Articles
To read the articles in this section, simply click on the article title or read button on the far right (if visible).
Use the below filters to customise the number of articles displayed or search for specific title topics/keywords.
| Articles | |
|---|---|
| Read | |
| Read | |
|
Articles:
Website History
| Read |
|
Articles:
Site Awards
| Read |
|
Articles:
Meet The Firewall.cx Team!
| Read |
Suggested Articles:

OpManager - Network Monitoring & Management
Elevate your network management: Maximizing effic…
As technology evolves, so do our networks. Today's sprawling network infrastructures are intricate ecosystems, demanding more from IT teams than ever…
Network Protocol Analyzers
Introducing Colasoft Unified Performance Manageme…
Colasoft Unified Performance Management (UPM) is a business-oriented network performance management system, which analyzes network performance, quali…

OpManager - Network Monitoring & Management
Optimizing Cisco Router Performance: Best Practic…
Effective monitoring and management of Cisco routers and network devices are essential for ensuring a robust and efficient network infrastructure. In…
Network Protocol Analyzers
How to Detect SYN Flood Attacks with Capsa Networ…
This article explains how to detect a SYN Flood Attack using an advanced protocol analyser like Colasoft Capsa. We’ll show you how to identify and in…
Featured Subcategories:
WireShark Articles:
How to Use Multi-Segment Analysis to Troubleshoot…
Troubleshooting network problems can be a very intensive and challenging process. Intermittent network problems are even more difficult to troublesho…
Advanced Network Protocol Analyzer Review: Colaso…
Firewall.cx has covered Colasoft Capsa several times in the past, but its constant improvements make it well worth revisiting. Since the last review…
How To Detect ARP Attacks & ARP Flooding With Col…
ARP attacks and ARP flooding are common problems small and large networks are faced with. ARP attacks target specific hosts by using their MAC addres…
How to Perform TCP SYN Flood DoS Attack & Detect…
This article will help you understand TCP SYN Flood Attacks, show how to perform a SYN Flood Attack (DoS attack) using Kali Linux & hping3 and co…
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!
Palo Alto Networks
How to Fix Palo Alto Firewall “Error: Image File Authe…
Keeping your Palo Alto Firewall up to date with the latest PAN-OS software updates is an important step to ensure your organization is protected against t…
Palo Alto Networks
Palo Alto Firewall Application-based Policy Enforcemen…
Our previous article examined the benefits of Palo Alto Networks Firewall Single Pass Parallel Processing (SP3) architecture and how its combine with the…

Palo Alto Networks
Configuring QoS on Palo Alto Firewalls: Class-based Po…
This article’s purpose is to help you quickly master Palo Alto QoS concepts and learn to configure QoS on Palo Alto Firewalls in a simple and efficient wa…
Palo Alto Networks
Introduction to Palo Alto Next-Generation Network Fire…
During the past decade, we’ve seen the global IT security market flooded with new network security and firewall security appliances. New vendors emerging…
Windows Servers
Windows Server 2016 Licensing Made Easy – Understand Y…
This article describes the new Windows Server 2016 Licensing model (per-core licensing) Microsoft has implemented for its new server-based operating syste…
Windows Servers
How to Install and Configure Windows 2012 DNS Server R…
Our previous article covered introduction to the Domain Name System (DNS) and explained the importance of the DNS Server role within the network infrastru…
Windows Servers
Creating a Virtual Machine in Windows Hyper-V. Configu…
Our previous articles covered basic concepts of Virtualization along with the installation and monitoring of Windows 2012 Hyper-V. This article takes the…
Windows Servers
Configuring Windows Server Roaming Profiles
Windows roaming profiles allow the mobile users of a company to always work with their personal settings from any network computer in a domain. Roaming pr…
Popular Topics
Routing
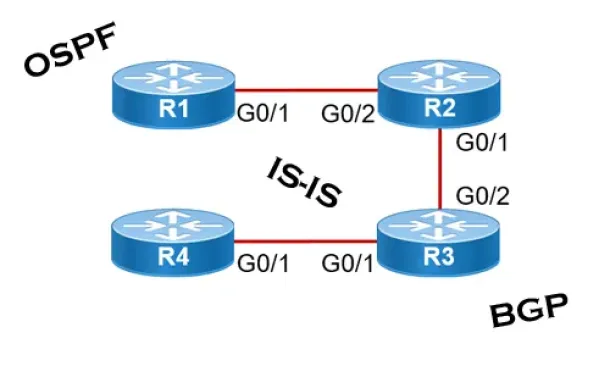
Link State Routing Protocols
Link State routing protocols do not view networks in terms of adjacent routers and hop counts, but they build a comprehensive view of the overall network…
Windows Servers
Free Webinar & eBook on Microsoft Licensing for Virtua…
Microsoft Licensing for Virtual environments can become a very complicated topic, especially with all the misconceptions and false information out there…

VLAN Networks
VLANs - Access & Trunk Links
If you've read our previous article The VLAN Concept - Introduction to VLANs then you should feel comfortable with terms such as 'VLAN', 'Stati…
Routing
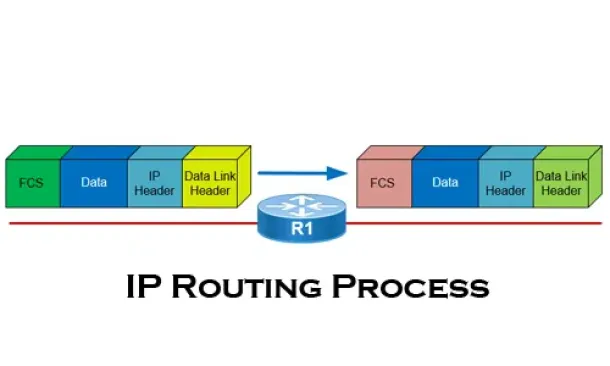
The IP Routing Process - Step-by-Step Analysis
We are going to analyse what happens when routing occurs on a network (IP routing process). When I was new to the networking area, I thought that all you…
Cisco CallManager-CCME
Secure CallManager Express Communications - Encrypted…
In this article we discuss about the security and encryption of Cisco Unified Communications Manager Express (CUCME) which is an integral part of Cisco UC…

Cisco Data Center (Nexus/UCS)
Nexus 7000/7700 Software Upgrade via ISSU. Complete Up…
This article shows how to perform an ISSU (In-Service Software Upgrade) on a Nexus Data Center switch (7000 and 7700 models) and avoid service and network…
Cisco Switches
Configuring SPAN On Cisco Catalyst Switches - Monitor…
Being able to monitor your network traffic is essential when it comes to troubleshooting problems, performing a security audit or even casually checking y…
Cisco Services & Technologies
Introduction to Cisco VIRL – Virtual Internet Routing…
One of the most difficult things for people who are starting out in a networking career is getting their hands on the equipment. Whether you are studying…



















