Articles
To read the articles in this section, simply click on the article title or read button on the far right (if visible).
Use the below filters to customise the number of articles displayed or search for specific title topics/keywords.
| Articles | |
|---|---|
| Read | |
| Read | |
|
Articles:
Direct Cable Connection
| Read |
| Read | |
| Read | |
| Read | |
|
Articles:
Important Direct Cable Connection Notes
| Read |
| Read | |
|
Articles:
100Base-(T) TX/T4/FX - Ethernet
| Read |
|
Articles:
10Base-T/2/5/F/35 - Ethernet
| Read |
| Read | |
|
Articles:
Straight Thru UTP Cables
| Read |
| Read | |
Suggested Articles:
Network Address Translation - NAT
Static NAT - Part 1
Static NAT (also called inbound mapping) is the first mode we're going to talk about and also happens to be the most uncommon between smaller network…
Network Fundamentals
Network Broadcast
The term "Broadcast" is used very frequently in the networking world . You will see it in most networking books and articles, or see it happening on…
Network Protocols
Introduction To Protocols
In the networking and communications area, a protocol is the formal specification that defines the procedures that must be followed when transmitting…
ICMP Protocol
ICMP Protocol - Part 5: Source Quench Message Ana…
The ICMP - Source Quench message is one that can be generated by either a gateway or host. You won't see any such message pop up on your workstation…
Featured Subcategories:
Netflow Articles:
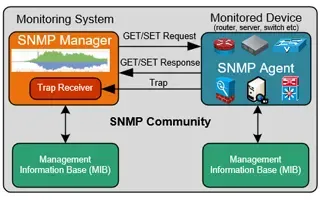
Netflow vs SNMP. Two Different Approaches to Netw…
SNMP (Simple Network Management Protocol) and Netflow are both popular protocols with admins, prized for their ability to give visibility over the ne…
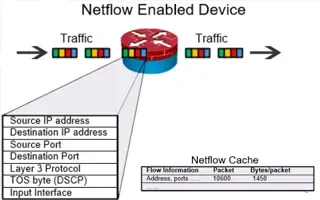
Complete Guide to Netflow: How Netflow & its Comp…
This article will cover the basics of Netflow, including its use cases, Netflow supported devices, Netflow history, and variants. We’ll also dive int…

Netflow: Monitor Bandwidth & Network Utilization…
Monitoring network traffic & bandwidth usage via Netflow is mandatory for any type and size network. Gaining visibility into user traffic, applic…
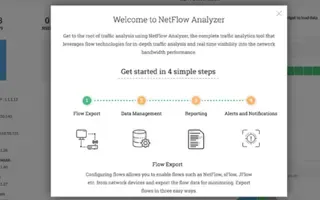
NetFlow Analyzer: Free Download, Step-by-Step Ins…
In our previous article we explained how a Netflow Analyzer can help you gain visibility into your user traffic, application traffic and data flows w…
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!
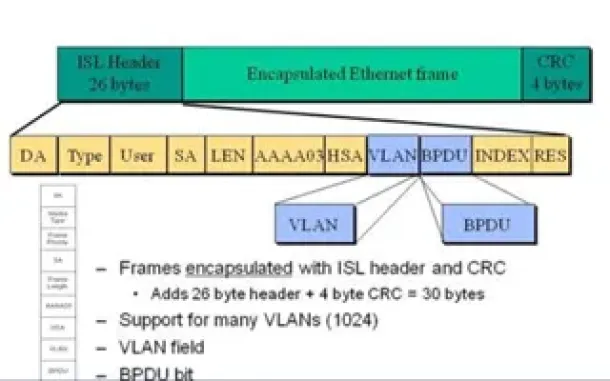
VLAN Networks
VLAN InterSwitch Link (ISL) Protocol Analysis
Deciding whether to use ISL or IEEE 802.1q to power your trunk links can be quite confusing if you cannot identify the advantages and disadvantages of eac…

VLAN Networks
VLAN Security - Making the Most of VLANs
It's easy to see why virtual LANs have become extremely popular on networks of all sizes. In practical terms, multiple VLANs are pretty much the same as h…

VLAN Networks
Static VLANs
VLANs are usually created by the network administrator, assigning each port of every switch to a VLAN. Depending on the network infrastructure and securit…

VLAN Networks
VTP Pruning
VTP (VLAN Trunking Protocol) pruning is a feature that is used in Cisco switches to reduce unnecessary traffic in VLAN (Virtual Local Area Network) trunks…
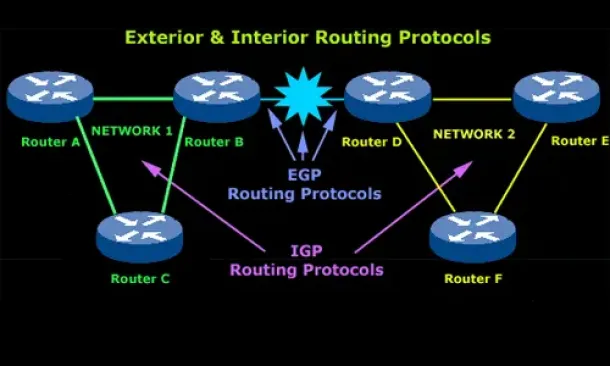
Routing
Introduction to Routing Protocols
Distance Vector, Link State RIP, IGRP, EIGRP, OSPF
Routing protocols were created for routers. These protocols have been designed to allow the exchange…
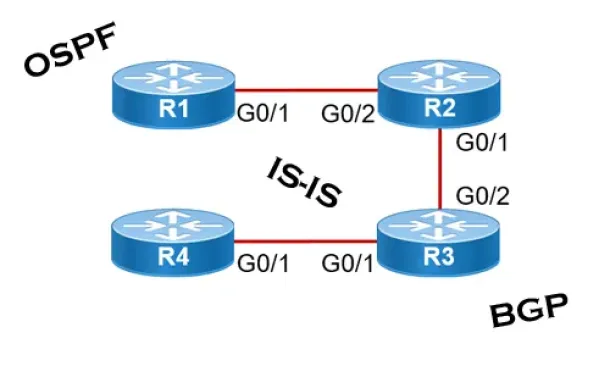
Routing
Link State Routing Protocols
Link State routing protocols do not view networks in terms of adjacent routers and hop counts, but they build a comprehensive view of the overall network…
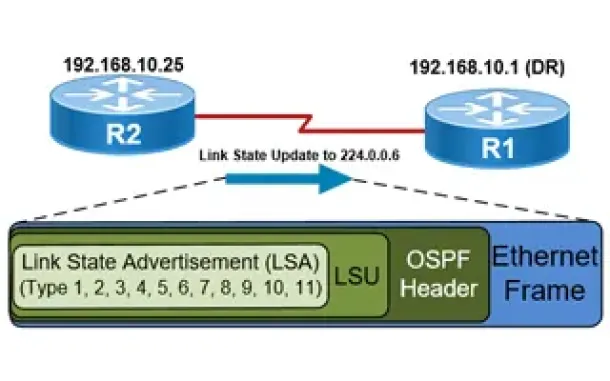
Routing
OSPF - Part 5: Analysis of OSPF Link State Update (LSU…
This article explains how OSPF uses Link State Advertisement (LSA) to exchange information about the network topology between routers. When a router recei…
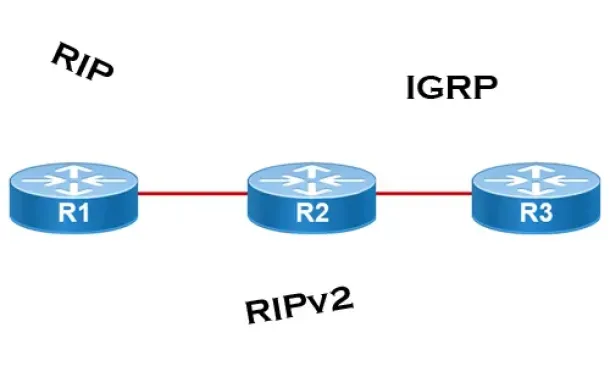
Routing
Distance Vector Routing Protocols
Distance Vector routing protocols use frequent broadcasts (255.255.255.255 or FF:FF:FF:FF) of their entire routing table every 30 sec. on all their interf…
Cisco Routers
Understanding MPLS IP VPNs, Security Attacks and VPN E…
What Are MPLS Networks?
Multi-Protocol Label Switching (MPLS) networks are the next-generation of networks designed to allow customers create end-to-end…
SASE & SD-WAN Networks
Key Features of a True Cloud-Native SASE Service. Sett…
Secure Access Service Edge (SASE) is an architecture widely regarded as the future of enterprise networking and security. In previous articles we talked a…
SASE & SD-WAN Networks
Converged SASE Backbone – How Leading SASE Provider, C…
Global connectivity is top of mind for many IT teams at organizations of all sizes. We are currently in the middle of a dramatic shift in business and tec…
SASE & SD-WAN Networks
Configuring A SASE Unified Network: Data centers, Remo…
This article explores the need for Secure Access Service Edge (SASE) in today’s organizations. We show how one of the most advanced SASE platforms availab…



















