Suggested Articles:

OpManager - Network Monitoring & Management
Elevate your network management: Maximizing effic…
As technology evolves, so do our networks. Today's sprawling network infrastructures are intricate ecosystems, demanding more from IT teams than ever…
Network Protocol Analyzers
Improve Network Analysis Efficiency with Colasoft…
Troubleshooting network problems can be a very difficult and challenging task. While most IT engineers use a network analyzer to help solve network p…

ManageEngine Firewall Analyzer
7 Essential Firewall Management Strategies for Ma…
A firewall appliance is a fundamental pillar of network security, acting as the first line of defense against cyber threats. However, its strength…

OpManager - Network Monitoring & Management
Optimizing Cisco Router Performance: Best Practic…
Effective monitoring and management of Cisco routers and network devices are essential for ensuring a robust and efficient network infrastructure. In…
Featured Subcategories:
WireShark Articles:
How to Perform TCP SYN Flood DoS Attack & Detect…
This article will help you understand TCP SYN Flood Attacks, show how to perform a SYN Flood Attack (DoS attack) using Kali Linux & hping3 and co…
How to Detect SYN Flood Attacks with Capsa Networ…
This article explains how to detect a SYN Flood Attack using an advanced protocol analyser like Colasoft Capsa. We’ll show you how to identify and in…
Improve Network Analysis Efficiency with Colasoft…
Troubleshooting network problems can be a very difficult and challenging task. While most IT engineers use a network analyzer to help solve network p…
How To Detect ARP Attacks & ARP Flooding With Col…
ARP attacks and ARP flooding are common problems small and large networks are faced with. ARP attacks target specific hosts by using their MAC addres…
Your IP address:
18.217.164.190
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!
Palo Alto Networks
Palo Alto Networks Firewall - Web & CLI Initial Config…
This article is the second-part of our Palo Alto Networks Firewall technical articles. Our previous article was introduction to Palo Alto Networks Firewal…
Palo Alto Networks
Palo Alto Firewalls Security Zones – Tap Zone, Virtual…
Palo Alto Networks Next-Generation Firewalls rely on the concept of security zones in order to apply security policies. This means that access lists (fire…

Palo Alto Networks
Complete Guide: Configuring IPSec VPN between Palo Alt…
This article will show you how to configure an IPSec VPN tunnel between a Palo Alto firewall (all PANOS versions) and Meraki MX security appliance. Our co…
Palo Alto Networks
How to Fix Palo Alto Firewall “Error: Image File Authe…
Keeping your Palo Alto Firewall up to date with the latest PAN-OS software updates is an important step to ensure your organization is protected against t…
Windows Servers
How to Install and Configure Windows 2012 DNS Server R…
Our previous article covered introduction to the Domain Name System (DNS) and explained the importance of the DNS Server role within the network infrastru…
Windows Servers
Windows 2012 Server Foundation, Essential, Standard &…
FREE Hyper-V & VMware Virtualization Backup: FREE for Firewall.cx readers for a Limited Time! Download Now!
Windows Server 2012 Editions…
Windows Servers
Installing Active Directory Services & Domain Controll…
This article serves as an Active Directory tutorial covering installation and setup of Windows 2012 Active Directory Services Role & Domain Controller…
Windows Servers
Creating a Virtual Machine in Windows Hyper-V. Configu…
Our previous articles covered basic concepts of Virtualization along with the installation and monitoring of Windows 2012 Hyper-V. This article takes the…
Popular Topics
Virtualization & VM Backup
The Backup Bible. A Free Complete Guide to Disaster Re…
The Free Backup Bible Complete Edition written by backup expert and Microsoft MVP Eric Siron, is comprised of 200+ pages of actionable content divided int…

Network Fundamentals
Next-Gen Firewalls & Topologies. Designing & Building…
Next-generation firewalls (NGFWs) and DMZ zones are two critical components of network security that work hand in hand to protect an organization's networ…
Windows Servers
New Features in Windows Server 2012 - Why Upgrade to…
There is no doubt that Cloud Computing is hot topic these days. Innovations in cloud computing models have made every industry and company IT departments…
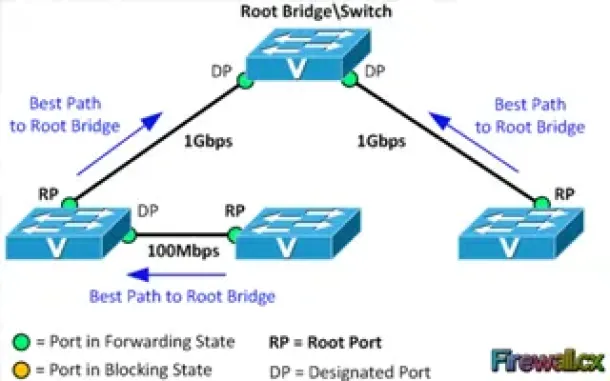
Spanning Tree Protocol (STP)
Spanning Tree Protocol – Part 2: Rapid STP Port Costs…
Spanning Tree Protocol, Rapid STP port costs and port states are an essential part of the STP algorithm that affect how STP decides to forward or block a…
Cisco Switches
Basic & Advanced Catalyst Layer 3 Switch Configuration…
This article covers basic and advanced configuration of Cisco Catalyst Layer-3 switches such as the Cisco Catalyst 3560G, 3560E, 3560-X, 3750, 3750E, 3750…
Cisco Routers
Configuring Cisco Dynamic Multipoint VPN (DMVPN) - Hub…
Our DMVPN Introduction article covered the DMVPN concept and deployment designs. We explained how DMVPN combines a number of technologies that give it its…
Cisco Routers
Configuring NAT Overload On A Cisco Router
NAT (Network Address Translation) is a method that allows the translation (modification) of IP addresses while packets/datagrams are traversing the networ…
Cisco CallManager-CCME
Free Cisco IP Phone & ATA Firmware (SCCP & SIP) Downl…
Firewall.cx readers can now download free Cisco firmware files for all Cisco IP Phones & Cisco ATA devices. Our new Cisco IP Phone & ATA Firmware…


















