VPN Hotspot - How to Stay Safe on Public & Guest WiFi Networks
Is Guest WiFi Safe?
 It’s hard to go to a pub, café, or hotel these days without running into public or guest WiFi. In many cases, an internet connection can feel like a necessity – keeping up with work or personal emails, arranging plans with friends, checking social media. Connecting is usually as easy as entering an email address, filling out a survey, or entering a code on a receipt.
It’s hard to go to a pub, café, or hotel these days without running into public or guest WiFi. In many cases, an internet connection can feel like a necessity – keeping up with work or personal emails, arranging plans with friends, checking social media. Connecting is usually as easy as entering an email address, filling out a survey, or entering a code on a receipt.
It's an easy trap to fall into. Cellular data is expensive. In the US, 500 MB of pre-paid data costs an average of $85 US. If your contract doesn’t have a large data allowance, free WiFi is a godsend. However, that convenience comes with considerable risk to your privacy and security. If you’re not using a VPN at a public hotspot, you’re opening yourself up to all kind of malicious attacks and data interceptions such as sslstrip man-in-the-middle attack (analysed below), online activity monitoring, computer hijacking, restricted online browsing and many more serious security threats.
Public - Guest WiFi Security Risks
The biggest misconception about open WiFi is that it offers the same protection as your home network. That couldn’t be further from the truth. The annoying password on your home network does much more than keep people from connecting. It encrypts your data so that those on the outside have trouble looking in.
By nature, guest WiFi has no password. In most cases, that means no encryption. With a simple tool, anyone on the network can see which websites you’re visiting. In some cases, they can even intercept the emails you send, the files on your computer, and passwords. It doesn’t matter if you’re at a high-security airport or the coffee shop down the road.
Even when an attacker isn’t around, you’re putting trust in the security of everyone else on the network. You may have the latest version of Windows 10, but the person next to you could have no security knowledge. Some forms of malware attempt to spread themselves to other people on the network, and the user probably doesn’t even know about it.
Common WiFi Attacks used at Internet Hotspots
![]() Thankfully, wifi snooping is on the decrease thanks to SSL encryption. This web standard is spreading across all the most popular sites, and you’ll notice it by the HTTPS icon in your browser (as seen in the image on the left). It means that while someone can see the url you’re on, they can’t see your emails or the password you just typed in. Unfortunately, this won’t stop someone resourceful. In fact, SSL can be bypassed with a single method.
Thankfully, wifi snooping is on the decrease thanks to SSL encryption. This web standard is spreading across all the most popular sites, and you’ll notice it by the HTTPS icon in your browser (as seen in the image on the left). It means that while someone can see the url you’re on, they can’t see your emails or the password you just typed in. Unfortunately, this won’t stop someone resourceful. In fact, SSL can be bypassed with a single method.
In 2009, security expert Moxie Marlinspike introduced sslstrip. By routing a victim’s connection through their own machine, an attacker can redirect them to the HTTP version of the page. The browser won’t even detect this and the victim has no idea what’s going on.
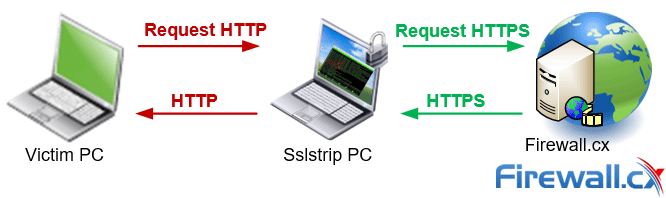
Representation of how an sslstrip wifi attack works
The vulnerability comes from the fact that most users don’t type in “https://” at the beginning of every url. This means that when they first connect to the site, it’s HTTP. Most websites will then redirect users to an HTTPS version, but ssltrip steps in and sends back HTTP instead. The hacker can then view all the user’s requests in plaintext, collecting whatever information he likes.
Though attackers often need specialist software and some technical knowledge, packages such as WiFi Pineapple can make so-called “man-in-the-middle” attacks relatively simple. In a few clicks, users can pretend to be a public network, routing traffic through them rather than to the router. From there, the attacker can force the user to visit websites with malware, install key loggers, and plenty of other shady things. It’s not too difficult, and with the aid of YouTube, a seven-year-old did it in eleven minutes.
In some cases, attackers don’t even need any experience to view your information. Oftentimes, users connecting to hotel WiFi forget to change Windows sharing settings. This makes it easy for anybody to view your shared files with no hacking required. Sometimes this isn’t even password protected, making it child’s play.
However, there are also tools to make more complex processes simple. In 2010, a simple browser extension called FireSheep was released. The tool lets users catch browsing cookies from any website that doesn’t use HTTPS. Though many major websites such as Facebook and Gmail are protected, smaller sites often use HTTP, and many users have the same password for multiple sites.
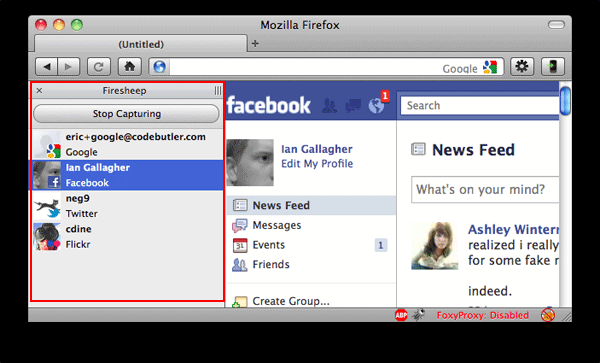
Firesheep Firefox extension in action
Other tools let you do the same from an Android phone or other devices. And that’s assuming you’re connecting to the right network at all. A common method of attack is to set up a fake network, or honeypot. To the untrained eye, it won’t look out of place. Often, they will make sense in the context, named Starbucks WiFi, for example. In fact, an attacker owns it, and is logging everything you do. Our article configuring Windows 8 / 8.1 as an access point is a good example that shows just how easy it is to configure your workstation into a honeypot.
Hotel Hotspots - 277 Hotels Wordwide with Major Security Flaw
 Hotels are one of the most vulnerable places for such attacks. They often have hundreds of people connected to the network at a time and hackers can stay in their rooms, undetected by anyone. Most hotels don’t have good security, and standardization means that many have the same, vulnerable hardware.
Hotels are one of the most vulnerable places for such attacks. They often have hundreds of people connected to the network at a time and hackers can stay in their rooms, undetected by anyone. Most hotels don’t have good security, and standardization means that many have the same, vulnerable hardware.
In 2015, for example, 277 hotels worldwide were found to be using ANTlab’s InnGate device. It’s used by much of the hotel industry to set up guest WiFi, including most of the top 10 chains. Unfortunately, it has a major security flaw, enabling hackers to gain access to users’ data, and sometimes even credit card data held by the hotel.
ANTlab’s InnGate WiFi client login page
Thankfully, ANTlab has since produced a software update to solve the issue, but it must be installed manually, and there's no way to tell if the hotel has applied the fix. This leaves a situation where you can never truly trust hotel networks.
Business executives should be particularly cautious. Russian security firm Kaspersky Lab discovered in 2014 that hackers were running a malware campaign code-named DarkHotel which was targeting business leaders at hotels in Asia. DarkHotel is a targeted spear-phishing spyware and malware-spreading campaign that appears to be selectively attacking business hotel visitors through the hotel's in-house WiFi network. When logging into the WiFi, a page asked them to download the latest version of Flash Player, Messenger or other software. The software was legitimate but malware piggybacked on the install, stealing valuable data.
Business Guest WiFi Security
Businesses’ own networks can also be a significant target. Though many private corporate networks invest in security, guest internet is often open and unsecure. This puts clients or visitors at risk, and can also endanger employees using the wrong network. Unfortunately, a number of solutions fail to offer proper network encryption.
This opens users up to the dangers mentioned before, such as man-in-the-middle attacks. Browsing is open to snooping and could result in lost passwords, malware and more. Many routers try to circumvent the risk slightly by implementing a portal page, but this can lead to further problems.
In the case of some Linksys and Belkin routers, the page uses HTTP rather than HTTPS. That means that anyone sniffing WiFi traffic nearby can discover a password in plaintext when its typed in. Naturally, that gives them access to the network anyway, and possibly other logins if the password is re-used.
In addition, some guest networks still use Wired Equivalent Privacy (WEP) for protection. WEP is outdated and easily circumvented, now succeeded by WPA and WPA2. WEP can now be easily circumvented, and in 2011 three Seattle-based hackers stole over $750,000 from local businesses using this method.
The three drove around with networking tools, looking for unsecure or accessible wireless networks and stealing data. Employee social security numbers, email addresses, company credit card numbers and other information was then sold on to third parties.
Staying Safe on Public Wi-Fi Networks & Internet Hotspots
Fortunately, there are several ways you can stay safe on public WiFi and protect both your information and clients. Firstly, check that you’re connecting to the right network. It’s stupidly easy for someone to create their own hotspot called “Hotel WiFi” and log all your connections. It always pays to ask an employee which WiFi you should connect to.
Before you connect, check your sharing settings. This will stop the average joe from seeing all your shared documents with a click. You can view them easily in Windows via Network and Internet> Change advanced sharing settings.
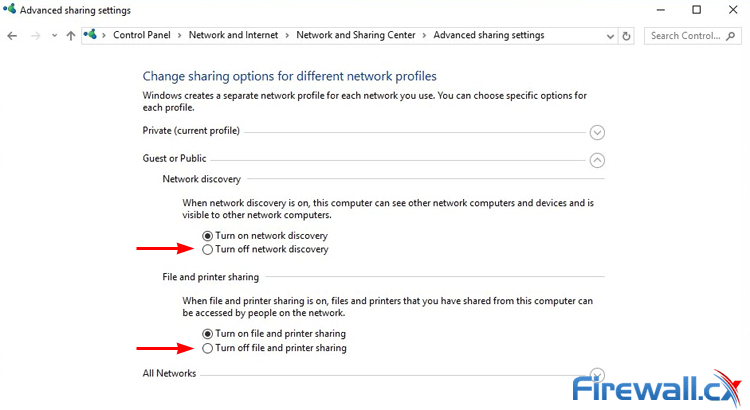
Disabling Network Discovery and File Printer Sharing when connected to Public wifi
You’ll want to disable both Network Discovery and File and printer sharing. This will make it harder for people to access all your documents. In OSX you’ll want to go to System Preferences> Sharing and untick all the boxes there.
While you’re at it, you may as well make sure your Firewall is enabled. Often, users can disable the setting due to annoying software asking for permissions. However, having the Firewall enabled is essential on guest internet. Though it’s not infallible, it will make it harder for attackers to poke around in your PC.
In Windows, you can simply type in firewall, and then click turn Windows Firewall on or off on the left side of the control panel. OSX is equally simple, and both let you set exceptions for public and private networks.
Users should also be keeping both their operating system and applications up to date. This is especially important for browsers and plugins like Flash and Java. Not only will this reduce the vulnerabilities on your computer, you won’t be fooled by the bogus update messages mentioned earlier.
Speaking of browsers, try to make sure you’re using HTTPS where possible. A simple way is to visit popular websites in HTTPS on a secure network and then bookmark them. When you’re in public, only use that bookmark to access your logon. Alternatively, extensions such as HTTPS Everywhere will force Chrome, Opera, or Firefox to use SSL encryption on all webpages that support it. This will protect you against sslstrip and is much more user-friendly.
If someone still manages to sniff your password, two-factor authentication can be a lifesaver. Most major email providers such as Gmail and Hotmail provide this service, as does Facebook. Essentially, it makes you enter a time-sensitive passphrase when connecting from a new device. This can be delivered via text, a mobile app, or email. The extra step can be enough to turn away most hackers.
However, the only way you can be 100% sure is to not visit sensitive websites at all. Generally, it’s a bad idea to go on PayPal, online banking, or other such websites on guest WiFi. You can never be confident you’re truly safe, and that applies to mobile banking too. When you’re done browsing, you should consider disconnecting from WiFi or turning off your computer. The longer your PC is open and on the network, the longer an attacker has to find vulnerabilities.
All of these steps will help a lot with creating a secure public WiFi experience. However, the unfortunate truth is that a determined attacker can still bypass these measures. To significantly increase your safety, you’ll want to invest in a VPN Service Provider. While selecting a VPN Provider can be a time-consuming process our Best VPN services comparison will help considerably in the process of selection.
Secure WiFi Access and Identity Protection with VPN Service Providers
A Virtual Private Network is exactly what it sounds like. Simply, a VPN allows you to make a secure connection to a server over the internet. All your traffic goes through that server, with very strong encryption that makes it almost impossible to snoop. When you connect to an unprotected WiFi network, attackers will just see a load of random characters. Trying to circumvent that is simply not worth their time.
With a VPN Provider your PC creates a tunnel to send your data over the internet. Every piece of data sent over the internet is in chunks called packets. Each packet has part of the data, as well as other information like the protocol (HTTP/HTTPS) and the user’s IP address. When you connect to a VPN, that packet is sent inside another packet. As you would expect, the outer packet provides security and keeps the information from prying eyes.
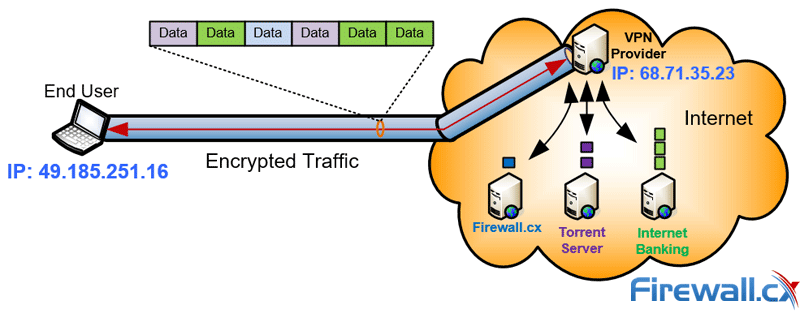
With a VPN Provider all internet traffic is encrypted and secure
However, as mentioned before, data is also encrypted. How exactly this is achieved depends on the security protocol of the VPN client. Using the Best VPN Protocol is important to ensure your VPN connection has the most suitable encryption depending on your online usage. Following is a quick rundown of the various encryption methods VPN providers use:
- Point-to-Point Tunnel Protocol. Supported by most VPN providers, this is an obsolete and insecure protocol. While it doesn’t support encryption, it creates a Generic Routing Encapsulation (GRE) Tunnel between the two endpoints (client – server) and encapsulates all traffic inside the tunnel. Because of the encapsulation process PPTP can suffer from slow performance issues if there is not enough bandwidth available.
- L2TP / IPSec: Layer 2 Tunnel Protocol is considered the evolution of PPTP coupled with IPSec for encryption. It’s a highly secure protocol used by all VPN Service providers and manages to offer a high-level of confidentiality.
- SSTP – Secure Socket Tunnel Protocol: A fairly newer encryption protocol that relies on SSLv3/TLS for encryption which means SSTP is able to pass through most Firewalls and Proxy Servers using TCP port 443 (HTTPS). SSTP is supported by Microsoft Windows Vista SP1 and later plus RouterOS. As with most IP-tunnelled protocols, SSTP performance can be affected if there is not enough bandwidth available.
- OpenVPN: One of the latest VPN clients offering great security and flexibility. OpenVPN is maintained by the open-source community and relies on OpenSSL to provide encryption. OpenVPN can utilize both UDP and TCP protocols making it a highly desirable alternative to IPSec when it’s blocked. OpenVPN can support up to 256bit encryption and many vendors have implemented into their products e.g VPN Service Providers.
Additional Benefits of Using a VPN at Hotspots & Public Wifi Networks
As well as data protection, VPNs provide other benefits on public WiFi - Hotspots. Due to the nature of tunnelling, VPNs can be used to bypass content restrictions. This can be particularly useful on guest internet, which often has filtering policies in place.
They also give you some anonymity when connecting to the web. The website you’re connecting to sees your connection is coming from wherever the VPN Server is located, not your physical (real) location. Moreover, as all of your information is encrypted, the broadband service provider can’t spy on you either. This has the bonus of protection from surveillance by the government or other parties. For a journalist or lawyer, that can be essential.
However, not all VPNs are created equal. The protection your VPN hotspot provides depends largely on which of the above protocols they use and how the data is stored. Some VPN services keep a log of every site you visit and from which IP address. Naturally, that removes some degree of anonymity.
This is particularly relevant if they’re located in one of the so-called ‘five-eyes.’ The US, UK, Canada, Australia, and New Zealand all share the data from their intelligence agencies. In many cases, VPN providers must legally hand over user data to the government on request. The only way VPN hotspots can circumvent this is by not keeping logs at all. For someone just wanting to stay safe on public WiFi, that’s not much of a concern. If you’re looking for the full package, though, it’s worth looking up their policies.
Of course, some providers offer VPN functionality free of charge. Unfortunately, these are often subject to data caps, advertisements, or other money making methods. In some cases, free providers have sold user bandwidth or connection data. Though they’ll do in a pinch, free VPNs are no substitute for a paid service. If you go free, it’s best to do some research beforehand.
There’s also availability to consider. Most paid VPN Services support all the major devices and operating systems, such as Windows, OSX, Linux, iOS, Android and routers. That means you can be protected on all your devices, but not necessarily all at once. The limit of devices you can connect varies depending on provider, anywhere between 2 and 6. The majority support 4 or 5 devices, but this can change depending on your plan.
Despite this, it’s easy to get a VPN set up on any device. Though some don’t support less popular platforms like Windows 10 Mobile, it’s usually possible to set them up manually via a built-in settings menu.
For more obscure devices like a DS or PS Vita, or just to avoid setup, you can share your VPN connection from a PC. This essentially acts as a separate, VPN Hotspot, meaning you’ll have your own password-protected WiFi network that’s secure and encrypted. You can set one up on a Windows PC with the following steps or read our Windows WiFi Hotspot article:
- Connect your PC over Ethernet or WiFi
- Hit Start and type cmd and select Open command prompt as an administrator
- Type netsh wlan show driver
- Look for the network you’re connected to and check for the field Hosted network supported: Yes
- Type netsh wlan set hostednetwork mode=allow ssid=VPN hotspot key=MyP@$$!
- Type netsh wlan start hostednetwork
- Go to Control Panel>Network and Sharing Center and click Change adapter settings
- Find the relevant VPN adapter and click on Properties
- Go to the Sharing tab and tick Allow other network users to connect through this computer’s internet connection
- Start up your VPN and connect to the new VPN hotspot from any device
This is a good solution if you have multiple people in a hotel suite or café, and saves downloading an app on every device. For easier setup, you can download a tool like Virtual Router Manager. You’ll still need a compatible WiFi card, but you can set up the VPN hotspot in just a few seconds.
Another great solution for home or office environments is to configure your router to connect with your VPN Provider. A solution like this will allow you to cleverly share your VPN connection with all devices in your network without requiring to separately configure each one with a VPN client.
Summary
You can never be truly safe on Public or Guest WiFi. Whether you’re in a hotel, café or on a business guest network, a determined attacker may be able to find a way. Regardless of how safe you think you are, it’s always worth avoiding sensitive logins while on an unsecure connection.
If you have to, a VPN will significantly reduce the risk. For most attackers, it will be more hassle than it’s worth. Setting up a VPN hotspot can extend this protection to any device, so friends and family have little reason to be unsafe.
Naturally, VPNs aren’t infallible. Users still need to watch out for fake WiFi portals, which may launch in the time between connecting to a network and launching the VPN. This short window may also give the attacker information about your system or other clues to help them.
However, in combination with other measures, a VPN is possibly the best protection you’ll find. Without a VPN, hotspots just aren’t secure and, considering what’s on the line, $3 to $8 US a month for a fast & secure VPN service is a complete bargain.
Your IP address:
52.14.94.195
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!













