Configuring Point-to-Point GRE VPN Tunnels - Unprotected GRE & Protected GRE over IPSec Tunnels
Generic Routing Encapsulation (GRE) is a tunneling protocol developed by Cisco that allows the encapsulation of a wide variety of network layer protocols inside point-to-point links.
A GRE tunnel is used when packets need to be sent from one network to another over the Internet or an insecure network. With GRE, a virtual tunnel is created between the two endpoints (Cisco routers) and packets are sent through the GRE tunnel.
It is important to note that packets travelling inside a GRE tunnel are not encrypted as GRE does not encrypt the tunnel but encapsulates it with a GRE header. If data protection is required, IPSec must be configured to provide data confidentiality – this is when a GRE tunnel is transformed into a secure VPN GRE tunnel.
The diagram below shows the encapsulation procedure of a simple - unprotected GRE packet as it traversers the router and enters the tunnel interface:

While many might think a GRE IPSec tunnel between two routers is similar to a site to site IPSec VPN (crypto), it is not. A major difference is that GRE tunnels allow multicast packets to traverse the tunnel whereas IPSec VPN does not support multicast packets. In large networks where routing protocols such as OSPF, EIGRP are necessary, GRE tunnels are your best bet. For this reason, plus the fact that GRE tunnels are much easier to configure, engineers prefer to use GRE rather than IPSec VPN.
This article will explain how to create simple (unprotected) and secure (IPSec encrypted) GRE tunnels between endpoints. We explain all the necessary steps to create and verify the GRE tunnel (unprotected and protected) and configure routing between the two networks.
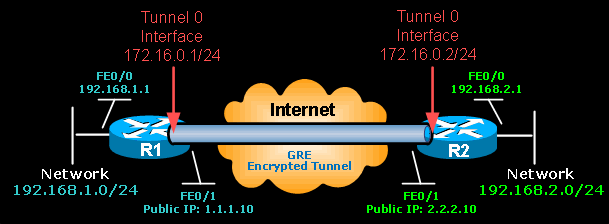
Creating a Cisco GRE Tunnel
GRE tunnel uses a ‘tunnel’ interface – a logical interface configured on the router with an IP address where packets are encapsulated and decapsulated as they enter or exit the GRE tunnel.
First step is to create our tunnel interface on R1:
All Tunnel interfaces of participating routers must always be configured with an IP address that is not used anywhere else in the network. Each Tunnel interface is assigned an IP address within the same network as the other Tunnel interfaces.
In our example, both Tunnel interfaces are part of the 172.16.0.0/24 network.
Since GRE is an encapsulating protocol, we adjust the maximum transfer unit (mtu) to 1400 bytes and maximum segment size (mss) to 1360 bytes. Because most transport MTUs are 1500 bytes and we have an added overhead because of GRE, we must reduce the MTU to account for the extra overhead. A setting of 1400 is a common practice and will ensure unnecessary packet fragmentation is kept to a minimum.
Closing, we define the Tunnel source, which is R1’s public IP address, and destination – R2’s public IP address
As soon as we complete R1’s configuration, the router will confirm the creation of the tunnel and inform about its status:
*May 4 21:30:22.971: %LINEPROTO-5-UPDOWN: Line protocol on Interface Tunnel0, changed state to up
Since the Tunnel 0 interface is a logical interface it will remain up even if there is no GRE tunnel configured or connected at the other end.
Next, we must create the Tunnel 0 interface on R2:
R2’s Tunnel interface is configured with the appropriate tunnel source and destination IP address. As with R1, R2 router will inform us that the Tunnel0 interface is up:
*May 4 21:32:54.927: %LINEPROTO-5-UPDOWN: Line protocol on Interface Tunnel0, changed state to up
Routing Networks Through The GRE Tunnel
At this point, both tunnel endpoints are ready and can ‘see’ each other. An icmp echo from one end will confirm this:
Again, this result means that the two tunnel endpoints can see each other. Workstations on either network will still not be able to reach the other side unless a static route is placed on each endpoint:
On R1 we add a static route to the remote network 192.168.2.0/24 via 172.16.0.2 which is the other end of our GRE Tunnel. When R1 receives a packet for 192.168.2.0 network, it now knows the next hop is 172.16.0.2 and therefore will send it through the tunnel.
The same configuration must be repeated for R2:
Now both networks are able to freely communicate with each over the GRE Tunnel.
Securing the GRE Tunnel with IPSec
As mentioned earlier, GRE is an encapsulation protocol and does not perform any encryption. Creating a point-to-point GRE tunnel without any encryption is extremely risky as sensitive data can easily be extracted from the tunnel and viewed by others.
For this purpose, we use IPSec to add an encryption layer and secure the GRE tunnel. This provides us with the necessary military-grade encryption and peace of mind. Our example below covers GRE IPSec Tunnel mode.
GRE IPSec modes are covered extensively in our GRE and IPSec – GRE Over IPSec - Selecting and Configuring Gre IPSec Tunnel or Transport Mode.
Configuring IPSec Encryption For GRE Tunnel (GRE over IPSec)
IPSec encryption involves two steps for each router. These steps are:
- (1) Configure ISAKMP (ISAKMP Phase 1)
- (2) Configure IPSec (ISAKMP Phase 2)
Configure ISAKMP (IKE) - (ISAKMP Phase 1)
IKE exists only to establish SAs (Security Association) for IPsec. Before it can do this, IKE must negotiate an SA (an ISAKMP SA) relationship with the peer.
To begin, we’ll start working on R1.
First step is to configure an ISAKMP Phase 1 policy:
The above commands define the following (in listed order):
Next we are going to define a pre shared key for authentication with R1's peer, 2.2.2.10:
The peer’s pre shared key is set to firewallcx. This key will be used for allISAKMP negotiations with peer 2.2.2.10 (R2).
Create IPSec Transform (ISAKMP Phase 2 policy)
Now we need to create the transform set used to protect our data. We’ve named this TS:
R1(cfg-crypto-trans)# mode transport
Finally, we create an IPSec profile to connect the previously defined ISAKMP and IPSec configuration together. We’ve named our IPSec profile protect-gre:
We are ready to apply the IPSec encryption to the Tunnel interface:
R1(config-if)# tunnel protection ipsec profile protect-gre
Now it's time to apply the same configuration on R2:
Verifying The GRE Over IPSec Tunnel
Finally, our tunnel has been encrypted with IPSec, providing us with the much needed security layer. To test and verify this, all that is required is to ping the other end and force the VPN IPSec tunnel to come up and start encrypting/decrypting our data:
Using the show crypto session command, we can quickly verify the encryption is in place and doing its work:
Summary
In this article we saw how to create simple (unprotected) and secure (IPSec encrypted) GRE tunnels between Cisco routers. We explained all the necessary steps to create and verify the GRE tunnel (unprotected and protected) and configure routing between the two networks.
Your IP address:
13.58.173.156
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!













