been introduced into the Spanning Tree Protocol to make it flexible for today’s increasingly complex and demanding networks. Using enhanced STP features like BPDUGuard helps protect the network from rogue switches and avoid unwanted STP topology changes, however, it is important to understand the correct usage of BPDUGuard to ensure it’s correctly configured and placed in the STP topology.
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!














