Acunetix Web Vulnerability Scanner
The biggest problem with testing web applications is scalability. With the addition of even a single form or page to test, you invariably increase the number of repetitive tasks you have to perform and the number of relationships you have to analyze to figure out whether you can identify a security issue.
As such, performing a security assessment without automation is an exercise in stupidity. One can use the lofty argument of the individual skill of the tester, and this is not to be discounted – I’ll come back to it – but, essentially, you can automate at least 80% of the task of assessing website security. This is part of the reason that security testing is becoming highly commoditized, the more you have to scan, the more repetitive tasks you have to perform. It is virtually impossible for a tester to manually analyze each and every single variable that needs to be tested. Even if it were so, to perform this iterative assessment manually would be foolishly time-consuming.
This problem, coupled with the explosive growth of web applications for business critical applications, has resulted in a large array of web application security testing products. How do you choose a product that is accurate (false positives are a key concern), safe (we’re testing important apps), fast (we come back the complexity point) and perhaps most importantly, meaningful in its analysis?
This implies that its description of the vulnerabilities discovered, and the measures to be taken to mitigate them, must be crystal clear. This is essentially what you’re paying for, it doesn’t matter how good the scanning engine is or how detailed their threat database is if the output – risk description and mitigation – are not properly handled. With these points in mind, we at Firewallcx, decided to take Acunetix’s Web Vulnerability Scanner for a spin.
I’ve had the pleasure of watching the evolution of web scanning tools, right from my own early scripting in PERL, to the days of Nikto and libwhisker, to application proxies, protocol fuzzers and the like. At the outset, let me say that Acunetix’s product has been built by people who have understood this evolution. The designers of the product have been around the block and know exactly what a professional security tester needs in a tool like this. While this puppy will do point ’n’ shoot scanning with a wizard for newbies, it has all the little things that make it a perfect assistant to the manual tester.
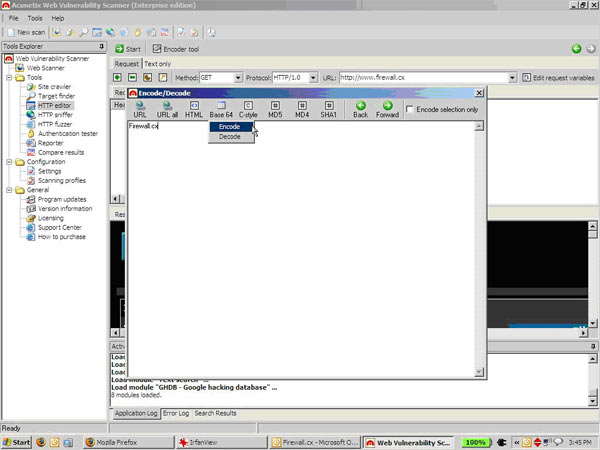
A simple example of ‘the small stuff’ is the extremely handy encoder tool that can handle text conversions and hashing in a jiffy. Anyone who’s had the displeasure of having to whip up a base-64 decoder or resort to md5sum to obtain a hash in the middle of a test will appreciate why this is so useful. More importantly, it shows that the folks at Acunetix know that a good tester will be analyzing the results and tweaking the inputs away from what the scanning engine would do. Essentially they give you the leeway to plug your own intellect into the tool.
Usage is extremely straightforward, hit the icon and you’ll get a quick loading interface that looks professional and displays information smartly (I appreciate the tabbed interfaces, these things matter as a badly designed UI could overwhelm you with more information than you need). Here’s a shot of the target selection wizard:
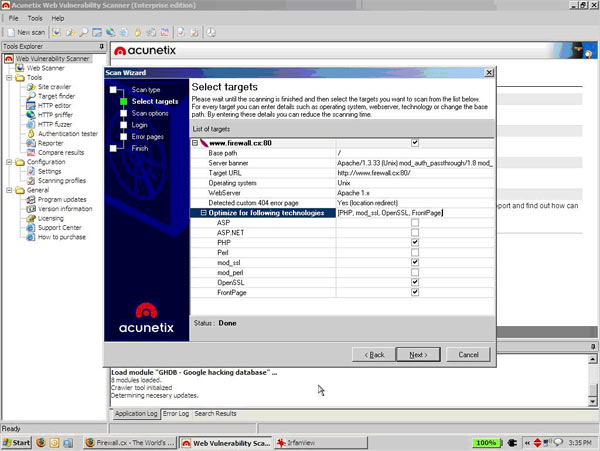
What I liked here was the ‘Optimize for the following technologies’ setup. Acunetix did a quick query of my target (our website, www.Firewall.cx) and identified PHP, mod_ssl, OpenSSL and FrontPage as modules that we’re using. When you’re going up against a blind target in a penetration test or setting up scans for 50 webapps at a time, this is something that you will really appreciate.
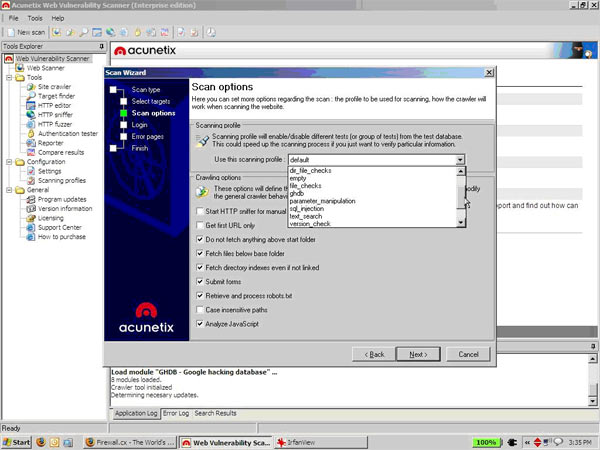
Next we come to the profile selection – which allows you to choose the scanning profile. Say I just want to look for SQL injection, I can pick that profile. You can use the profile editor to customize and choose your own checks. Standard stuff here. The profile and threat selection GUI is well categorized and it’s easy to find the checks you want to deselect or select.
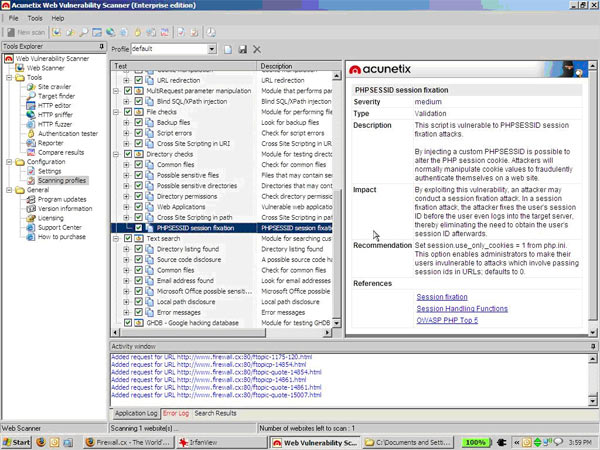
You can browse the threat database in detail as shown below:
At around this juncture, the tool identified that www.Firewall.cx uses non-standard (non-404) error pages. This is extremely important for the tool to do. If it cannot determine the correct ‘page not found’ page, it will start throwing false positives on every single 302 redirect. This is a major problem with scanners such as Nikto and is not to be overlooked. Acunetix walked me through the identification of a valid 404 page. Perhaps a slightly more detailed explanation as to why this is important would benefit a newbie.
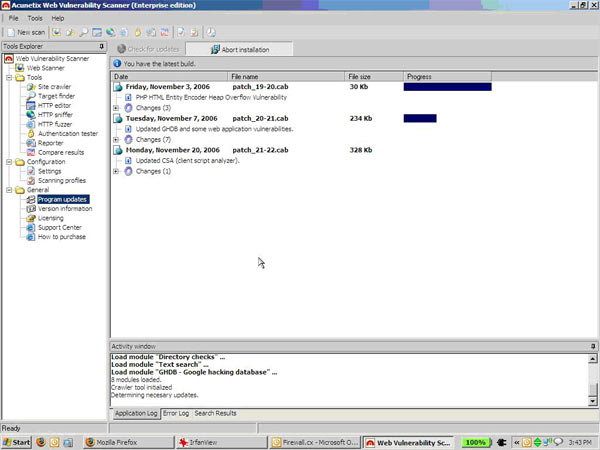
I had updated the tool before scanning, and saw the threat database being updated with some recent threats. I don’t know the threat update frequency, but the process was straightforward and, unlike many tools, didn’t require me to restart the tool with the new DB.
Since I was more interested in the ‘how can I help myself’ as opposed to ‘how can you help me’ approach to scanning, I fiddled with the fuzzer, request generator and authentication tester. These are very robust implementations, we have fully fledged tools implementing just this functionality and you should not be surprised to see more people discarding other tools and using Acunetix as a one-stop-shop toolbox.
One note though, the usernames dictionary for the authentication tester is far too limited out of the box (3-4 usernames), the password list was reasonably large, but the tool should include a default username list (where are things like ‘tomcat’, ‘frontpage’ etc?) so as not to give people a false sense of security. Given that weak password authentication is still one of the top reasons for a security breach, this module could use a reworking. I would like to see something more tweakable, along the lines of Brutus or Hydra’s HTTP authentication capabilities. Perhaps the ability to plug in a third party bruteforce tool would be nice.
Here I am playing with the HTTP editor:
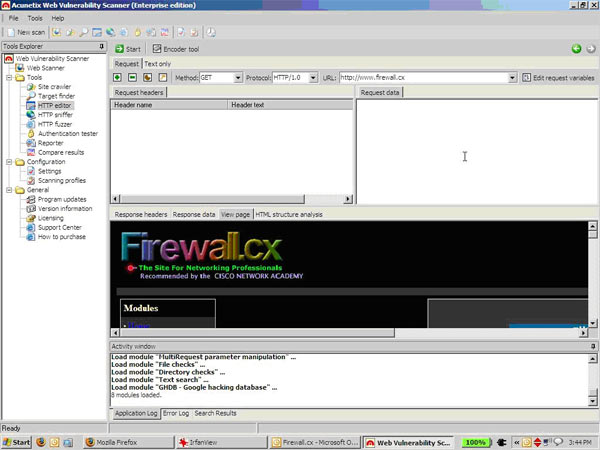
Here’s the neat little encoder utility that I was talking about earlier. You will not miss this one in the middle of a detailed test:
After being satisfied that this product could get me through the manual phase of my audits, I fell back on my tester’s laziness and hit the scan button while sipping a Red Bull.
The results arrive in real time and are browseable, which is far better than seeing a progress bar creep forward arbitrarily. While this may seem cosmetic, when you’re being pushed to deliver a report, you want to be able to keep testing manually in parallel. I was watching the results come in and using the HTTP editor to replicate the responses and judge what required my manual intervention.
Essentially, Acunetix chews through the application looking for potential flaws and lets you take over to verify them in parallel. This is absolutely the right approach and far more expensive tools that I’ve used do not realise this. Nobody with half smarts will rely purely on the output of a tool, a thorough audit will have the tester investigating concern areas on his own, if I have to wait for your tool to finish everything it does before I can even see those half-results, you’ve wasted my time.
Here’s how the scanning window looked:
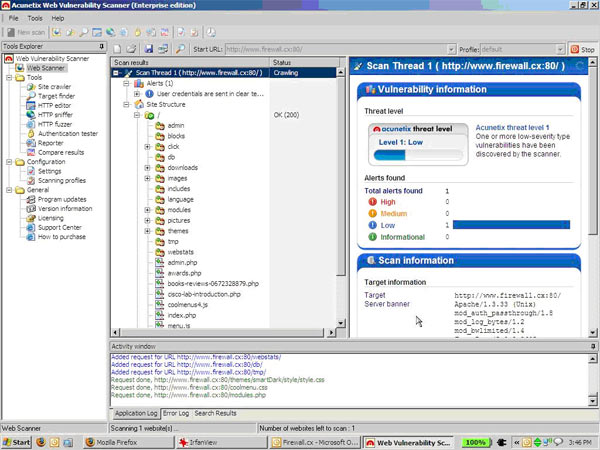
Now bear in mind that I was running this test over a 256kbps link on the Internet, I was expecting it to take time, especially given that Firewall.cx has an extremely large set of pages. Halfway through, I had to stop the test as it was bravely taking on the task of analyzing every single page in our forums. However, there was constant feedback through the activity window and my network interface, you don’t end up wondering whether the product has hung as is the case with many other products I’ve used.
The reporting features are pretty granular, allowing you to select the usual executive summary and detailed report options. Frankly, I like the way the results are presented and in the course of my audits never needed to generate a report from the tool itself. I’m certain that the features of the reporting module will more than suffice. The descriptions of the vulnerabilities are well written, the solutions are accurate and the links to more information come from authoritative sources. If you come back to what I said in the opening stages of this review, this is the most important information that a tool should look to provide. Nothing is more terrible than ambiguous results, and that is a problem you will not have with this product.
One drawback found with the product was the lack of a more complete scripting interface. Many testers would like the ability to add their own code to the scanning setup. I did check out the vulnerability editor feature, but would prefer something that gave me more flexibility. Another was the lack of a version for Linux / UNIX-like systems. The majority of security testers operate from these platforms and it would be nice not to have to switch to a virtual machine or deal with a dual boot configuration to be able to harness the power of this tool. Neither of these drawbacks are deal killers, and should be treated more as feature requests.
Other than that, I truly enjoyed using this product. Web application auditing can be a tedious and time consuming nightmare, and the best praise I can give Acunetix is that they’ve made a product that makes me feel a part of the test. The interactivity and levels of detail available to you give you the ability to be laid back or tinker with everything you want, while the test is still going on. With its features and reasonable pricing for a consultant’s license, this product is unmatched and will quickly become one of the premier tools in your arsenal.
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!














