The Ultimate TOR vs VPN Guide – How TOR/VPN Works, Comparing Security, Speeds, Advantages and Disadvantages
 Back then, the Internet was so very young. Those were the times of Windows Maze Screensaver, of the classy Minesweeper, of grey-white MS Paint, and of silvery floppy disks. Gone are those days. Now, after completing its silver jubilee, the Internet has grown to be almost a multiverse of information, every micro-second its network mushrooms like anything. But even maturity comes with its own struggle. This enhanced version of the Internet carries its own privacy concerns.
Back then, the Internet was so very young. Those were the times of Windows Maze Screensaver, of the classy Minesweeper, of grey-white MS Paint, and of silvery floppy disks. Gone are those days. Now, after completing its silver jubilee, the Internet has grown to be almost a multiverse of information, every micro-second its network mushrooms like anything. But even maturity comes with its own struggle. This enhanced version of the Internet carries its own privacy concerns.
But not to worry, there are plenty of technologies and software developed to preserve your Internet privacy. TOR and VPN are the popular ones. So, here we explore and share which of the two comes out to be a better way to achieve a superior level of privacy on the Internet.
Before diving deep into the topic, let’s see what’s covered:
- What is Internet Privacy?
- How TOR Works
- How VPNs Work
- VPN Protocols
- PPTP – Point to Point Tunnelling Protocol
- L2TP/IPSec – Layer 2 Tunnel Protocol / IPSecurity
- SSTP – Secure Sockets Tunnelling Protocol
- OpenVPN
- When to use TOR
- When to use VPN
- TOR vs VPN – TOR Advantages and Disadvantages
- TOR vs VPN – VPN Advantages and Disadvantages
- TOR vs VPN Summary
What is Internet Privacy?
What if, at all times, someone is keeping an undersea eye on what you browse over Google, always peering into the messages as you chat with other people? Wouldn’t that make you uneasy? This is Internet privacy. That is, whatever information you share, or browsing you do over the Internet, keeps itself only to you, until you want it public.
We continually hear about governments and ISPs spying on users and even other countries, which shows how unsafe the internet is. Thankfully, user awareness on internet privacy is continually improving as more and more users seek out bullet-proof methods to encrypt their communications and protect their online privacy.
How TOR Works
 TOR or The Onion Router is a free, open source software that comes under the development and maintenance of The Tor Project, a non-profit organisation funded by the US Government. TOR enables users to preserve their anonymity over Internet communications.
TOR or The Onion Router is a free, open source software that comes under the development and maintenance of The Tor Project, a non-profit organisation funded by the US Government. TOR enables users to preserve their anonymity over Internet communications.
To download, simply go to www.TORproject.org. There’s two bundles available for downloading, one is Vidalia, which requires a web browser pre-installed on your system. However, the other one, the TOR Browser Bundle, is preferred as it puts TOR directly into your system without you having to fulfil any prerequisites or additional installations.
You can download the necessary files for your operating system by visiting: https://www.torproject.org/download/download.html.en
TOR - Onion Routing
TOR employs Onion Routing, a technology developed in the late nineties by a scientist named Syverson. It works at the TCP Layer of the network, using a multiple hop pathway. Whenever a user sends data across the network, TOR creates a relay of nodes (or hops) that decrypts the data, one layer at a time. This is where the TOR vs VPN battle actually takes off.
The relay of nodes is randomly selected proxy servers from the TOR users’ network. When the data travels from a user to the first node, it decrypts the IP address of the second node. Similarly, when it reaches the second node, it decrypts the IP address of the third node and so on till it reaches the last node. At each node only information about the next node is decrypted, thus maintaining the anonymity of the user over the entire network. When the data packet reaches the exit node, the node there finally decrypts the IP address of the destination server/node.
The following diagram provides an accurate representation of the Onion Routing method described. Like the layers of an onion, each message (the core of the onion) is covered with layers of encryption. Each layer is removed as it is received by a TOR Node (Router) and then forwarded to the next TOR Node (Router):
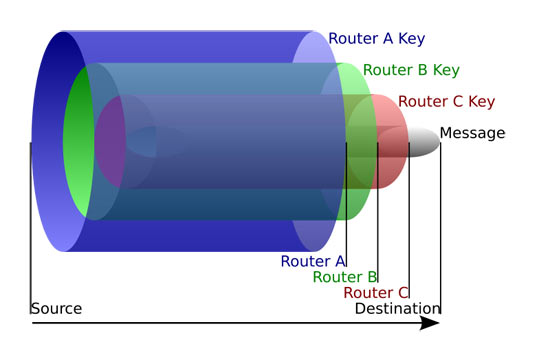
Figure 1. TOR Onion Routing method. Each layer is removed by each node to reveal the message
The diagram below is another example which shows how data is exchanged within the TOR network to guarantee privacy and make it almost impossible to track where data packets originate from or the final destination:
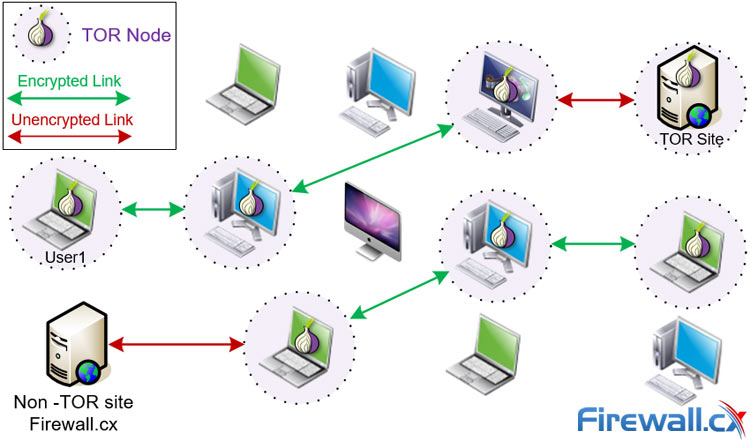
How TOR works – Data exchange between TOR nodes and normal non-TOR servers
Note that TOR nodes/users are also able to access normal (non-TOR) websites and hosts in a similar manner.
An example to further clarify the concept: let’s say you want to send a picture to your friend over the internet, without disclosing your location/IP address.
So when you send the picture, what happens is that your phone, i.e. the Client, creates a data packet that comprises two parts: Data Payload and Header. Data Payload contains your message, in this case the picture, while the header carries all the information about the Client’s (your) and recipient’s IP address.
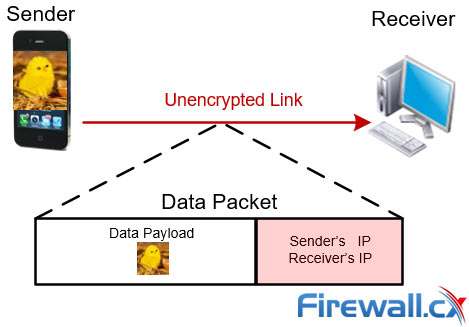
Figure 3. Data transfer process without TOR exposes the sender’s & receiver’s IP address
Now, if you are not using TOR, this data packet directly reaches out to your friend (receiver). And, if your friend is an IT person, it will be fairly easy for him to figure out your IP address from the header and thus the location, which you wanted kept private.
However, with TOR, a different scene would play altogether.
With TOR, this data packet from the Client (sender), instead of reaching out directly to the Server (receiver), passes through several proxy servers in between. At each layer, the data packet reveals only as much information as is required to reach the next layer. Thus at each step the data packet unfolds information only about the next node, not about the forthcoming layers. The layers unfold one at a time, to reach the destination Server safely without him knowing your location:
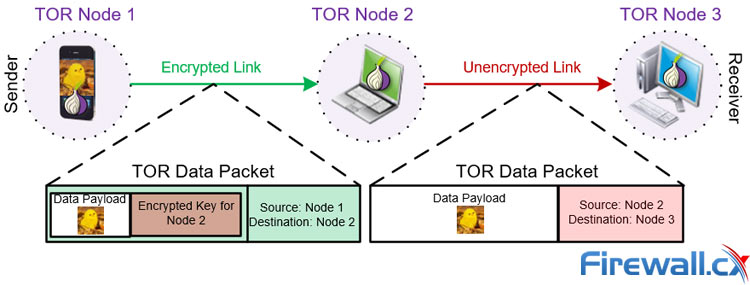
Data transfer via the TOR network guarantees encryption and privacy
This way TOR doesn’t necessarily erase the footprints of the client but makes it less likely for the server to trace the client’s details. TOR’s strength lies in the number of proxies in the relay. These proxies are servers operated by volunteers connected to the TOR Project. So, the more volunteers the stronger the security network of TOR.
How VPNs Work (Virtual Private Networks)
Our comprehensive Guide to VPNs covers everything you’ll need to know about VPNs however we’ll provide an overview as well to make it easier to compare VPNs with TOR.
VPNs were created in to provide security to users sending data across a public network such as the internet.
Unlike TOR, VPN employs the Client-Server technology with a single hop relay. The intermediate node in the relay is called a VPN Server. A VPN Server acts as a proxy server to transmit data between the client and the internet as shown in the diagram below:
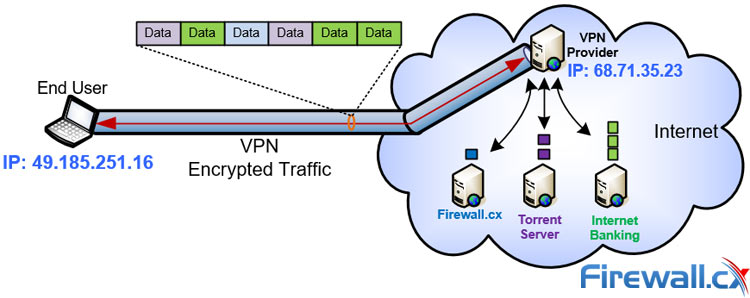
Securely accessing the internet via a VPN Service Provider
A VPN Client is usually a computer, laptop or mobile phone with VPN software installed and a VPN Server is generally located at the organization’s office, in the case of a company-private VPN, or at a large data center in the case of a VPN Service Provider.
Only a VPN Client with the right settings (credentials and VPN Server address) can connect to the VPN Server. A VPN Server combines the hardware and software technologies necessary to host and deliver VPN services over the network. The moment a VPN Client sends a message to connect to the VPN Server, the server will request the client to authenticate. If the credentials are correct, the client connects to the server creating an encrypted tunnel between the two endpoints. Data flowing between the client and VPN server is encrypted, thus preserving the client’s anonymity during the communication.
VPN Service Providers allow you, the client, to connect to their VPN Servers located around the world via VPN, thus encrypting your internet traffic to make it almost impossible to monitor and track.
When the client (you) tries to access a resource on the internet, e.g. a website, instead of sending the request directly to the website, which would reveal your IP address and allow the ISP to monitor the session, the request is encrypted and sent to the VPN server. The VPN Server then reaches out to the website by forwarding the client’s request, however, the website sees that the request came from the VPN Server, not the client. This hides the end client completely making it impossible to track where the request originated.
The same process applies whether you are torrenting, sending-receiving emails, browsing websites or downloading content from the internet. One key-point to remember here is that when you authenticate in order to access a service, e.g. email, you are in fact disclosing your identity to the end server, however, your location is not revealed.
VPN Protocols
VPNs offer different layers of security depending on the encryption protocol. There is a number of VPN encryption protocols used today by VPN Providers and each has its advantages and disadvantages.
Selecting the best VPN Protocol for your mobile device or computer can be a daunting task especially for new users but it can be simplified when you understand a few basic concepts.
While our upcoming extensive guide to the Best VPN Protocol will cover this in great depth, let’s take a quick look at the most commonly used VPN protocols:
PPTP - Point to Point Tunnelling Protocol
PPTP stands for Point to Point Tunnelling Protocol. Developed by Microsoft decades ago, PPTP is supported by most operating systems including Windows, MAC, Mobile OS and Android. It is fast but at the cost of weak encryption. This means that a PPTP VPN can be easily cracked and shouldn’t be used when sending or transmitting sensitive information. PPTP also seems to works well on Wi-Fi hotspots.
L2TP/IPsec – Layer 2 Tunnel Protocol / IPSecurity
Layer 2 Tunnelling Protocol and IP Security offers good encryption resulting in heavy CPU processing, thereby decreasing its speed. L2TP is a much better replacement for the older PPTP but users need to be aware that the increased security/encryption comes at the cost of speed.
SSTP – Secure Sockets Tunnelling Protocol
The SSTP protocol is considered a very reliable and easy-to-use protocol. Its advantages include that it will pass through most firewalls, is difficult to block and is natively supported by all Windows platforms from Windows Vista SP1 onwards. Its encryption capabilities are considered moderate and the same applies to its speeds.
OpenVPN
OpenVPN is a newer VPN protocol created and supported by the open-source community. OpenVPN offers the highest level of encryption but, at the same time, is the most flexible protocol available thanks to its ability to utilize the TCP or UDP protocol. It requires a VPN Client and is supported by Windows, Mac and Android Operating Systems. OpenVPN is the preferred VPN protocol as it combines flexibility, encryption and speed. OpenVPN is also the preferred VPN Protocol used by all VPN Providers in our extensive Best VPN review.
When to use TOR
This ‘Dark Onion Science’ prevails. Over 25% of Internet users use TOR daily. That makes the comparison of TOR VPN even more interesting in many ways.
Here are a few examples where TOR can be used, in general:
By Social Workers, Activists & Journalists without Borders
To avoid media censorships while working with sensitive information or secret projects
By Parents & Households
To prevent digital stalking, image abuse and cyber spying.
Law Enforcement Agencies and Military on Undercover Missions
To stay away from the media eye and government hacking/monitoring groups
By Bloggers, Job Professionals or Normal People
To increase their privacy over internet or to simply avoid cyber theft.
Hidden Internet Services
This is a very interesting application of TOR. Hidden Services mean that a client hosts its website or service without disclosing its identity. Here, TOR provides anonymity to websites and other servers. These kinds of websites don’t even have a regular URL address, e.g. www.firewall.cx, instead TOR shows a randomly generated 16-digit code as its domain name. So, if there’s a TOR user trying to access a hidden services website, his browser will identify the domain via public keys and introduction points stored in a distributed hash table in the TOR Network. However, if the user doesn’t have TOR installed, there is no way of accessing these hidden internet services.
Apart from the above mentioned applications, the most common applications that use anonymous internet via TOR are Internet Relay Chat (IRC), Instant Messaging (IM) and World Wide Web (www) browsing.
When to use VPN (VPN Service Provider)
It is without doubt that VPNs are far more popular than TOR, however, let’s take a quick look at the common reasons people prefer to use VPNs:
To Access Restricted Websites – Bypassing Geo-Location Restrictions
Netflix or Hulu are the most common examples here. Users who want to access their Netflix or similar account cannot do so when travelling overseas. With a VPN service you can connect to one of your provider’s VPN servers and access the online content as if you were located in that country – effectively bypassing any geo-location restriction. Another example is trying to access a domain or website that is blocked from your country, e.g. accessing facebook from China.
Our Best VPN Service Provider comparison also includes VPN Providers that provide access to Netflix and Hulu.
For Downloading via Torrents & Avoiding Bandwidth Throttling
Torrent downloading implies downloading illegal or pirated software, however, this is not 100% true. Many vendors offer legal downloading of their software via Torrents. ISPs unfortunately tend to “unofficially” throttle user bandwidth when they detect Torrent traffic. Using a VPN, all traffic is encrypted therefore there is no bandwidth throttling by the ISP.
Secure Mobile Device Internet Data
Users tend to use their mobile devices today to access all sorts of content while commuting to work, casually surfing the internet or checking their bank accounts. No matter what the activity, with a VPN Service Provider that supports mobile clients users are sure that all their data and activities are encrypted and protected.
Authenticating to Websites or Private Resources (Email, Internet Banking etc)
When you are signing in with your credentials to an online resource, it’s always better to protect yourself from crawler bots and cyber fraud artists. A VPN will ensure your traffic is encrypted so anyone monitoring your traffic (e.g. at a public hotspot) won’t be able to see the data that is being transferred.
On Travel or Business
On the road, or at a hotel, VPNs are just the right thing if you travel. VPNs help bypass any firewall restrictions providing full internet access no matter where you might be.
TOR vs VPN: TOR Advantages and Disadvantages
Advantages Include:
High Level of Anonymity
TOR gives you such a high level of anonymity it is almost impossible for a website to track you. The Onion Routing technology leaves no way through which your pathway can be tracked.
Free To Use
TOR is completely free!
Reliable
Unlike VPNs where your privacy depends on how trustworthy your VPN Service Provider is, TOR is absolutely reliable. Owing to the randomly selected network of nodes, no one knows about the other and thus there is no concern about reliability here.
Disadvantages include:
Non Traceable Exit Nodes
Since the data packets at exit nodes are decrypted, whoever is running the exit node can misuse, leak or manipulate the information sent by you.
Blocked Relays
Some relays are cleverly tracked and blocked by the ISPs. This can cause real difficulties in connection between users.
Slow Processing
Since the data packets route through a number of proxy servers, the connection can be slow. This can cause irritation while watching or downloading large files like videos.
Unsuitable for Data-metered Plans
If your internet plan includes a specific amount of data, e.g. 10GB/month, TOR can become a big problem as your bandwidth will be used by other TOR nodes to transfer their data. This will result in quickly depleting your monthly data allowance.
TOR vs VPN: VPN Advantages and Disadvantages
Advantages include:
Variety of Security Encryption Levels Depending on your Online Activities
Whether you need to access your email, download torrents, stream videos, perform internet banking transactions or anything else, you can easily select the encryption level and help speed up the connection, or heavily secure it.
Compatible with Almost Any Device
VPNs are compatible with almost any iPhone and android device, Windows operating system or MAC OS. Tablets including iPad are also capable of running VPN client software. This makes it very easy for novice users to install a VPN client and securely connect to the internet.
Fast Speed
From multiple to just one proxy/node automatically increases the speed of data transmission in VPNs compared to that of TOR. This makes it highly suitable for torrenting or downloading large files. VPNs also allow you to select the server to which you connect - an option that considerably speeds up the overall download speeds one can acheive via a VPN connection.
Easy Availability, Installation and Support
Unlike TOR, VPNs are easily allowed and operated by commercial companies that ensure fast and good quality services for their clients. If you have any problem there is almost always someone at the support desk that can help you via email or live chat.
Ability to bypass Firewall Restrictions
With the use of a VPN you can pretty much bypass any protocol or URL restriction in place, effectively opening the internet to your device.
Disadvantages:
Despite the many advantages of VPNs, there still remains a fly in the ointment. Since information just passes in and out of the tunnel, companies operating the VPNs have access this information. The best way to protect yourself from your VPN Provider is to ensure they have a no-log policy which means they do not log any data or user activity on their VPN Servers. Our Beginners Guide to VPNs article provides all the necessary information new or existing VPN users need, including security concerns and VPN features that help enhance your protection.
TOR vs VPN: Summary
So, the comparison comes out like this: use TOR, or use VPN, each one of them has its own pros and cons. Both are good as long as you understand your needs, the level of anonymity you want over the Internet and at what price. It can cost your time and money. If you want to secure your Internet privacy, TOR is a great option if you have a fast and unmetered (unlimited bandwidth) connection. If you need fast downloading speeds, to bypass any firewall restrictions or just greater flexibility and better control of how you consume your monthly data plan, then a VPN is your solution.
In the comparison of TOR vs VPN, the user is the winner. And to the hackers and government agencies all we can say is, no snooping around!
Your IP address:
52.15.169.97
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!













