Suggested Articles:
Palo Alto Networks
How to Fix Palo Alto Firewall “Error: Image File…
Keeping your Palo Alto Firewall up to date with the latest PAN-OS software updates is an important step to ensure your organization is protected agai…
SASE & SD-WAN Networks
How To Secure Your SD-WAN. Comparing DIY, Managed…
With so much enterprise network traffic now destined for the cloud, backhauling traffic across an expensive MPLS connection to a data center to apply…
SASE & SD-WAN Networks
MPLS vs. SD-WAN vs. Internet vs. Cloud Network. C…
The Wide Area Network (WAN) is the backbone of the business. It ties together the remote locations, headquarters and data centers into an integrated…
SASE & SD-WAN Networks
WAN Optimization vs SD WAN Networks. Today’s Chal…
Enterprises have been successfully running WAN optimization appliances at their many distributed sites for years. The devices have done a good job of…
Featured Subcategories:
SASE & SD-WAN Articles:
MPLS vs. SD-WAN vs. Internet vs. Cloud Network. C…
The Wide Area Network (WAN) is the backbone of the business. It ties together the remote locations, headquarters and data centers into an integrated…
Key Features of a True Cloud-Native SASE Service…
Secure Access Service Edge (SASE) is an architecture widely regarded as the future of enterprise networking and security. In previous articles we tal…
Understanding Secure Access Service Edge (SASE) a…
Software Defined Wide Area Networking (SD-WAN) is changing the way that businesses connect to the cloud. With SD-WAN, organizations can move away fro…
Complete Guide to SD-WAN. Technology Benefits, SD…
SD-WAN is the answer for enterprises and organizations seeking to consolidate network functions and services while at the same time simplify their WA…
Your IP address:
216.73.216.176
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!
Palo Alto Networks
How to Register a Palo Alto Firewall and Activate Supp…
This article explains how to register and activate your Palo Alto Firewall Appliance to obtain technical support, RMA hardware replacement, product update…
Palo Alto Networks
Palo Alto Firewall Configuration Options. Tap Mode, Vi…
Our previous article explained how Palo Alto Firewalls make use of Security Zones to process and enforce security policies. This article will explain the…
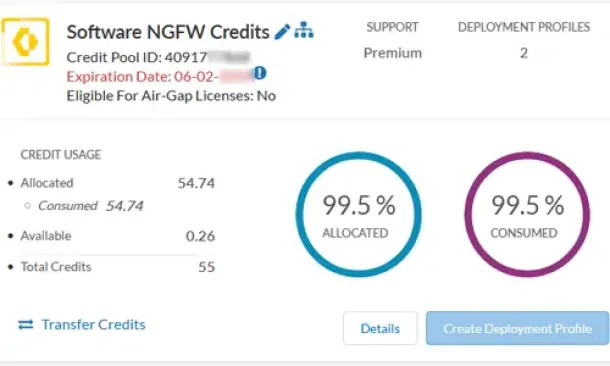
Palo Alto Networks
The Ultimate Guide to Palo Alto Networks Software NGFW…
Discover the ins and outs of using Palo Alto Networks’ Software NGFW (Flex) credits to seamlessly renew your cloud-based or virtualized software NGFW devi…
Palo Alto Networks
Palo Alto Firewalls Security Zones – Tap Zone, Virtual…
Palo Alto Networks Next-Generation Firewalls rely on the concept of security zones in order to apply security policies. This means that access lists (fire…
Popular Topics
Windows Servers
The Importance of a Hyper-V & VMware Server Backup Too…
Using Hyper-V Server virtualization technology, you can virtualize your physical environment to reduce the cost of physical hardware. As part of IT best p…
Cisco Wireless
Cisco Wireless Controllers (WLC) Datasheets Available…
We would like to inform our readers that Firewall.cx has just made available as a free download all of Cisco's Wireless Controller Datasheets.
The datash…
Network Protocol Analyzers
How to Detect SYN Flood Attacks with Capsa Network Pro…
This article explains how to detect a SYN Flood Attack using an advanced protocol analyser like Colasoft Capsa. We’ll show you how to identify and inspect…
Windows Servers
Windows 2003 DHCP Server Installation & Configuration
DHCP (Dynamic Host Configuration Protocol) is a protocol that allows clients on a network to request network configuration settings from a server running…

















