Data Encapsulation & Decapsulation in the OSI Model
Here we are going to explain in detail how data travels through the OSI model. You must keep in mind that the OSI model is a guideline. It tells the computer what it's supposed to do when data needs to be sent or when data is received.
|
In order to make it easier for most, there is a movie file available which will show your exactly what we are about to analyse. Click here to to obtain the encap-decap movie (1MB). You will need Windows media player to view it.
|
Our Study Case
We are going to analyse an example in order to try and understand how data encapsulation and decapsulation works. This should make it easier for most people.
Try to see it this way :
When a car is built in a factory, one person doesn't do all the jobs, rather it's put into a production line and as the car moves through, each person will add different parts to it so when it comes to the end of the production line, it's complete and ready to be sent out to the dealer.
The same story applies for any data which needs to be sent from one computer to another. The OSI model which was created by the IEEE committee is to ensure that everyone follows these guidelines (just like the production line above) and therefore each computer will be able to communicate with every other computer, regardless of whether one computer is a Macintosh and the other is a PC.
One important piece of information to keep in mind is that data flows 2 ways in the OSI model, DOWN (data encapsulation) and UP (data decapsulation).
The picture below is an example of a simple data transfer between 2 computers and shows how the data is encapsulated and decapsulated:
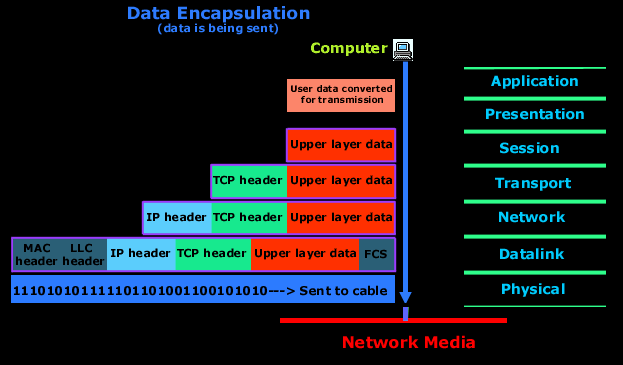
Explanation:
The computer in the above picture needs to send some data to another computer. The Application layer is where the user interface exists, here the user interacts with the application he or she is using, then this data is passed to the Presentation layer and then to the Session layer. These three layer add some extra information to the original data that came from the user and then passes it to the Transport layer. Here the data is broken into smaller pieces (one piece at a time transmitted) and the TCP header is a added. At this point, the data at the Transport layer is called a segment.
Each segment is sequenced so the data stream can be put back together on the receiving side exactly as transmitted. Each segment is then handed to the Network layer for network addressing (logical addressing) and routing through the internet network. At the Network layer, we call the data (which includes at this point the transport header and the upper layer information) a packet.
The Network layer add its IP header and then sends it off to the Datalink layer. Here we call the data (which includes the Network layer header, Transport layer header and upper layer information) a frame. The Datalink layer is responsible for taking packets from the Network layer and placing them on the network medium (cable). The Datalink layer encapsulates each packet in a frame which contains the hardware address (MAC) of the source and destination computer (host) and the LLC information which identifies to which protocol in the prevoius layer (Network layer) the packet should be passed when it arrives to its destination. Also, at the end, you will notice the FCS field which is the Frame Check Sequence. This is used for error checking and is also added at the end by the Datalink layer.
If the destination computer is on a remote network, then the frame is sent to the router or gateway to be routed to the desination. To put this frame on the network, it must be put into a digital signal. Since a frame is really a logical group of 1's and 0's, the Physical layer is responsible for encapsulating these digits into a digital signal which is read by devices on the same local network.
There are also a few 1's and 0's put at the begining of the frame, only so the receiving end can synchronize with the digital signal it will be receiving.
Below is a picture of what happens when the data is received at the destination computer.
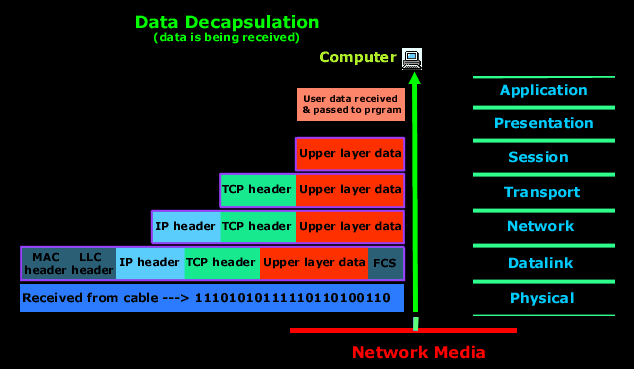
Explanation
The receiving computer will firstly synchronize with the digital signal by reading the few extra 1's and 0's as mentioned above. Once the synchonization is complete and it receives the whole frame and passes it to the layer above it which is the Datalink layer.
The Datalink layer will do a Cyclic Redundancy Check (CRC) on the frame. This is a computation which the comupter does and if the result it gets matches the value in the FCS field, then it assumes that the frame has been received without any errors. Once that's out of the way, the Datalink layer will strip off any information or header which was put on by the remote system's Datalink layer and pass the rest (now we are moving from the Datalink layer to the Network layer, so we call the data a packet) to the above layer which is the Network layer.
At the Network layer the IP address is checked and if it matches (with the machine's own IP address) then the Network layer header, or IP header if you like, is stripped off from the packet and the rest is passed to the above layer which is the Transport layer. Here the rest of the data is now called a segment.
The segment is processed at the Transport layer, which rebuilds the data stream (at this level on the sender's computer it was actually split into pieces so they can be transferred) and acknowledges to the transmitting computer that it received each piece. It is obvious that since we are sending an ACK back to the sender from this layer that we are using TCP and not UDP. Please refer to the Protocols section for more clarification. After all that, it then happily hands the data stream to the upper-layer application.
You will find that when analysing the way data travels from one computer to another most people never analyse in detail any layers above the Transport layer. This is because the whole process of getting data from one computer to another involves usually layers 1 to 4 (Physical to Transport) or layer 5 (Session) at the most, depending on the type of data.
Your IP address:
23.98.186.202
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!













